The SpiKey attack: How to copy keys using sound
Por um escritor misterioso
Last updated 25 março 2025

The SpiKey attack: How one can copy a key using a phone recording of the sound of the clicks the key makes during insertion into a lock.

What is Malware? Malware Definition, Types and Protection

The Top 20 Security Predictions for 2020

The sound your keystrokes make is enough for AI to steal them — how to stay safe

The SpiKey attack: How to copy keys using sound

Three of the World's Most Expensive Phishing Attacks and How You Can Prevent Them - Wealth & Finance International

The Immortality Key

Behringer Groove Key, a Keystep Pro inspired groovebox and MIDI CV sequencer
Foley Sound Effects: The Ultimate Guide for Electronic Music Producers - EDMProd

Segmentation, trace denoising and spike extraction framework. (A) Mask

Trader Bets Big on Volatility Index (VIX) Spike Hours Before US Payrolls Data - Bloomberg
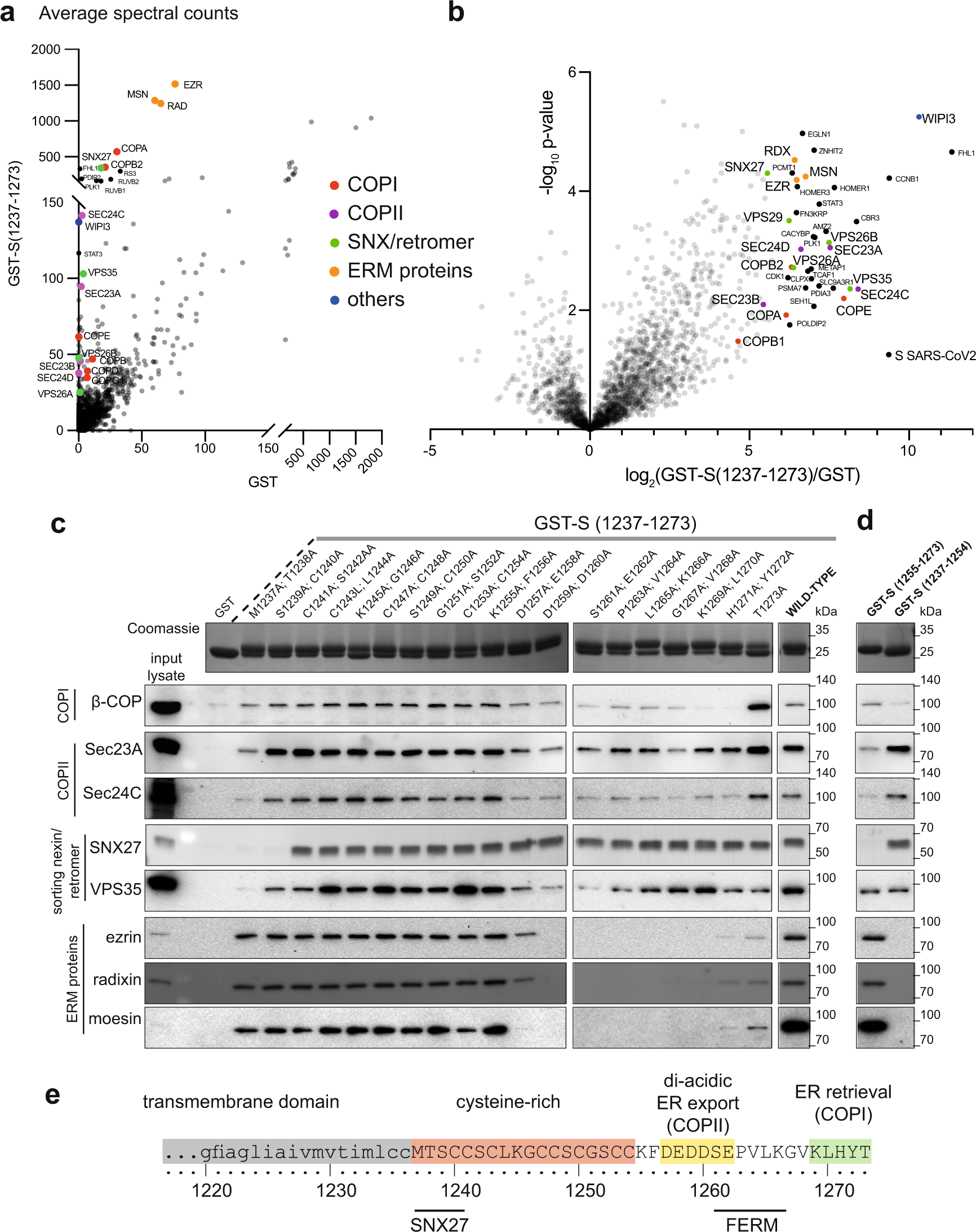
Sequences in the cytoplasmic tail of SARS-CoV-2 Spike facilitate expression at the cell surface and syncytia formation
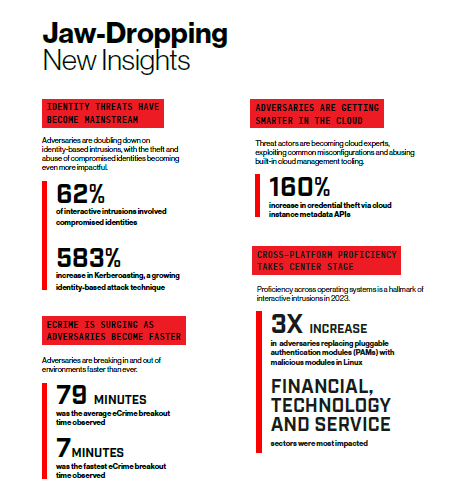
Identity-Based Attacks and Hands-on-Keyboard Activity on the Rise

Top 10 Noise Gate VST Plugins 2023 (+ 6 FREE Free Tools)
Recomendado para você
-
 Buy MX Keys S Keyboard - Full-Size25 março 2025
Buy MX Keys S Keyboard - Full-Size25 março 2025 -
 Kwikset 10119 4 CUT KEYS SmartKey Kit25 março 2025
Kwikset 10119 4 CUT KEYS SmartKey Kit25 março 2025 -
 CompX Chicago 1250 - 1499 Keys25 março 2025
CompX Chicago 1250 - 1499 Keys25 março 2025 -
 Keys - Locks and Tools Ltd - Dartford Locksmiths25 março 2025
Keys - Locks and Tools Ltd - Dartford Locksmiths25 março 2025 -
 Lost Keys & Lockouts25 março 2025
Lost Keys & Lockouts25 março 2025 -
 What's on your key ring? When is it too many?25 março 2025
What's on your key ring? When is it too many?25 março 2025 -
 Can You Recycle Keys? - Everyday Recycler25 março 2025
Can You Recycle Keys? - Everyday Recycler25 março 2025 -
 Key - Lockwiki25 março 2025
Key - Lockwiki25 março 2025 -
 Wicked Keys25 março 2025
Wicked Keys25 março 2025 -
 Get key copies that work at McGuire Lock25 março 2025
Get key copies that work at McGuire Lock25 março 2025
você pode gostar
-
 Buy The Crew 2 Standard Edition for PC25 março 2025
Buy The Crew 2 Standard Edition for PC25 março 2025 -
 Doors Department of Energy25 março 2025
Doors Department of Energy25 março 2025 -
 Equipamento kit SAT fiscal completo Elgrin - Equipamentos e mobiliário - Vila Costa e Silva, Campinas 125273918525 março 2025
Equipamento kit SAT fiscal completo Elgrin - Equipamentos e mobiliário - Vila Costa e Silva, Campinas 125273918525 março 2025 -
 Taylor Swift – End Game Lyrics25 março 2025
Taylor Swift – End Game Lyrics25 março 2025 -
 Sono Bisque Doll wa Koi wo Suru - Anime Icon by ZetaEwigkeit on25 março 2025
Sono Bisque Doll wa Koi wo Suru - Anime Icon by ZetaEwigkeit on25 março 2025 -
 Fone Ouvido Headphone Orelha Gato Bluetooth Dobravel Led Anúncio com variação - E_IDEIAS ONLINE25 março 2025
Fone Ouvido Headphone Orelha Gato Bluetooth Dobravel Led Anúncio com variação - E_IDEIAS ONLINE25 março 2025 -
SMART Denny25 março 2025
-
 Anime One Piece GK Sun God Nika Gear 5 Monkey D Luffy VS Kaido Dragon Fighting PVC Action Figures Collection Model Toys Gifts25 março 2025
Anime One Piece GK Sun God Nika Gear 5 Monkey D Luffy VS Kaido Dragon Fighting PVC Action Figures Collection Model Toys Gifts25 março 2025 -
 Melhores Palpites jogos de hoje - Palpites de Futebol para hoje25 março 2025
Melhores Palpites jogos de hoje - Palpites de Futebol para hoje25 março 2025 -
 Anime dragon ball z gohan batalha célula figura dbz filho gohan super saiyan 2 goku vegeta buu modelo boneca presente brinquedo 23cm25 março 2025
Anime dragon ball z gohan batalha célula figura dbz filho gohan super saiyan 2 goku vegeta buu modelo boneca presente brinquedo 23cm25 março 2025
