Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 19 janeiro 2025

Malware Analysis Benefits Incident Response

Windows Servers Security: How to Look for Suspicious Activities
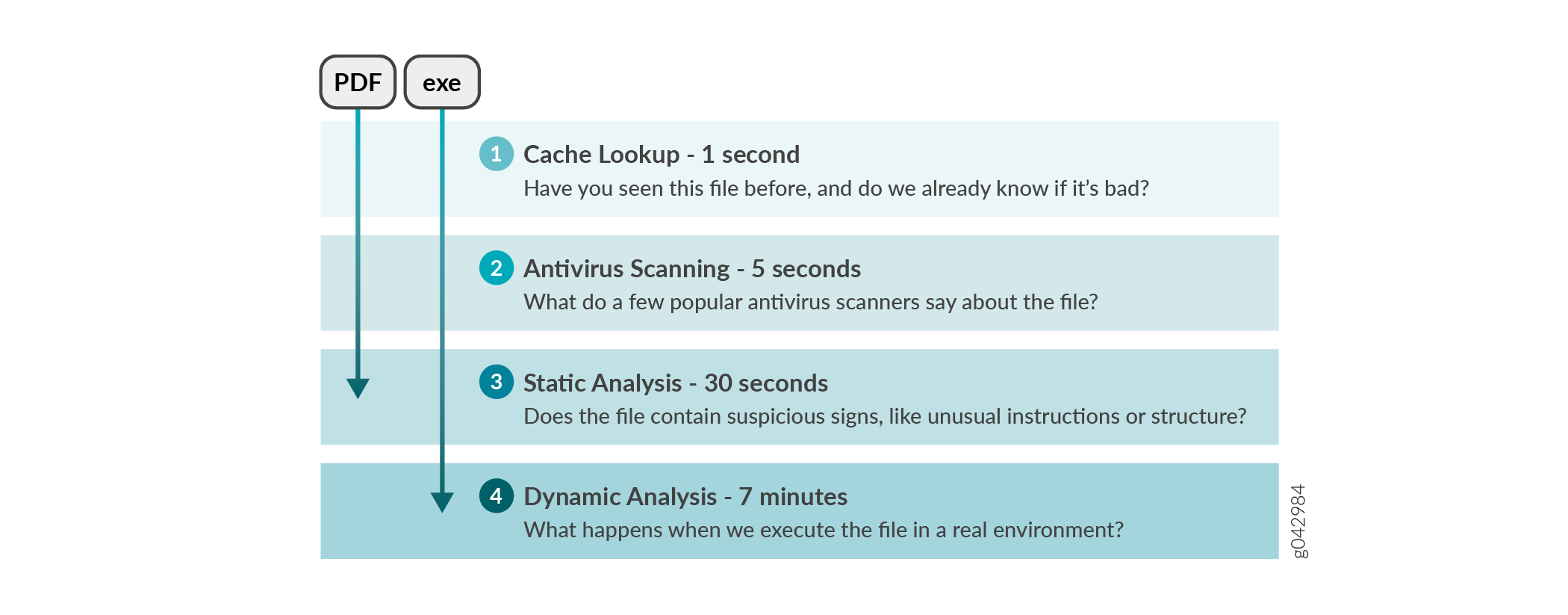
How is Malware Analyzed and Detected?, ATP Cloud
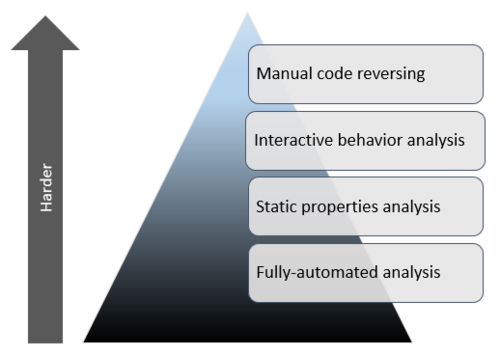
Mastering 4 Stages of Malware Analysis
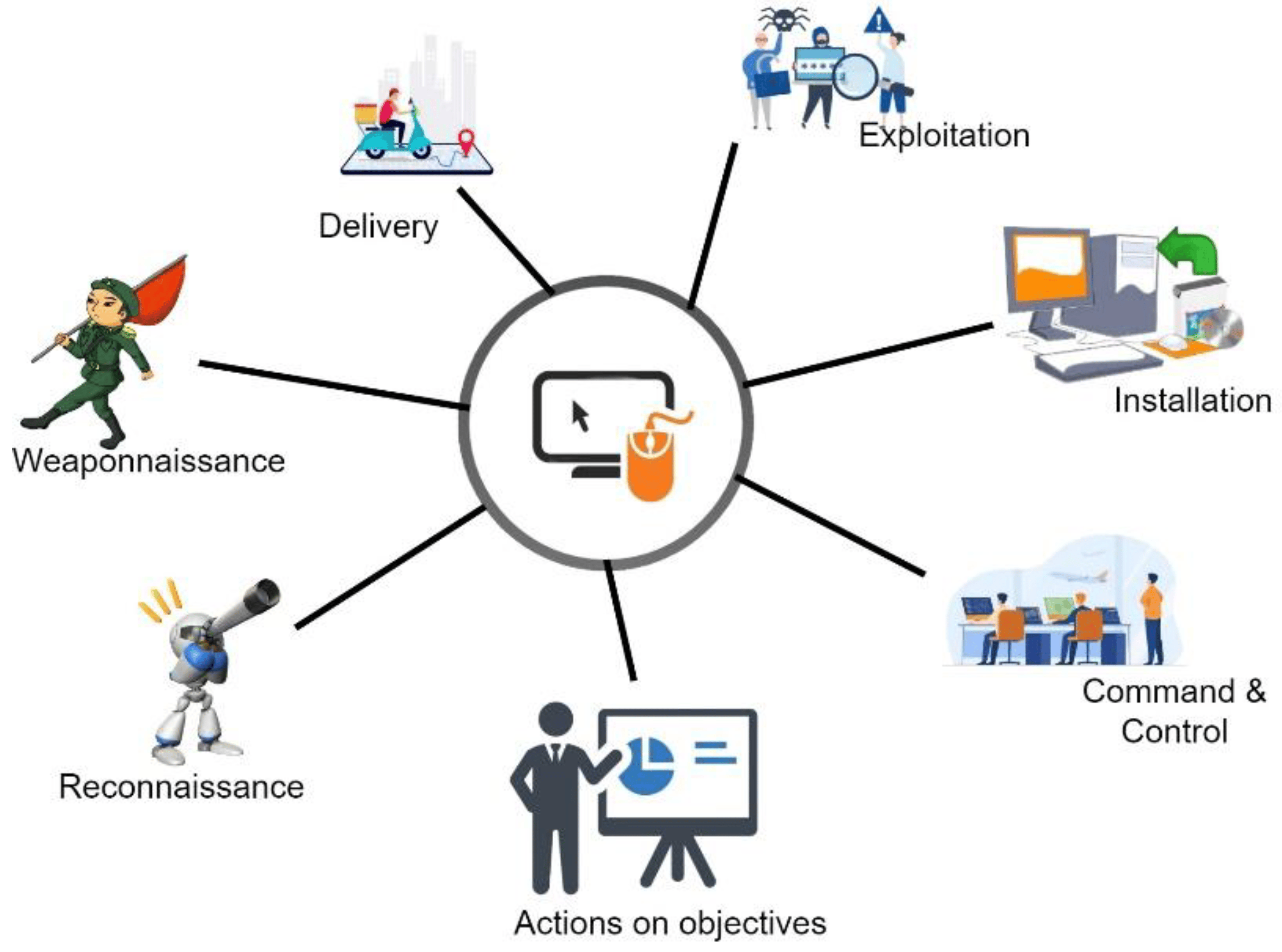
Symmetry, Free Full-Text
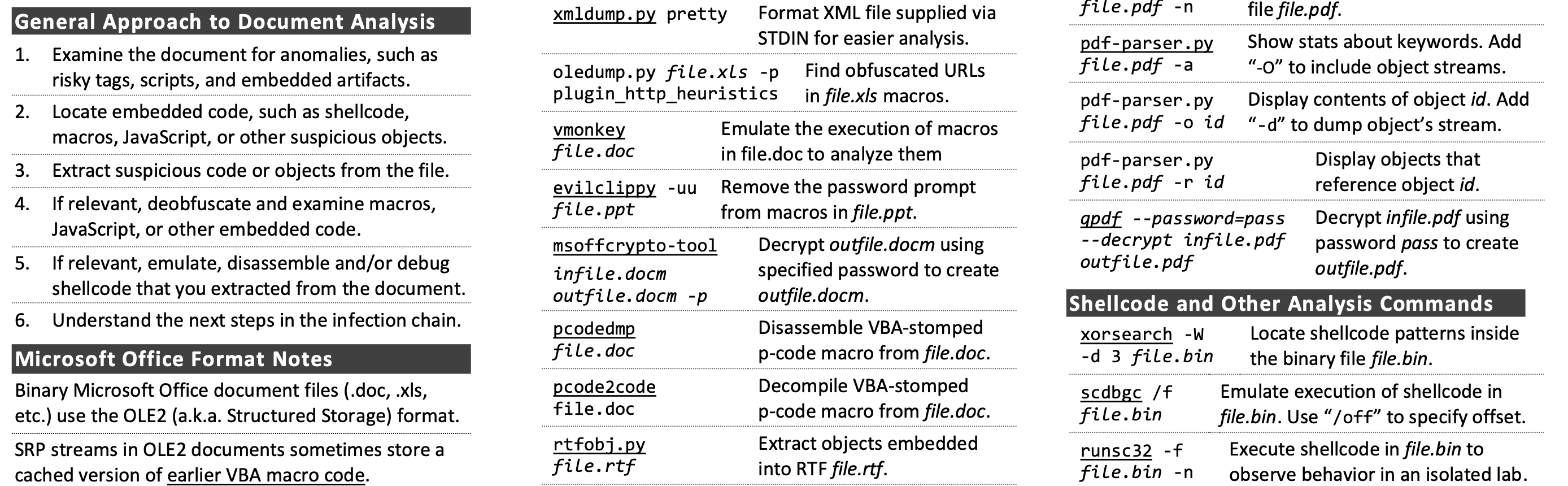
Analyzing Malicious Documents Cheat Sheet
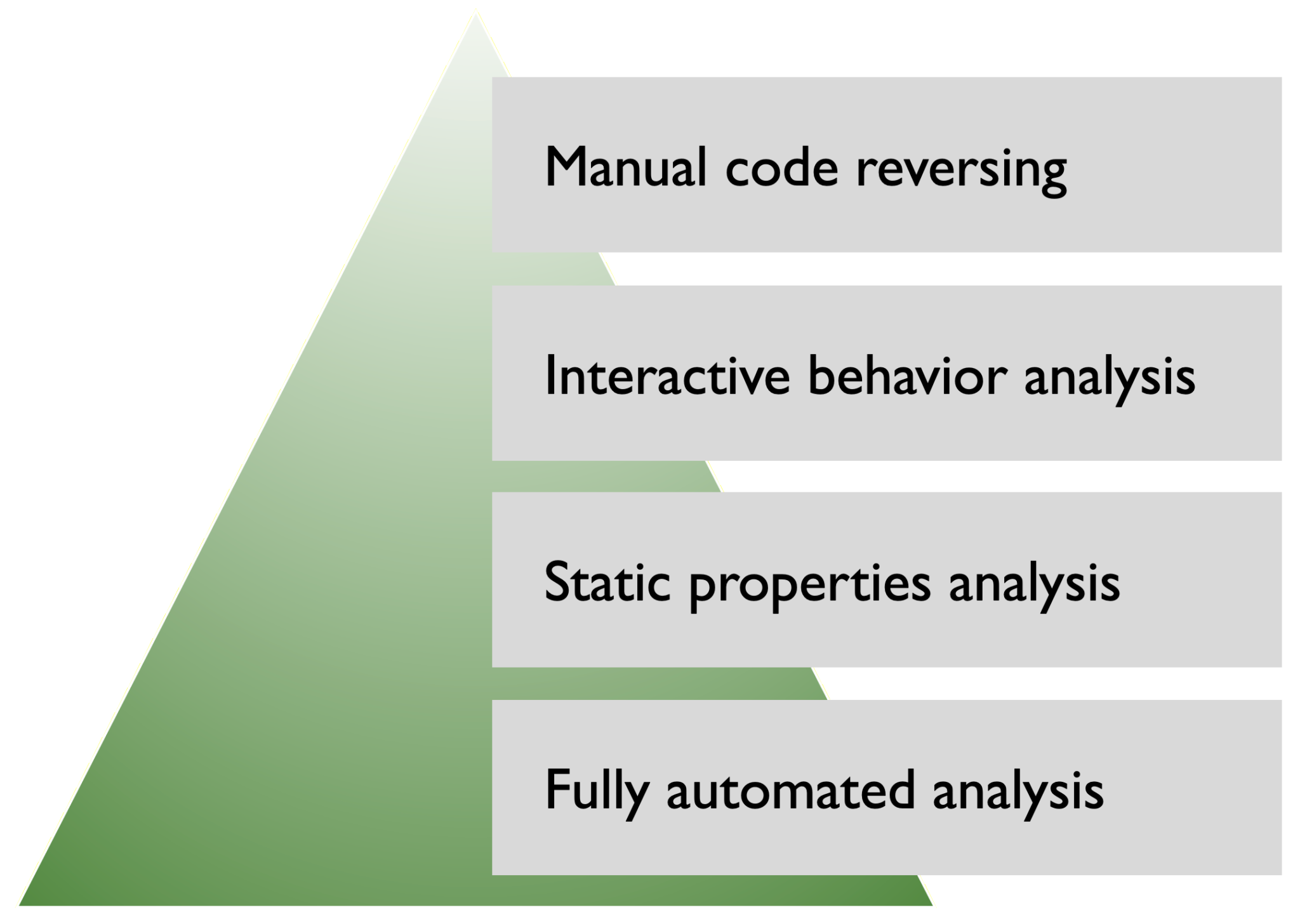
How You Can Start Learning Malware Analysis

How to Detect New Threats via Suspicious Activities

Operation Triangulation: iOS devices targeted with previously

Malware Incident Response Steps on Windows, and Determining If the
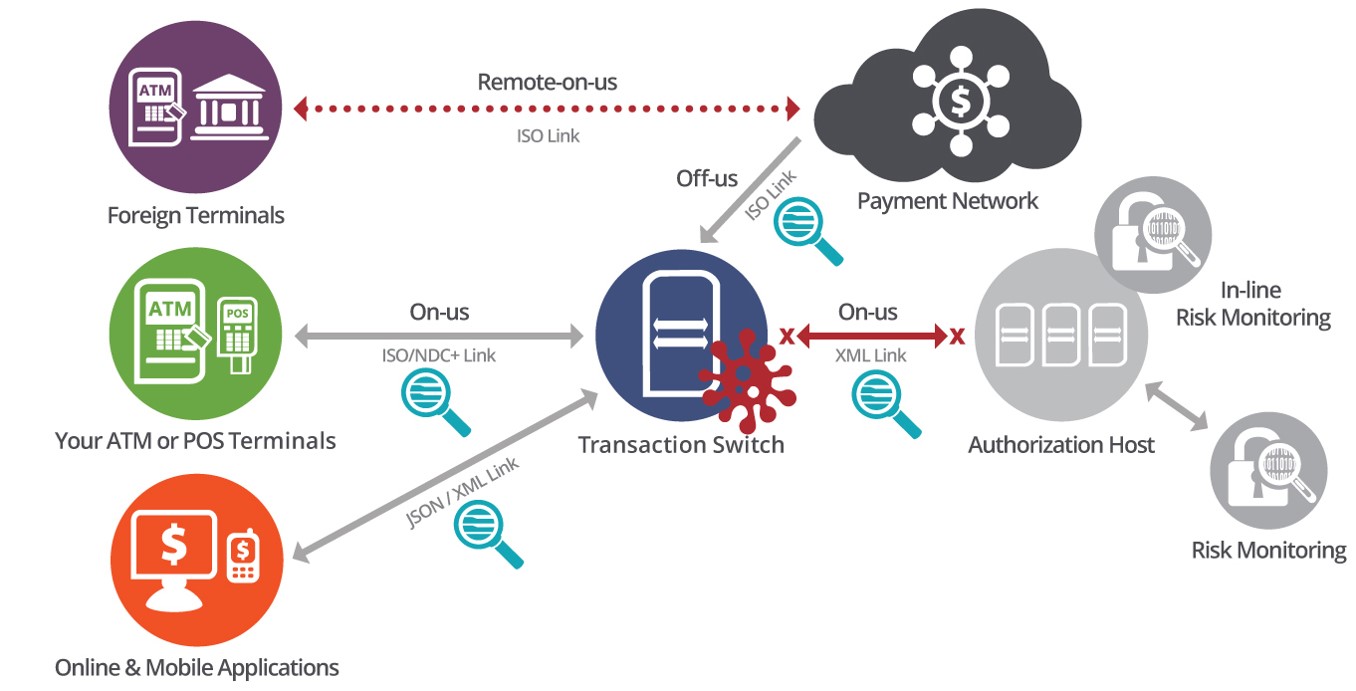
Malware Detection: One transaction at a time, INETCO Blog
Recomendado para você
-
/s.glbimg.com/po/tt2/f/original/2019/08/08/roblox-2.jpg) ROBLOX, Software19 janeiro 2025
ROBLOX, Software19 janeiro 2025 -
 ROBLOX FREE HACK, ROBLOX CHEAT DOWNLOAD19 janeiro 2025
ROBLOX FREE HACK, ROBLOX CHEAT DOWNLOAD19 janeiro 2025 -
roblox-exploit · GitHub Topics · GitHub19 janeiro 2025
-
 How to Avoid Getting Hacked on Roblox: 8 Steps (with Pictures)19 janeiro 2025
How to Avoid Getting Hacked on Roblox: 8 Steps (with Pictures)19 janeiro 2025 -
 Zeus S Executor Free, Zeus S Roblox Script 202319 janeiro 2025
Zeus S Executor Free, Zeus S Roblox Script 202319 janeiro 2025 -
 Randomizer Roblox Hack – Esp, Aimbot, WalkSPeed – Financial Derivatives Company, Limited19 janeiro 2025
Randomizer Roblox Hack – Esp, Aimbot, WalkSPeed – Financial Derivatives Company, Limited19 janeiro 2025 -
 Why You Should Avoid Roblox Hack V3.7 Download 70 Մամուլի խոսնակ - Անկախ հրապարակումների հարթակ19 janeiro 2025
Why You Should Avoid Roblox Hack V3.7 Download 70 Մամուլի խոսնակ - Անկախ հրապարակումների հարթակ19 janeiro 2025 -
 Roblox Hack Roblox pictures, Roblox, Ios games19 janeiro 2025
Roblox Hack Roblox pictures, Roblox, Ios games19 janeiro 2025 -
roblox-executor · GitHub Topics · GitHub19 janeiro 2025
-
:strip_icc()/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/L/9/A1pz9qTqWPixxA1dhC4Q/53586714-10156765096323580-9108199108673273856-n.jpg) Roblox permite hacks? Veja práticas proibidas na plataformas de games19 janeiro 2025
Roblox permite hacks? Veja práticas proibidas na plataformas de games19 janeiro 2025
você pode gostar
-
 Roblox Anime Champions codes in January 2023: Free Gems and Yen19 janeiro 2025
Roblox Anime Champions codes in January 2023: Free Gems and Yen19 janeiro 2025 -
 Elon Travels to Campbell For Thursday Night CAA Match - Elon University Athletics19 janeiro 2025
Elon Travels to Campbell For Thursday Night CAA Match - Elon University Athletics19 janeiro 2025 -
 Battle vs. Chess - Schachspiel für PC, Xbox 360 und PS319 janeiro 2025
Battle vs. Chess - Schachspiel für PC, Xbox 360 und PS319 janeiro 2025 -
 Pivot Base19 janeiro 2025
Pivot Base19 janeiro 2025 -
blaze x blox fruit script Trang web cờ bạc trực tuyến lớn nhất Việt Nam, w9bet.com, đánh nhau với gà trống, bắn cá và baccarat, và giành được hàng chục triệu giải19 janeiro 2025
-
 Batman: Arkham Collection Steam Key GLOBAL barato!19 janeiro 2025
Batman: Arkham Collection Steam Key GLOBAL barato!19 janeiro 2025 -
castle crasher mods|TikTok Search19 janeiro 2025
-
 Download Student Couple Matching Anime Profile Picture19 janeiro 2025
Download Student Couple Matching Anime Profile Picture19 janeiro 2025 -
 Chainsaw Man: horário de estreia do episódio 8 - MeUGamer19 janeiro 2025
Chainsaw Man: horário de estreia do episódio 8 - MeUGamer19 janeiro 2025 -
 Simon Says : Alexa Skills19 janeiro 2025
Simon Says : Alexa Skills19 janeiro 2025

