Lone-Actor Terrorism: Policy Paper 2: Attack Methodology and Logistics
Por um escritor misterioso
Last updated 16 julho 2024


Hackers use a new technique in malspam campaigns to disable Macro security warnings in weaponized docs
Semiconductors and the U.S.-China Innovation Race – Foreign Policy
European Cyber Defence Policy
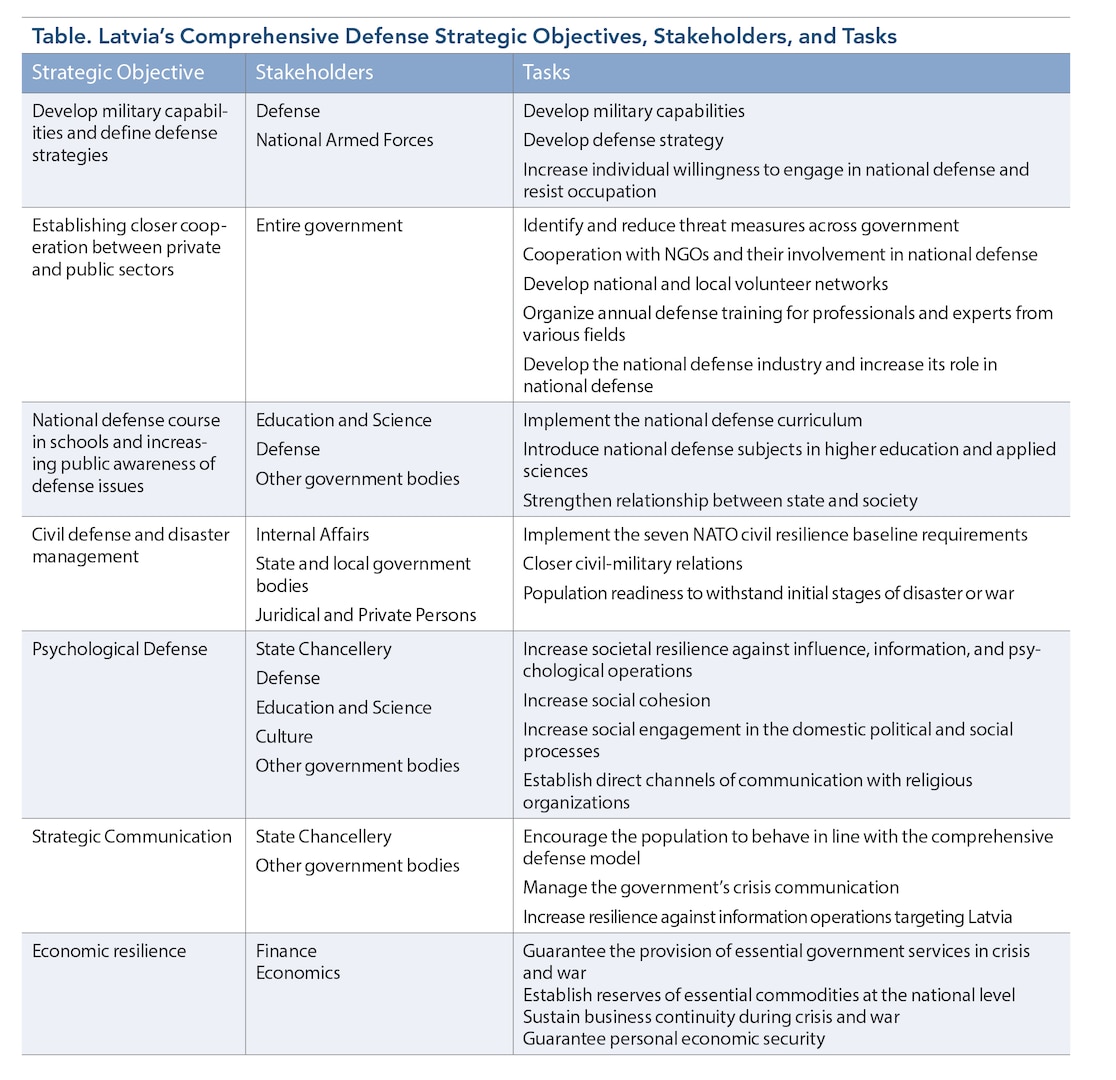
Latvia: From Total Defense to Comprehensive Defense > National Defense University Press > News Article View

A View from the CT Foxhole: Randall Blake, Former National Intelligence Officer for Transnational Threats, National Intelligence Council – Combating Terrorism Center at West Point

Lone-Actor Terrorism Royal United Services Institute

Avoiding a Long War: U.S. Policy and the Trajectory of the Russia-Ukraine Conflict

Mercenaries and War: Understanding Private Armies Today > National Defense University Press > News

EvilProxy used in massive cloud account takeover scheme

Wargaming to find a safe port in a cyber storm - Atlantic Council

Full article: An exploratory analysis of leakage warning behavior in lone-actor terrorists
tm239600-23_424b4alt - none - 24.7188496s
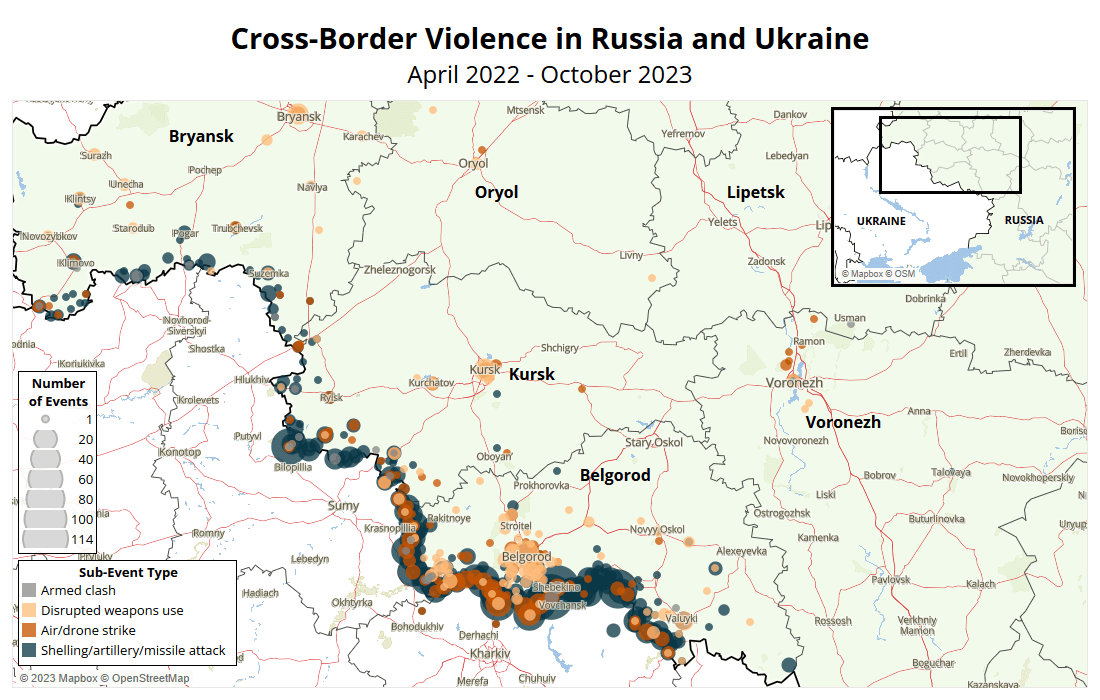
Importing Instability: How the War Against Ukraine Makes Russia Less Secure
Recomendado para você
-
 Paper.io 2 World Conflict16 julho 2024
Paper.io 2 World Conflict16 julho 2024 -
 PAPER IO World Conflict - UnBlocked16 julho 2024
PAPER IO World Conflict - UnBlocked16 julho 2024 -
 Paper.io 2 World Conflict16 julho 2024
Paper.io 2 World Conflict16 julho 2024 -
Paper.IO world Conflict on Vimeo16 julho 2024
-
 World Conflict in 03:47.233 by Vinny121 - Paper.io 2 - Speedrun16 julho 2024
World Conflict in 03:47.233 by Vinny121 - Paper.io 2 - Speedrun16 julho 2024 -
Paper - Io 2 World Conflict16 julho 2024
-
 Paper.io 2 World Conflict, New mode ''Teams16 julho 2024
Paper.io 2 World Conflict, New mode ''Teams16 julho 2024 -
 Paper.IO 2 Unblocked At School In 202316 julho 2024
Paper.IO 2 Unblocked At School In 202316 julho 2024 -
 What a third world war would mean for investors16 julho 2024
What a third world war would mean for investors16 julho 2024 -
Paper io 216 julho 2024
você pode gostar
-
 Code Vein: Lord Of Thunder on PS4 — price history, screenshots, discounts • USA16 julho 2024
Code Vein: Lord Of Thunder on PS4 — price history, screenshots, discounts • USA16 julho 2024 -
 Wallpaper : Tracer Overwatch, Video Game Art, seymour 3250x1828 - Ben10ash - 1959677 - HD Wallpapers - WallHere16 julho 2024
Wallpaper : Tracer Overwatch, Video Game Art, seymour 3250x1828 - Ben10ash - 1959677 - HD Wallpapers - WallHere16 julho 2024 -
 MotoGP™ Race Highlights 👊16 julho 2024
MotoGP™ Race Highlights 👊16 julho 2024 -
 Mega Cube: 2048 3D Merge Game Game for Android - Download16 julho 2024
Mega Cube: 2048 3D Merge Game Game for Android - Download16 julho 2024 -
 Butterfly Click Test blog - butterfly-click-test - ModDB16 julho 2024
Butterfly Click Test blog - butterfly-click-test - ModDB16 julho 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2023/i/0/BSMzhFSMmkeAzNRrfusQ/loud.jpg) Valorant Champions 2023: resumo da fase de grupos e tudo sobre os16 julho 2024
Valorant Champions 2023: resumo da fase de grupos e tudo sobre os16 julho 2024 -
 Illustration Of A Cartoon Red Gummy Bear Made Of Fruity Strawberry Jelly Candy Suitable For Babies Vector, Variety, Caramel, Color PNG and Vector with Transparent Background for Free Download16 julho 2024
Illustration Of A Cartoon Red Gummy Bear Made Of Fruity Strawberry Jelly Candy Suitable For Babies Vector, Variety, Caramel, Color PNG and Vector with Transparent Background for Free Download16 julho 2024 -
 One Piece Film Z still going strong: Box office total as of 20 January approaches $73 Million : r/OnePiece16 julho 2024
One Piece Film Z still going strong: Box office total as of 20 January approaches $73 Million : r/OnePiece16 julho 2024 -
 Solid Platinum Liquid Full Silicone Reborn Baby Dolls - Vacos Store – vacos16 julho 2024
Solid Platinum Liquid Full Silicone Reborn Baby Dolls - Vacos Store – vacos16 julho 2024 -
 The Gilded Age, Teaser16 julho 2024
The Gilded Age, Teaser16 julho 2024

