LetsDefend on X: Top 100 Reused Passwords / X
Por um escritor misterioso
Last updated 07 janeiro 2025


Cyber Security Interview Q&A - DETECTX

Abdul Malik Mohammed on LinkedIn: Introduction to 802.1x with EAP-TLS
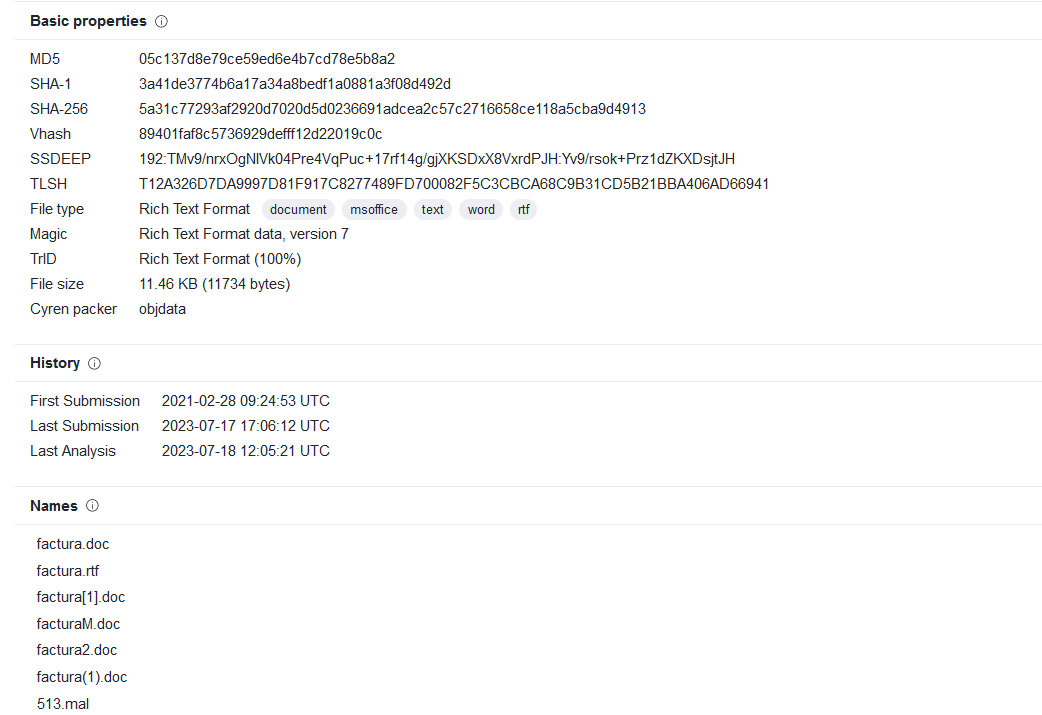
letsdefend.io challenge — Malicious Doc, by Enes Adışen

Expanding digital forensics education with artifact curation and scalable, accessible exercises via the Artifact Genome Project - ScienceDirect

Cyber Security Interview Q&A - DETECTX
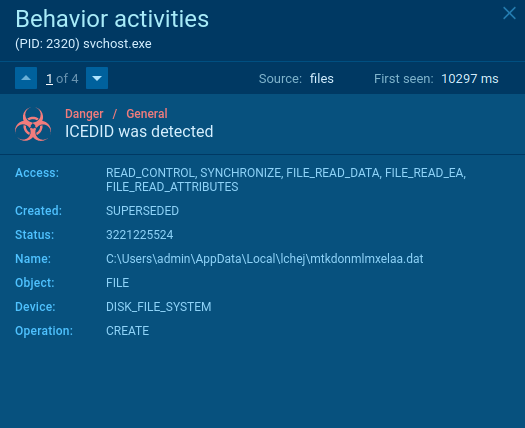
IcedID Malware Analysis, Overview by

OWASP Top 10, TryHackMe Writeup. This document delves into the OWASP Top…, by Lixin Zhang, Oct, 2023

SOC144 EventID:91 — New scheduled task created — letsdefend.io, by Enes Adışen

Account Takeover & Analysis of Brute Force Style Tools, by Lounge Fly

letsdefend.io challenge — Malicious Doc, by Enes Adışen

LetsDefend - Blue Team Training Platform
crzybkr46 (@crzybkr46) / X

LetsDefend's Malware Analysis: Suspicious Browser Extension Walk-Through - Cyber Gladius
Recomendado para você
-
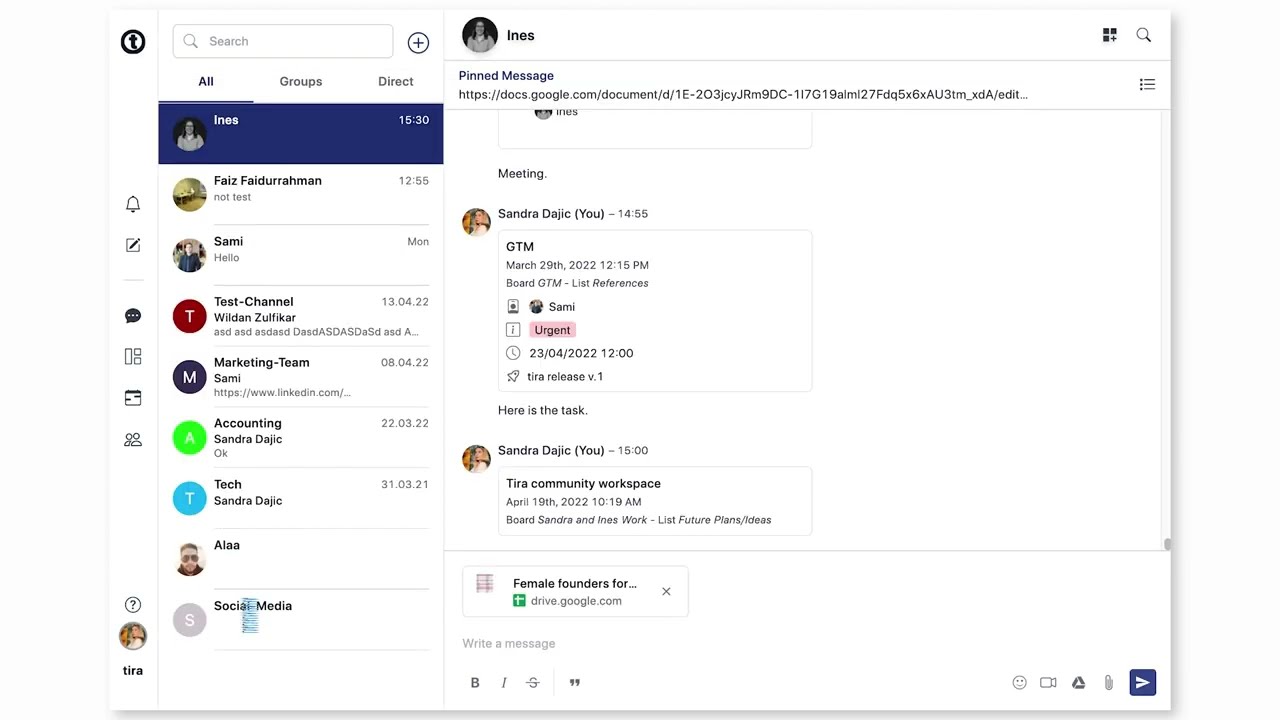 How to share Google Drive files to a chat07 janeiro 2025
How to share Google Drive files to a chat07 janeiro 2025 -
asdasd - Google My Maps07 janeiro 2025
-
 How to Upload Video to Google Drive EASILY - BizCrown Media Digital Marketing07 janeiro 2025
How to Upload Video to Google Drive EASILY - BizCrown Media Digital Marketing07 janeiro 2025 -
 asdasd (2) (2).png07 janeiro 2025
asdasd (2) (2).png07 janeiro 2025 -
 asd El blog feliz07 janeiro 2025
asd El blog feliz07 janeiro 2025 -
 How To: Shopify Recipes on Google with Rich Schema Data07 janeiro 2025
How To: Shopify Recipes on Google with Rich Schema Data07 janeiro 2025 -
asdas - Google My Maps07 janeiro 2025
-
 asdasdsa - Edwinius - Medium07 janeiro 2025
asdasdsa - Edwinius - Medium07 janeiro 2025 -
 Acast Launches Platform to Get Brands Running Podcast Ads07 janeiro 2025
Acast Launches Platform to Get Brands Running Podcast Ads07 janeiro 2025 -
 Contact Us Kinderland Child Care07 janeiro 2025
Contact Us Kinderland Child Care07 janeiro 2025
você pode gostar
-
 File:TataSteelChess2020-21.jpg - Wikipedia07 janeiro 2025
File:TataSteelChess2020-21.jpg - Wikipedia07 janeiro 2025 -
 livro - O Significado Sexual do Taro - Theodor Laurence07 janeiro 2025
livro - O Significado Sexual do Taro - Theodor Laurence07 janeiro 2025 -
 King Dice by Snow-Jackalope on DeviantArt07 janeiro 2025
King Dice by Snow-Jackalope on DeviantArt07 janeiro 2025 -
 Cabeça de tigre no logotipo do símbolo de fogo no fundo branco vetor de estêncil de tatuagem tribal de animais selvagens07 janeiro 2025
Cabeça de tigre no logotipo do símbolo de fogo no fundo branco vetor de estêncil de tatuagem tribal de animais selvagens07 janeiro 2025 -
Steam Workshop::TITANFALL: ADDENDUM [WOTC]07 janeiro 2025
-
nome do cronômetro no subway surf pc|TikTok Search07 janeiro 2025
-
![Attorney Online: Reboot [2.1.6] : Games](http://i.imgur.com/i2zF936.png) Attorney Online: Reboot [2.1.6] : Games07 janeiro 2025
Attorney Online: Reboot [2.1.6] : Games07 janeiro 2025 -
 How to Recover Hacked Free Fire Account?07 janeiro 2025
How to Recover Hacked Free Fire Account?07 janeiro 2025 -
 Scp 1080P, 2K, 4K, 5K HD wallpapers free download07 janeiro 2025
Scp 1080P, 2K, 4K, 5K HD wallpapers free download07 janeiro 2025 -
KuPS x Derry City 03/08/2023 – Palpite dos Jogo, Futebol07 janeiro 2025
![Steam Workshop::TITANFALL: ADDENDUM [WOTC]](https://steamuserimages-a.akamaihd.net/ugc/860610549951206980/F0DB3011483A201AA3B25D14D1079049EFC20EE8/?imw=637&imh=358&ima=fit&impolicy=Letterbox&imcolor=%23000000&letterbox=true)

