Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download
Por um escritor misterioso
Last updated 31 março 2025
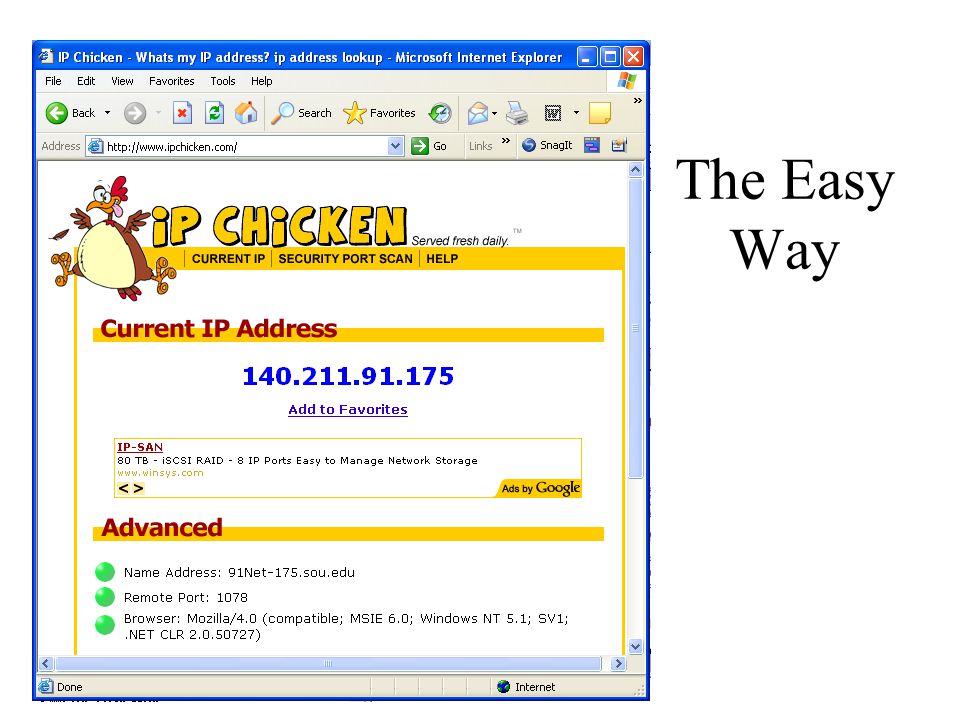
Phishing utilizing social engineering Induces the recipient to reveal desired personal information Bank account SSN Address Etc. Sometimes entices the recipient to go to a malicious web site
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the

Phishing URL Detection with ML. Phishing is a form of fraud in

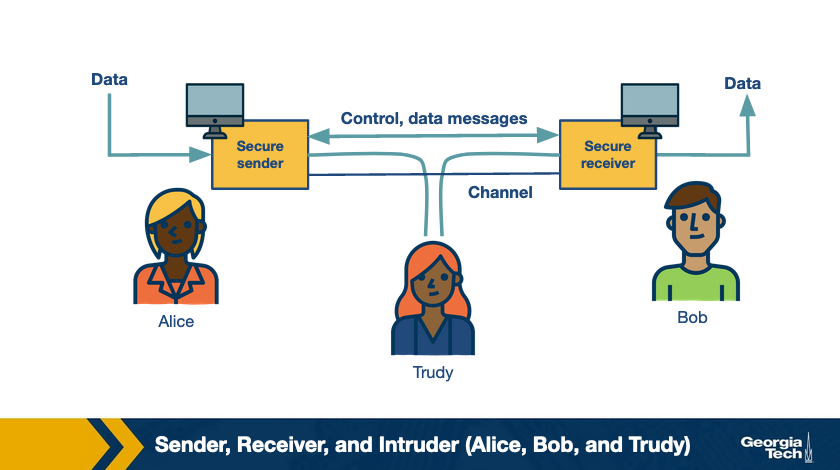
What Is Domain Name System (DNS)?
Internet Security - OMSCS Notes

Phishing Attacks And Strategies To Mitigate Them Powerpoint
.png)
The Ultimate Cybersecurity Glossary of Terms

Email - Wikipedia

6 Common Phishing Attacks and How to Protect Against Them
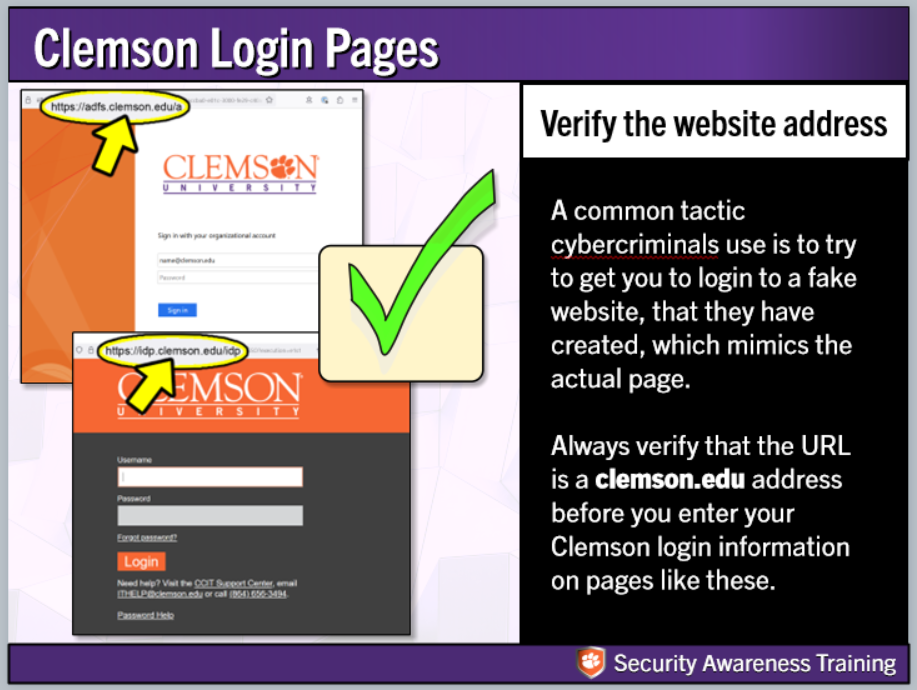
Cybersecurity Alerts

The COVID‐19 scamdemic: A survey of phishing attacks and their

Web Filtering Blog

Phishing Attacks And Strategies To Mitigate Them Powerpoint

Web Filtering Blog

Understanding Types of Cyber Attacks Training Ppt

PPT - Chapter 30 PowerPoint Presentation, free download - ID:9566444

What Is Phishing? - Definition, Types of Attacks & More
Recomendado para você
-
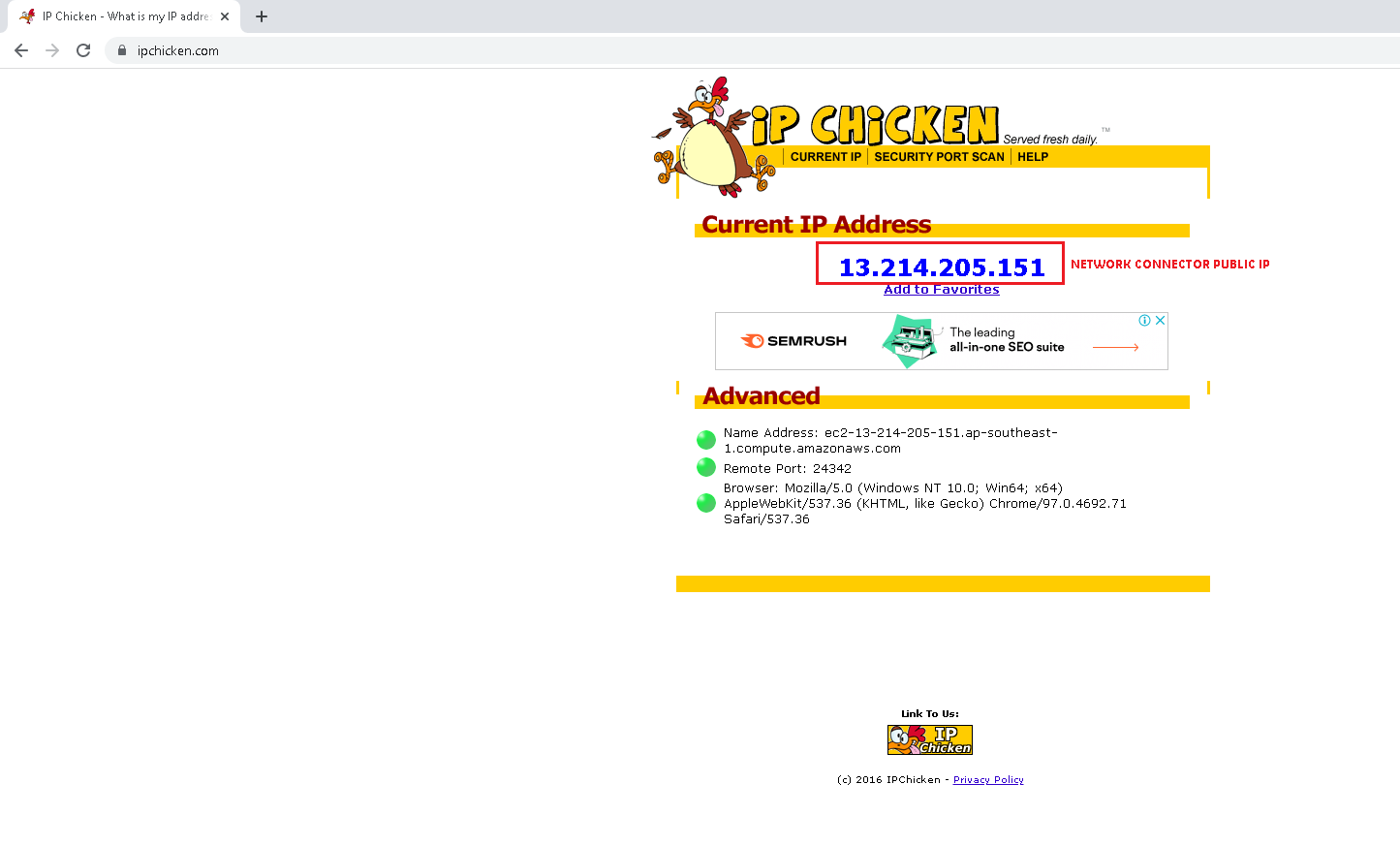 CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center31 março 2025
CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center31 março 2025 -
 like ip chicken 🐔🐔🐔 Ip chicken, Smart city, Coding31 março 2025
like ip chicken 🐔🐔🐔 Ip chicken, Smart city, Coding31 março 2025 -
 Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K31 março 2025
Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K31 março 2025 -
 Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community31 março 2025
Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community31 março 2025 -
![CGNAT: A Complete Guide to Carrier-Grade NAT [2023] — RapidSeedbox](https://www.rapidseedbox.com/wp-content/uploads/CGNAT_03.png) CGNAT: A Complete Guide to Carrier-Grade NAT [2023] — RapidSeedbox31 março 2025
CGNAT: A Complete Guide to Carrier-Grade NAT [2023] — RapidSeedbox31 março 2025 -
174.218.138.250 is a publicly routable IP address is it not?31 março 2025
-
 Port Scanner - an overview31 março 2025
Port Scanner - an overview31 março 2025 -
 Configuring private V2Ray server for bypassing internet censorship (TLS configuration)31 março 2025
Configuring private V2Ray server for bypassing internet censorship (TLS configuration)31 março 2025 -
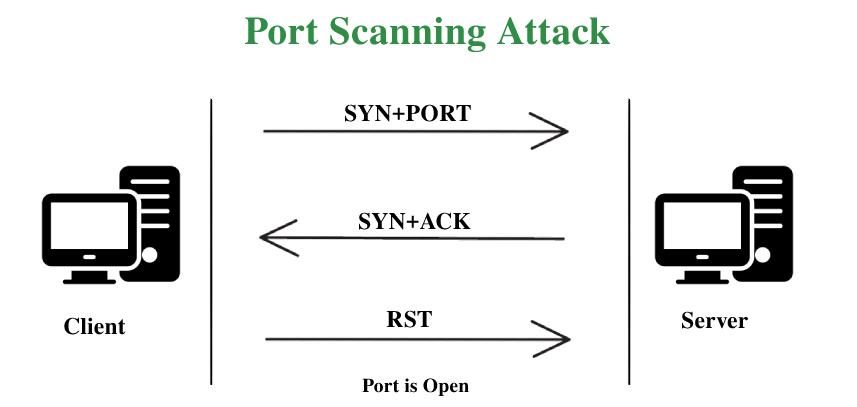 Port Scanning Attack - GeeksforGeeks31 março 2025
Port Scanning Attack - GeeksforGeeks31 março 2025 -
Gogo's T-Mobile sponsored in-flight wifi? Free? On a PC?!31 março 2025
você pode gostar
-
 Octoling doing the JoJo pose : r/splatoon31 março 2025
Octoling doing the JoJo pose : r/splatoon31 março 2025 -
 ESTRATÉGIA PRA SUBIR BANCA DE 30 REAIS NO MINES - JOGO DA MINA DA SORTE31 março 2025
ESTRATÉGIA PRA SUBIR BANCA DE 30 REAIS NO MINES - JOGO DA MINA DA SORTE31 março 2025 -
 Pokémon Scarlet and Violet Version-Exclusives31 março 2025
Pokémon Scarlet and Violet Version-Exclusives31 março 2025 -
 one piece wano arc nami Mangá one piece, Anime, One piece31 março 2025
one piece wano arc nami Mangá one piece, Anime, One piece31 março 2025 -
 Pokémon GO on X: Trainers, limited-time holiday packs will be available in the Pokémon GO in-game shop from December 25, 2016, to January 3, 2017 PST. / X31 março 2025
Pokémon GO on X: Trainers, limited-time holiday packs will be available in the Pokémon GO in-game shop from December 25, 2016, to January 3, 2017 PST. / X31 março 2025 -
 Street Fighter II - Guile Personagens street fighter, Street fighter, Desenho masculino31 março 2025
Street Fighter II - Guile Personagens street fighter, Street fighter, Desenho masculino31 março 2025 -
 Attack on Titan Temporada 4 Parte 2 Episódio 3 Data de lançamento confirmada - BR Atsit31 março 2025
Attack on Titan Temporada 4 Parte 2 Episódio 3 Data de lançamento confirmada - BR Atsit31 março 2025 -
 National Pokedex Complete: #001 - #718 by AustralAnima on DeviantArt31 março 2025
National Pokedex Complete: #001 - #718 by AustralAnima on DeviantArt31 março 2025 -
 Angels of Death Satsuriku No Tenshi Zack Isaac Foster Rachel Gardner Poster 331 março 2025
Angels of Death Satsuriku No Tenshi Zack Isaac Foster Rachel Gardner Poster 331 março 2025 -
 Rarity Factory Tycoon Codes Wiki for December 2023 - MrGuider31 março 2025
Rarity Factory Tycoon Codes Wiki for December 2023 - MrGuider31 março 2025
