Malware analysis Malicious activity
Por um escritor misterioso
Last updated 21 março 2025
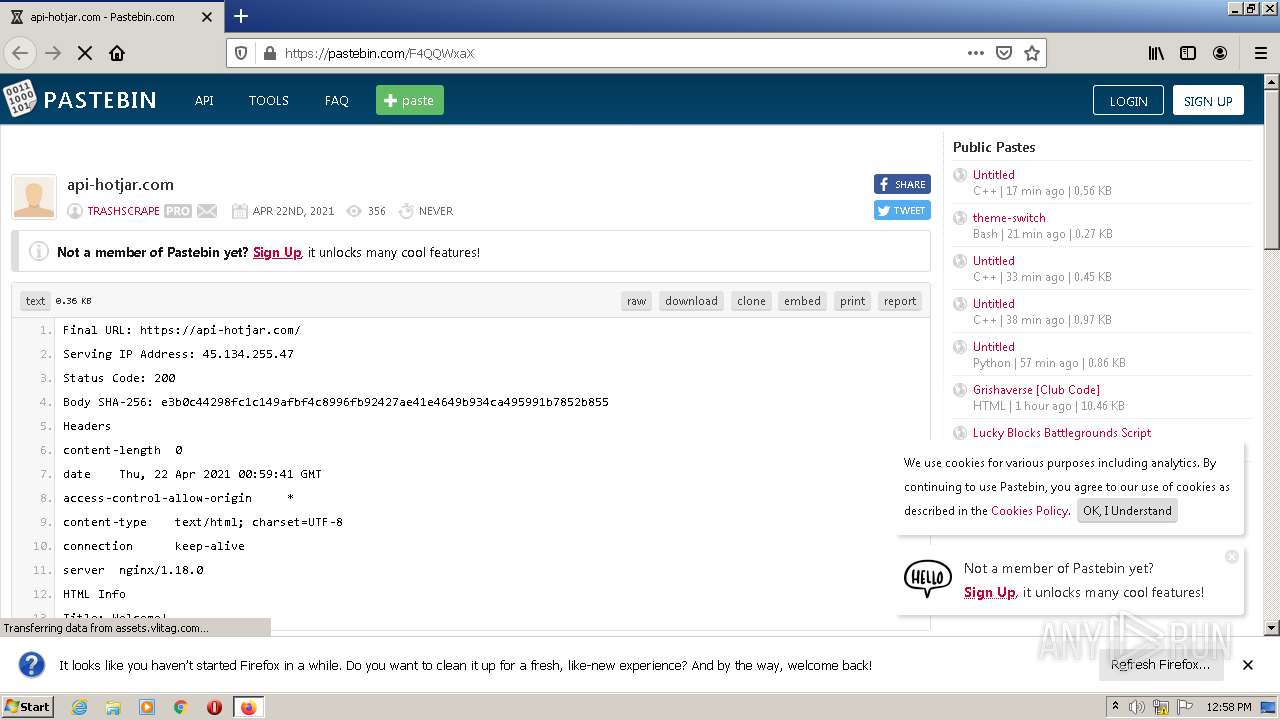

Intro to Malware Analysis: What It Is & How It Works - InfoSec

Outline of malware detection methodology.

How to Do Malware Analysis?

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1

StopRansomware: Rhysida Ransomware

Robust Malware Detection Models: Learning From Adversarial Attacks

Routers Roasting on an Open Firewall: the KV-botnet Investigation
Malware analysis file Malicious activity

Brute Force Attacks: Password Protection

Malware analysis Program_Install_and_Uninstall Malicious activity
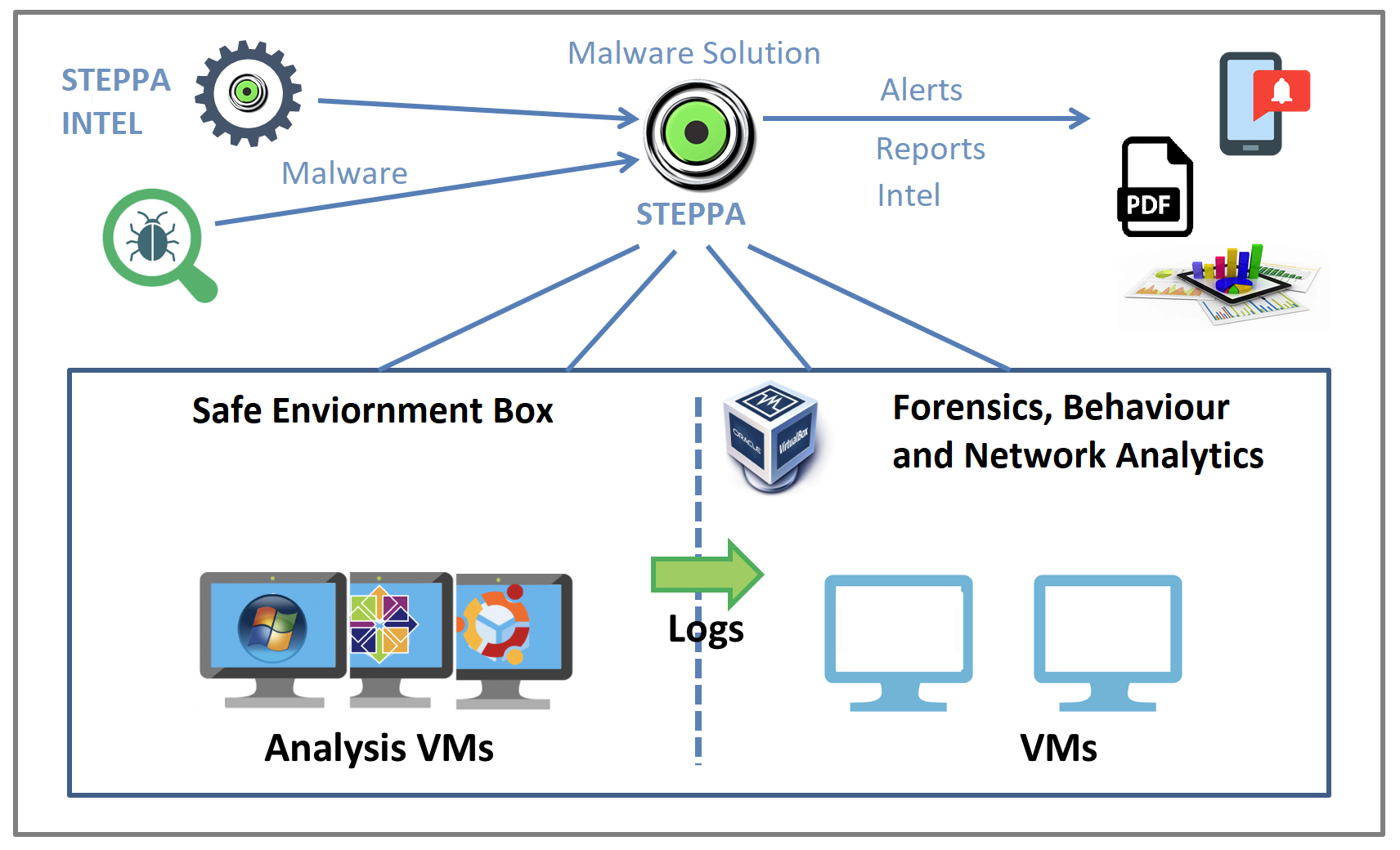
Malware Analysis Solution: Analyze, Detect, and Protect

StopRansomware: Rhysida Ransomware
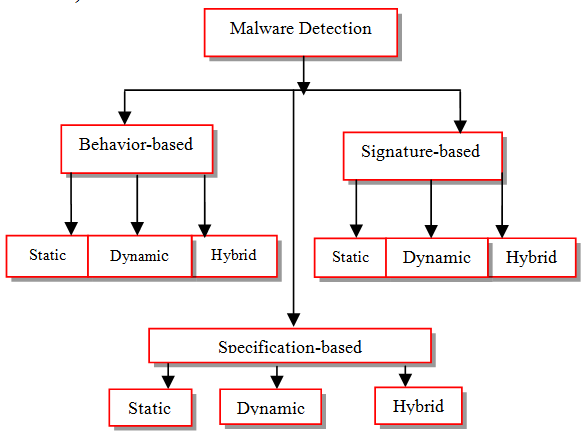
Organization of malware detection techniques (Elhadi et al., 2015

Unveiling activities of Tropic Trooper 2023 deep analysis of
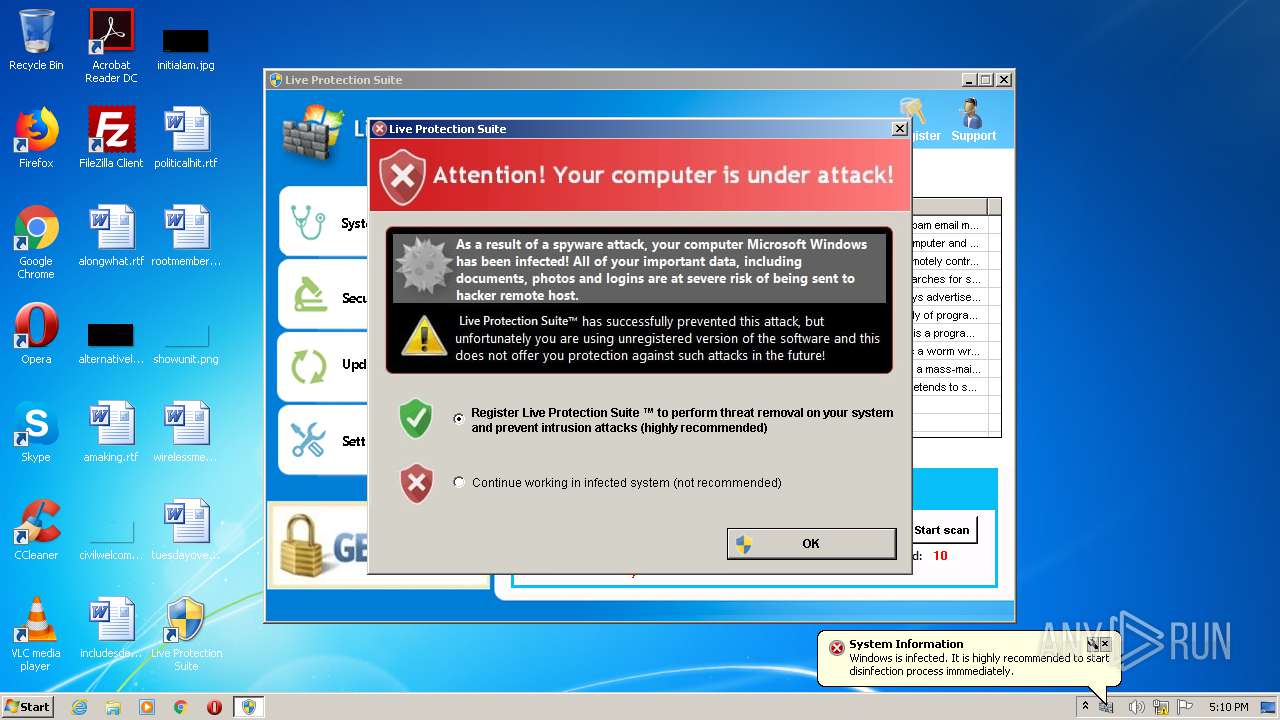
Malware analysis metasploit.bat Malicious activity
Recomendado para você
-
Roblox Silent Aim Script21 março 2025
-
Is zoom free to download Khalid music lyrics. Mountain mike's pizza oakdale.21 março 2025
-
Roblox Telekinesis Script21 março 2025
-
 NEW* LUCKY BLOCKS Battlegrounds Script (PASTEBIN 2023) (TAKE ANY BLOCK, SPEED, KILL ALL)21 março 2025
NEW* LUCKY BLOCKS Battlegrounds Script (PASTEBIN 2023) (TAKE ANY BLOCK, SPEED, KILL ALL)21 março 2025 -
![WORKING] Lucky Blocks Battlegrounds Script/GUI (KILL ALL, FLY) *PASTEBIN 2022*](https://i.ytimg.com/vi/gQm3x1gPxPs/maxresdefault.jpg) WORKING] Lucky Blocks Battlegrounds Script/GUI (KILL ALL, FLY) *PASTEBIN 2022*21 março 2025
WORKING] Lucky Blocks Battlegrounds Script/GUI (KILL ALL, FLY) *PASTEBIN 2022*21 março 2025 -
death ball roblox script|TikTok Search21 março 2025
-
 Super Kart Simulator Script Auto Wins » Download Free Cheats & Hacks for Your Game21 março 2025
Super Kart Simulator Script Auto Wins » Download Free Cheats & Hacks for Your Game21 março 2025 -
 Blizzard silenced Hearthstone players, and it made the game amazing : r/hearthstone21 março 2025
Blizzard silenced Hearthstone players, and it made the game amazing : r/hearthstone21 março 2025 -
 Scepter of Azj'Aqir - Item - World of Warcraft21 março 2025
Scepter of Azj'Aqir - Item - World of Warcraft21 março 2025 -
 RNC is expanding presence in the Delhi NCR region - RNC21 março 2025
RNC is expanding presence in the Delhi NCR region - RNC21 março 2025
você pode gostar
-
 All Rank Progression Rewards - Call of Duty: Modern Warfare 221 março 2025
All Rank Progression Rewards - Call of Duty: Modern Warfare 221 março 2025 -
Mortal Kombat 11 PPSSPP Android APK game #mortalkombat1121 março 2025
-
 Preview da Temporada – Gokukoku no Brynhildr21 março 2025
Preview da Temporada – Gokukoku no Brynhildr21 março 2025 -
shuumatsu no valkyrie 2 ep 11|TikTok Search21 março 2025
-
 Just Give Me the Damn Ball! by Keyshawn Johnson21 março 2025
Just Give Me the Damn Ball! by Keyshawn Johnson21 março 2025 -
 Pokemon 10475 Shiny Mega Gallade Pokedex: Evolution, Moves, Location, Stats21 março 2025
Pokemon 10475 Shiny Mega Gallade Pokedex: Evolution, Moves, Location, Stats21 março 2025 -
 Monkey? OMG No. One piece cosplay, Luffy cosplay, Easy cosplay21 março 2025
Monkey? OMG No. One piece cosplay, Luffy cosplay, Easy cosplay21 março 2025 -
 Number 89: Diablosis the Mind Hacker21 março 2025
Number 89: Diablosis the Mind Hacker21 março 2025 -
COMO DESENHAR KAKASHI COM CHIDORI, COMO DESENHAR KAKASHI COM CHIDORI . ACESSE: By kerodesenhar.com21 março 2025
-
AD Goalkeeper Gloves - DRAGON model🧤 • • Nikola Miljkovic, Fk Radnicki Niš @mr.keeper_gk_academy • • 〰️〰️〰️〰️〰️〰️ Hero of the Zero🧤 〰️〰️〰️〰️〰️〰️ • • #adgloves #heroofthezeroad #adteam #football #gloves #portier #golman21 março 2025




