Profiler 2.8 – Windows Memory Forensics – Cerbero Blog
Por um escritor misterioso
Last updated 14 março 2025
Memory Forensics - GrrCon2015 CTF

Memory Forensics Windows - Assistenza Tecnica Web
Support Blumira

Securing your Cloud Environment
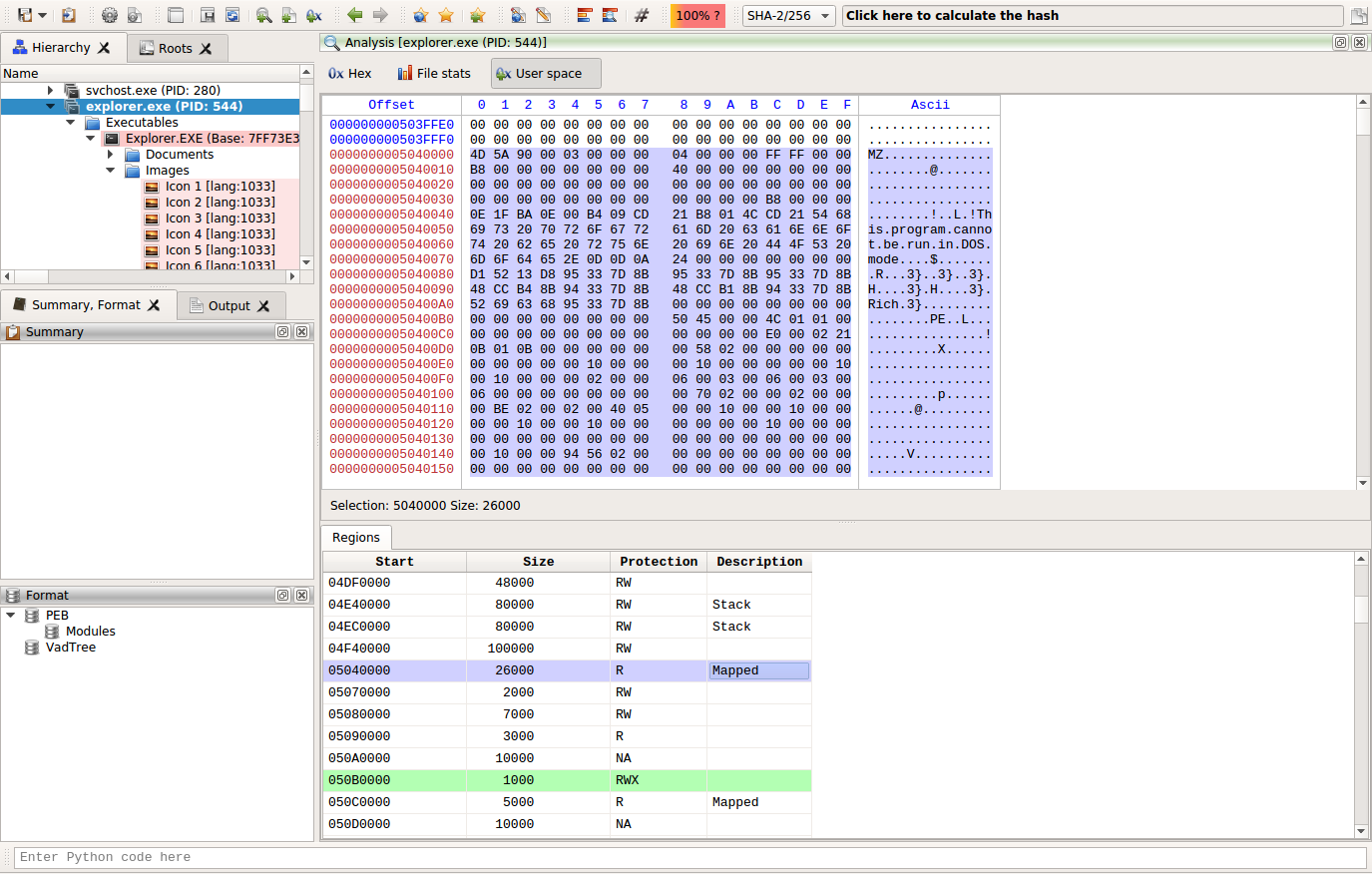
Profiler 2.8 – Windows Memory Forensics – Cerbero Blog

Memory Forensics - GrrCon2015 CTF

Books: shareholder value

Volatility Forensic Analysis: R2D2 Malware - Volatility, Memory Forensics, Malware

Core Impact System Requirements

Memory Forensics - GrrCon2015 CTF
Forgot android password
SharkBot: a “new” generation Android banking Trojan being distributed on Google Play Store, NCC Group Research Blog
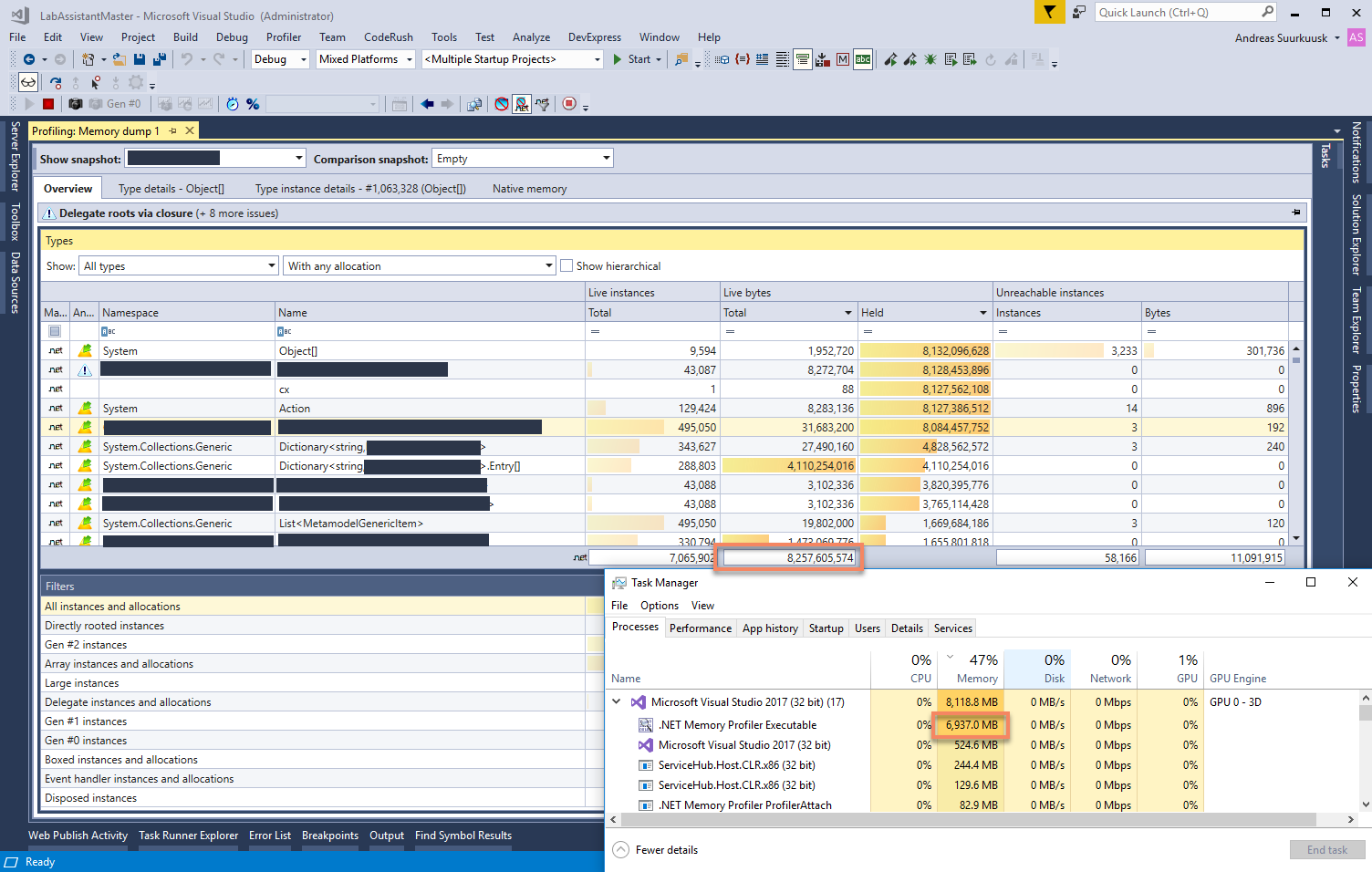
NET Memory Profiler Features

Top 12 Computer Forensics Tools
Is it possible to install cell phone spy software from a remote location? Is it just a myth? - Quora
Recomendado para você
-
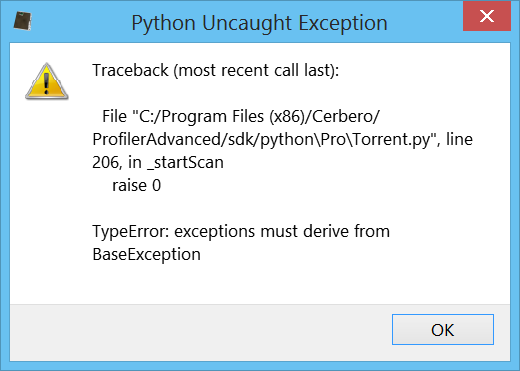
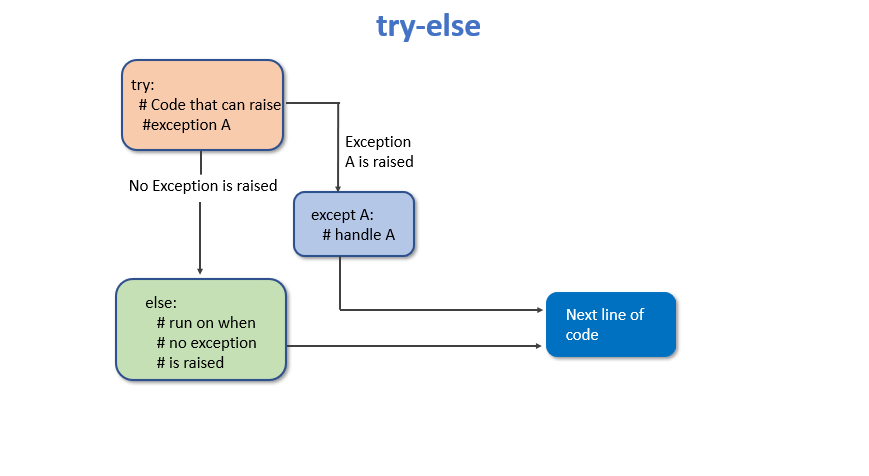 Python Exceptions and Errors – PYnative14 março 2025
Python Exceptions and Errors – PYnative14 março 2025 -
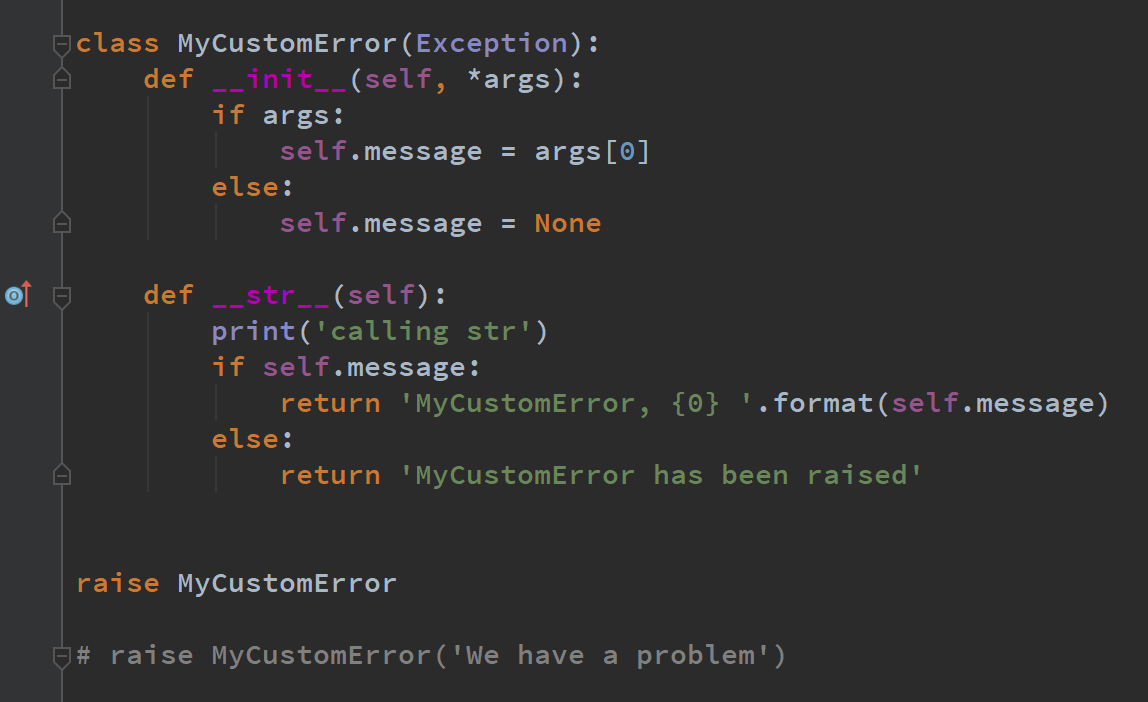 How to Define Custom Exception Classes in Python, by Stephen Fordham14 março 2025
How to Define Custom Exception Classes in Python, by Stephen Fordham14 março 2025 -
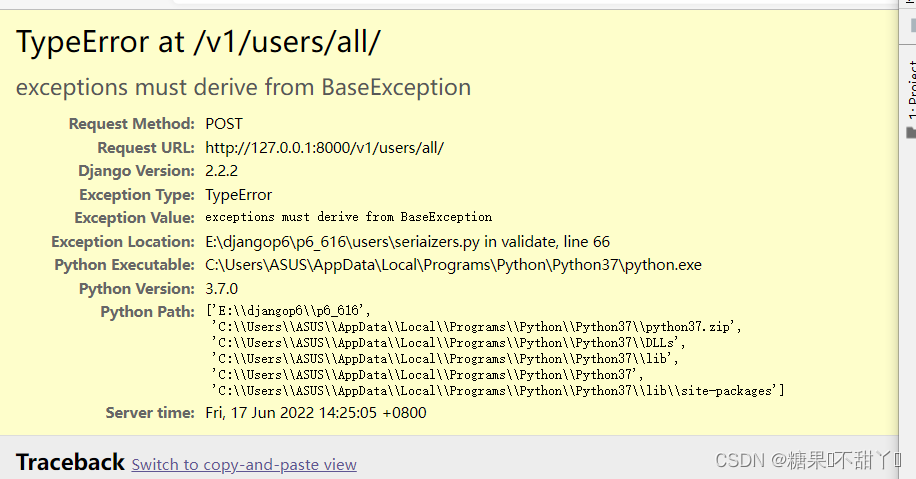 异常派生exceptions must derive from BaseException-CSDN博客14 março 2025
异常派生exceptions must derive from BaseException-CSDN博客14 março 2025 -
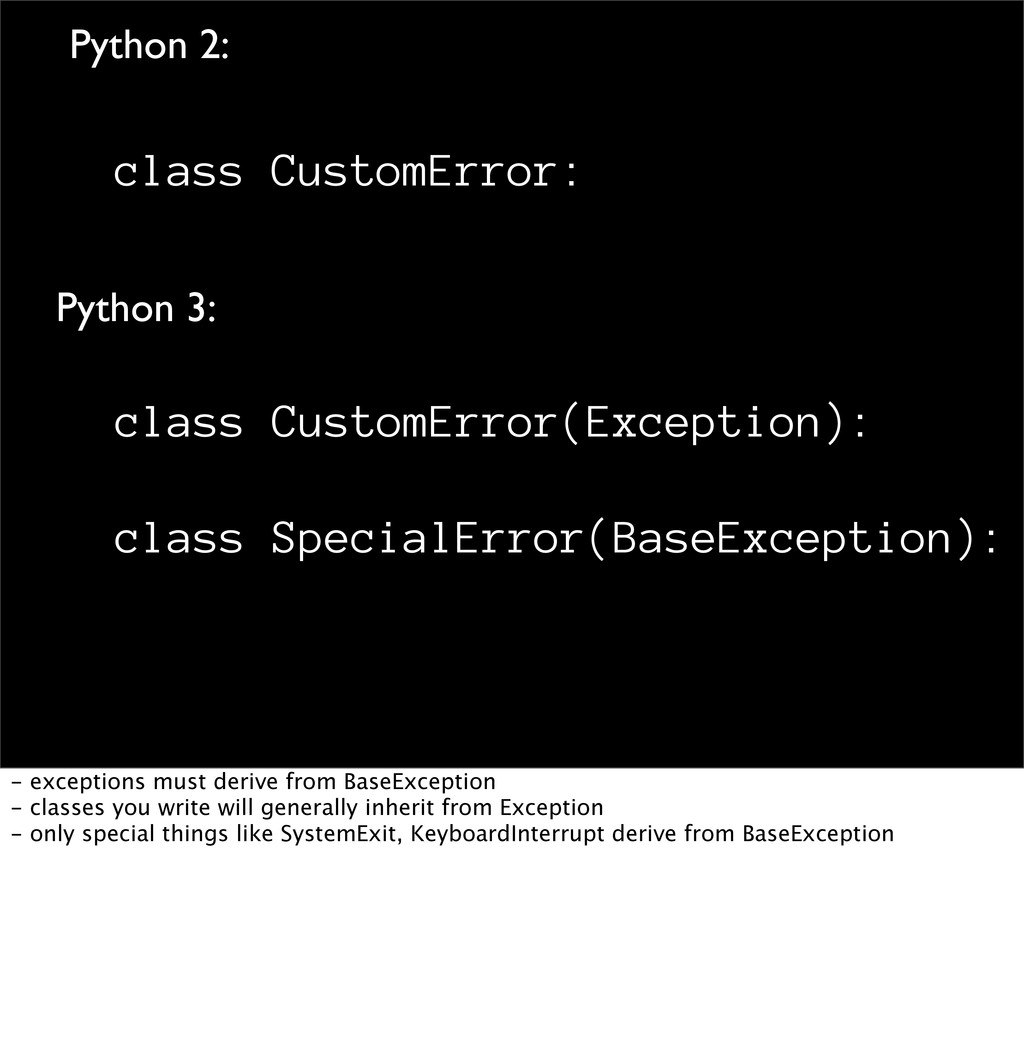 Porting to Python 3 - Speaker Deck14 março 2025
Porting to Python 3 - Speaker Deck14 março 2025 -
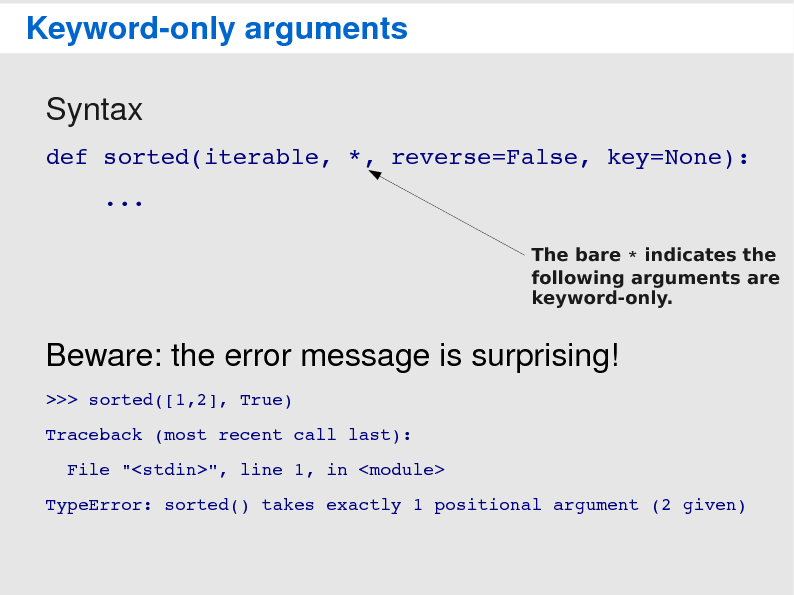 Porting your code to Python 314 março 2025
Porting your code to Python 314 março 2025 -
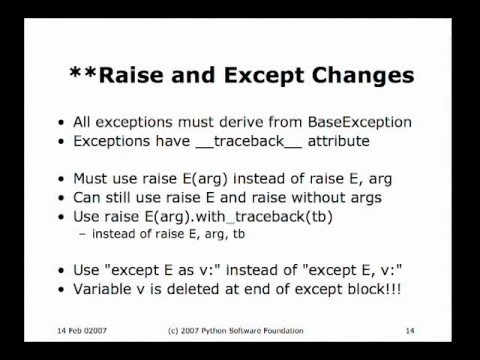 Python 300014 março 2025
Python 300014 março 2025 -
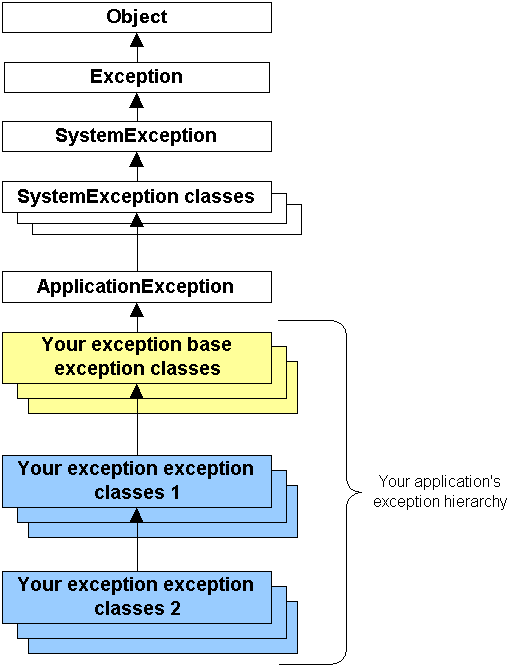 OLE DB Introduction14 março 2025
OLE DB Introduction14 março 2025 -
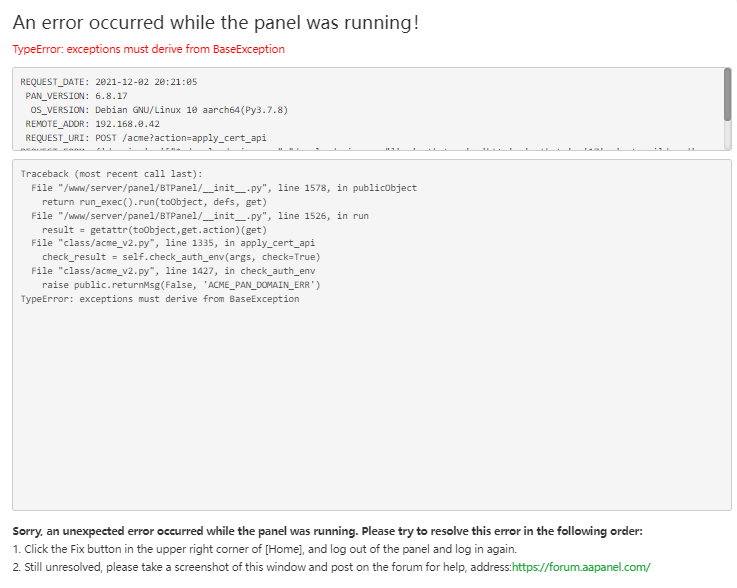 Error when applying SSL - aaPanel - Hosting control panel. One-click LAMP/LEMP.14 março 2025
Error when applying SSL - aaPanel - Hosting control panel. One-click LAMP/LEMP.14 março 2025 -
 9 Handling exceptions - Programmer's Guide to Apache Thrift14 março 2025
9 Handling exceptions - Programmer's Guide to Apache Thrift14 março 2025 -
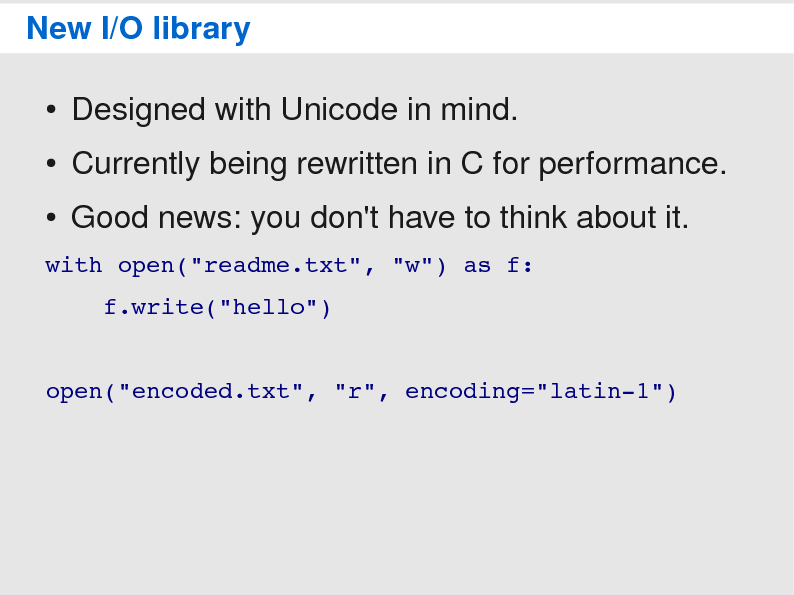 Porting your code to Python 314 março 2025
Porting your code to Python 314 março 2025
você pode gostar
-
 New posts in Level 8+ (Unconfirmed levels) - The Backrooms Community Community on Game Jolt14 março 2025
New posts in Level 8+ (Unconfirmed levels) - The Backrooms Community Community on Game Jolt14 março 2025 -
 How to Watch Friends Online From Anywhere: Complete Guide14 março 2025
How to Watch Friends Online From Anywhere: Complete Guide14 março 2025 -
 Last Rites, Robogames Wikia14 março 2025
Last Rites, Robogames Wikia14 março 2025 -
 The Last of Us Part 2: Remastered's No Return Roguelike Mode Gets First Look Trailer - IGN14 março 2025
The Last of Us Part 2: Remastered's No Return Roguelike Mode Gets First Look Trailer - IGN14 março 2025 -
 Guia básico: Regras D&D 5e - RPG Next14 março 2025
Guia básico: Regras D&D 5e - RPG Next14 março 2025 -
 Last week my wall certificate came in the mail. Today my office14 março 2025
Last week my wall certificate came in the mail. Today my office14 março 2025 -
 Actor Michael Ealy Speaks on Barbershop 3, Think Like A Man 314 março 2025
Actor Michael Ealy Speaks on Barbershop 3, Think Like A Man 314 março 2025 -
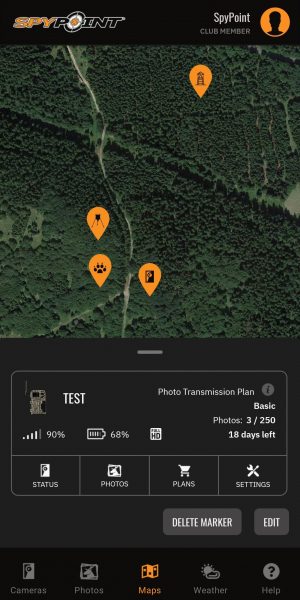 The SPYPOINT App14 março 2025
The SPYPOINT App14 março 2025 -
 Is there anyway to punish this queen opening?? It seems like it's all anybody ever does and it's getting really annoying. This is how it goes for me everytime and we end14 março 2025
Is there anyway to punish this queen opening?? It seems like it's all anybody ever does and it's getting really annoying. This is how it goes for me everytime and we end14 março 2025 -
 Cute Pou Sticker Sticker for Sale by viverradesigns14 março 2025
Cute Pou Sticker Sticker for Sale by viverradesigns14 março 2025