How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 01 janeiro 2025
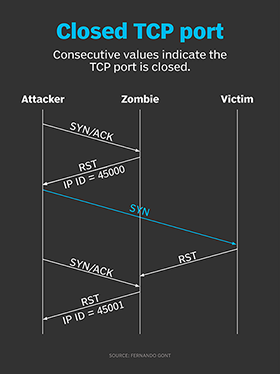
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
What Is a Port Scan Attack? Definition and Prevention Measures for Enterprises

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan
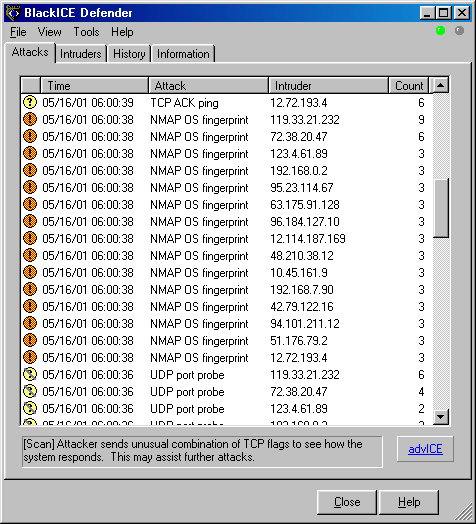
Subverting Intrusion Detection Systems
Port Scanning based Attacks
Nmap - Best Network Monitor and Port Scanner Tool - GBHackers
What Is Nmap? A Comprehensive Tutorial For Network Mapping
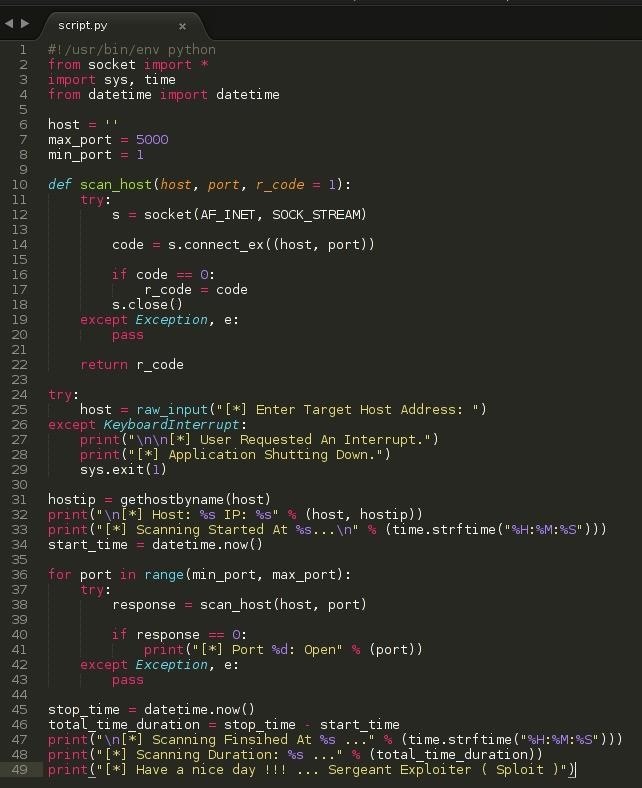
SPLOIT: How to Make a Python Port Scanner « Null Byte :: WonderHowTo

PPT - Port Scanning PowerPoint Presentation, free download - ID:1577632

PDF) TCP Idle Scanning using network printers
Recomendado para você
-
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack01 janeiro 2025
-
 How to Bypass Internet Censorship01 janeiro 2025
How to Bypass Internet Censorship01 janeiro 2025 -
 Cyber portfolio01 janeiro 2025
Cyber portfolio01 janeiro 2025 -
![Zscaler- Source IP Anchoring [SIPA]](https://i.ytimg.com/vi/ylt74TZnS2Q/hq720.jpg?sqp=-oaymwE7CK4FEIIDSFryq4qpAy0IARUAAAAAGAElAADIQj0AgKJD8AEB-AH-CIAC0AWKAgwIABABGDwgEyh_MA8=&rs=AOn4CLAOEq5hhRYj-Kw0ehVImE5Q4ZxLDQ) Zscaler- Source IP Anchoring [SIPA]01 janeiro 2025
Zscaler- Source IP Anchoring [SIPA]01 janeiro 2025 -
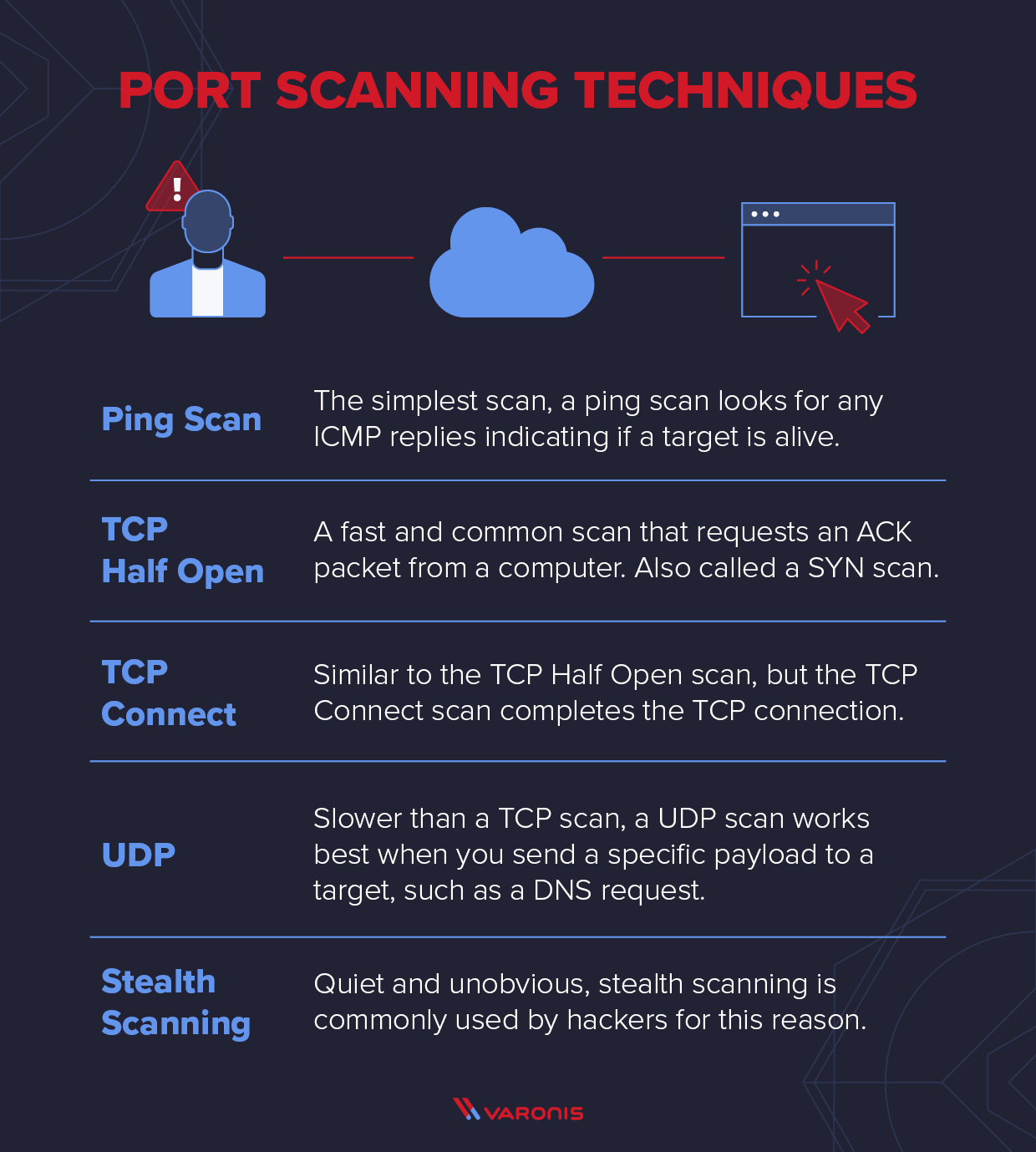 Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi01 janeiro 2025
Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi01 janeiro 2025 -
 Port Scan in Ethical Hacking - GeeksforGeeks01 janeiro 2025
Port Scan in Ethical Hacking - GeeksforGeeks01 janeiro 2025 -
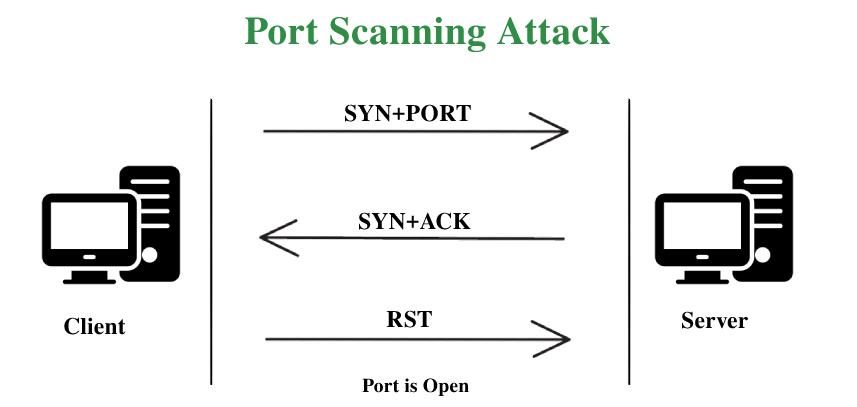 Port Scanning Attack - GeeksforGeeks01 janeiro 2025
Port Scanning Attack - GeeksforGeeks01 janeiro 2025 -
Wireshark: Port-Scanning Download Scientific Diagram01 janeiro 2025
-
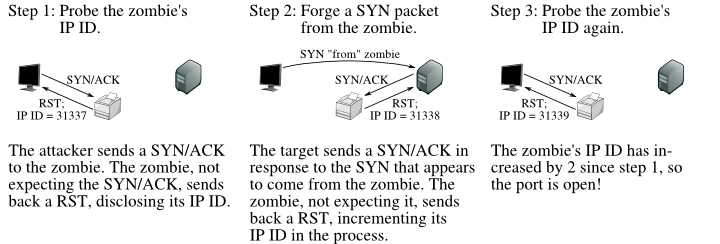 TCP Idle Scan (-sI) Nmap Network Scanning01 janeiro 2025
TCP Idle Scan (-sI) Nmap Network Scanning01 janeiro 2025 -
 Fortigate, TravelingPacket - A blog of network musings01 janeiro 2025
Fortigate, TravelingPacket - A blog of network musings01 janeiro 2025
você pode gostar
-
 Shadow the Hedgehog (Japanese Edition) Poster for Sale by PLUS-ULTRAS01 janeiro 2025
Shadow the Hedgehog (Japanese Edition) Poster for Sale by PLUS-ULTRAS01 janeiro 2025 -
 Mashle: Magic and Muscles Episode 1 Explained in Hindi01 janeiro 2025
Mashle: Magic and Muscles Episode 1 Explained in Hindi01 janeiro 2025 -
 FIFA 22 (Código Descarga) Xbox One, Series X, S - Catalogo01 janeiro 2025
FIFA 22 (Código Descarga) Xbox One, Series X, S - Catalogo01 janeiro 2025 -
 A Sato Company está em negociações para trazer o filme de My Hero01 janeiro 2025
A Sato Company está em negociações para trazer o filme de My Hero01 janeiro 2025 -
 Como Jogar na XBOX LIVE com Xbox 360 RGH.01 janeiro 2025
Como Jogar na XBOX LIVE com Xbox 360 RGH.01 janeiro 2025 -
como jogar versao antiga do subway surf no iphone|TikTok Search01 janeiro 2025
-
 Divertido Jumping Jogos de Macaco Festa da Família Lazer pai-filho01 janeiro 2025
Divertido Jumping Jogos de Macaco Festa da Família Lazer pai-filho01 janeiro 2025 -
CONVIDADOS INDESEJADOS está entre nós! E ele é bom demais! Esse é um j01 janeiro 2025
-
 Head Football League: Head Soccer, Head Ball Game Game for Android01 janeiro 2025
Head Football League: Head Soccer, Head Ball Game Game for Android01 janeiro 2025 -
 Assassin's Creed 3 / Lorne Balfe - Connor's Life (Track 08)01 janeiro 2025
Assassin's Creed 3 / Lorne Balfe - Connor's Life (Track 08)01 janeiro 2025

