Malware analysis Malicious activity
Por um escritor misterioso
Last updated 22 janeiro 2025

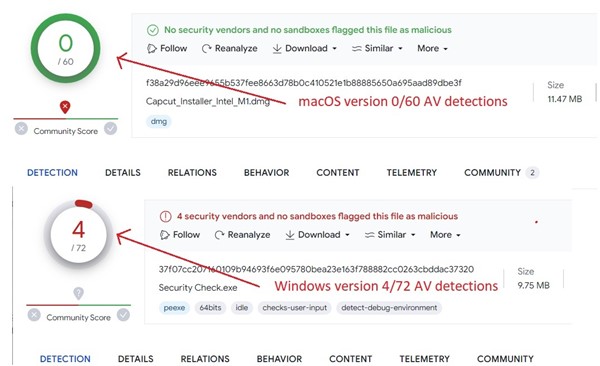
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

How to build a malware analysis sandbox with Elastic Security
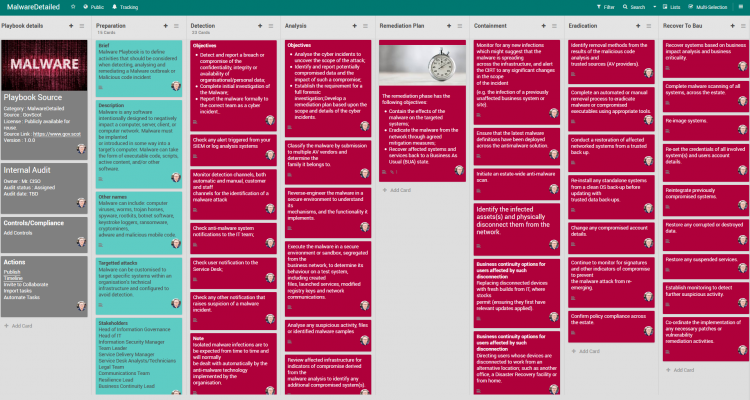
Playbook for Malware outbreak

StopRansomware: Rhysida Ransomware

What Is Malware Analysis? Definition, Types, Stages, and Best

UK and allies support Ukraine calling out Russia's GRU for

PROUD-MAL: static analysis-based progressive framework for deep

Malware Analysis - What is, Benefits & Types (Easily Explained)

Routers Roasting on an Open Firewall: the KV-botnet Investigation
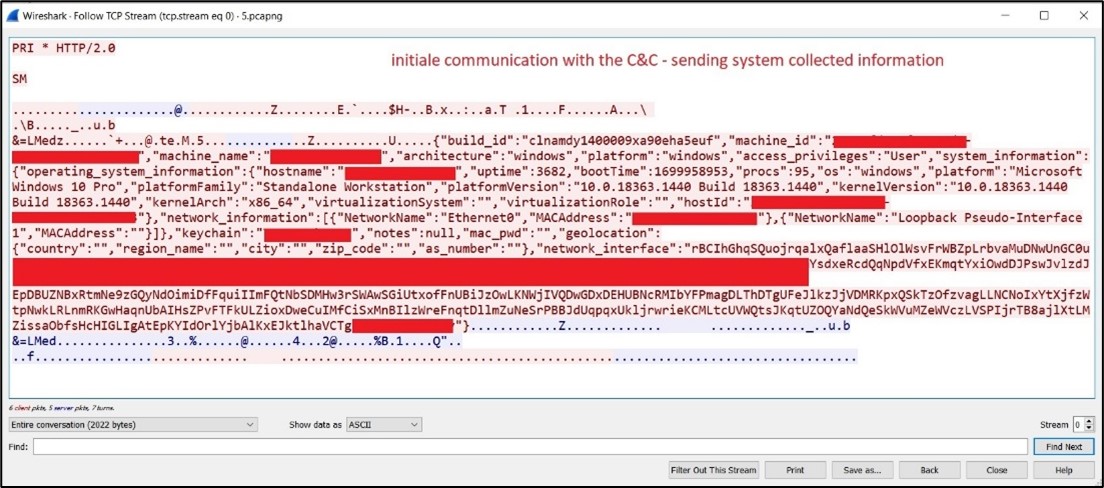
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
![How to Join Synapse X Discord [Fast & Simple] - Alvaro Trigo's Blog](https://alvarotrigo.com/blog/assets/imgs/2023-07-26/click-message-join-synapse-x-discord.jpeg) How to Join Synapse X Discord [Fast & Simple] - Alvaro Trigo's Blog22 janeiro 2025
How to Join Synapse X Discord [Fast & Simple] - Alvaro Trigo's Blog22 janeiro 2025 -
 Synapse X: Download and Install Guide22 janeiro 2025
Synapse X: Download and Install Guide22 janeiro 2025 -
![SYNAPSE X CRACK (BEST ROBLOX EXECUTOR) [WORKS 2021]](https://i.ytimg.com/vi/yGlhspG6ggA/maxresdefault.jpg) SYNAPSE X CRACK (BEST ROBLOX EXECUTOR) [WORKS 2021]22 janeiro 2025
SYNAPSE X CRACK (BEST ROBLOX EXECUTOR) [WORKS 2021]22 janeiro 2025 -
synapse-x · GitHub Topics · GitHub22 janeiro 2025
-
 SYNAPSE X CRACKED 2022, CRACK SYNAPSE X ROBLOX HACK22 janeiro 2025
SYNAPSE X CRACKED 2022, CRACK SYNAPSE X ROBLOX HACK22 janeiro 2025 -
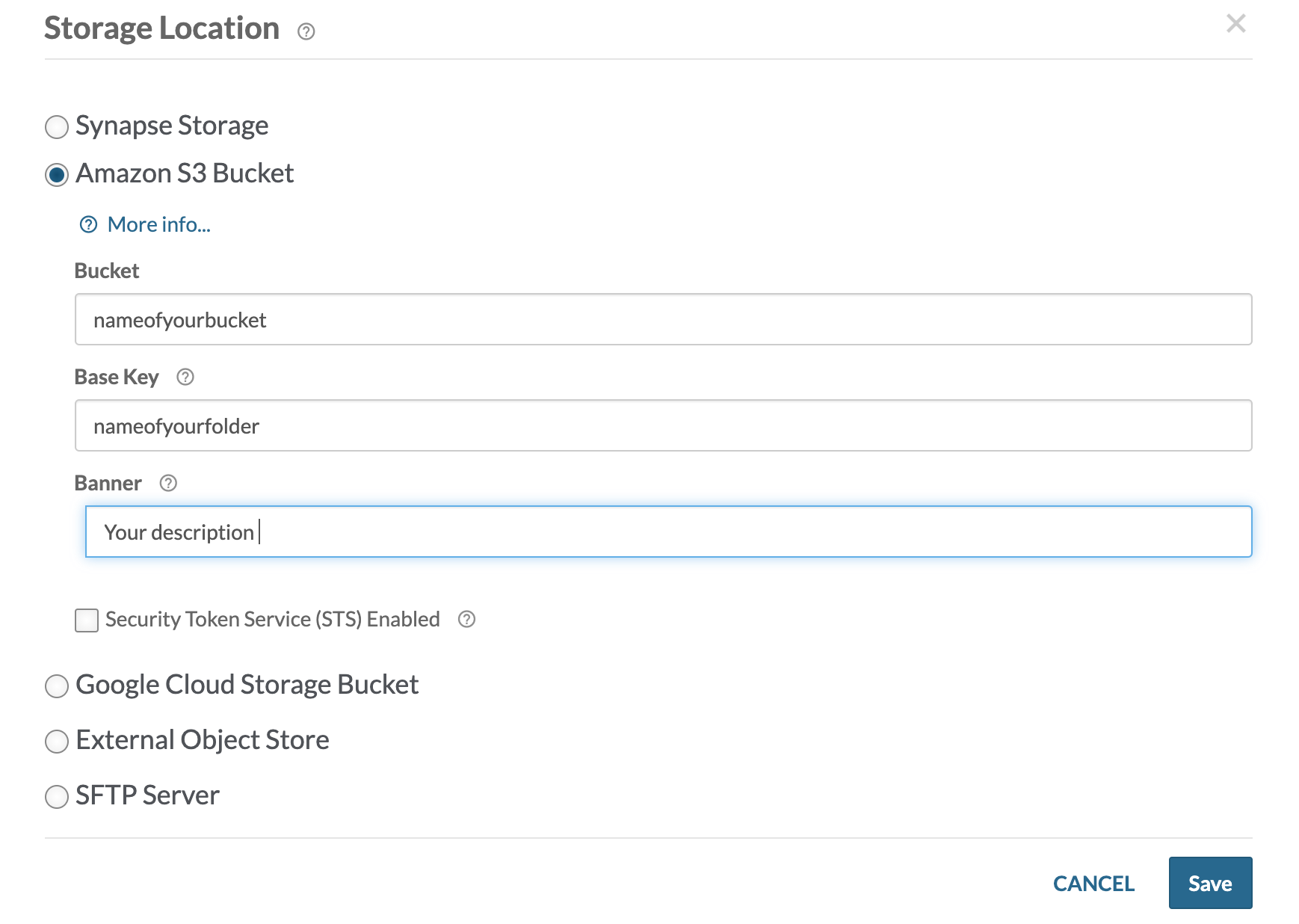 Custom Storage Locations22 janeiro 2025
Custom Storage Locations22 janeiro 2025 -
 How to configure the Razer Stream Controller on Razer Synapse 322 janeiro 2025
How to configure the Razer Stream Controller on Razer Synapse 322 janeiro 2025 -
 giving synapse key|TikTok Search22 janeiro 2025
giving synapse key|TikTok Search22 janeiro 2025 -
 Getting Started with Azure Synapse Studio 📑, by Rui Carvalho22 janeiro 2025
Getting Started with Azure Synapse Studio 📑, by Rui Carvalho22 janeiro 2025 -
 Synapse X Login22 janeiro 2025
Synapse X Login22 janeiro 2025
você pode gostar
-
 Today, Fisher Opening Party – Diario De Ibiza News22 janeiro 2025
Today, Fisher Opening Party – Diario De Ibiza News22 janeiro 2025 -
Demon Slayer Brasil - Nezuko como caçadora de demônios. Perfeita.❤ Cliquem na imagem., @zineshizz - twitter, /Mitsuri22 janeiro 2025
-
 Anime - tokyo revengers Wallpaper Download22 janeiro 2025
Anime - tokyo revengers Wallpaper Download22 janeiro 2025 -
 Blocos de construção de jogo colorido universal crianças desktop jogando brinquedos de madeira blocos russos brinquedos educativos iniciais – os melhores produtos na loja online Joom Geek22 janeiro 2025
Blocos de construção de jogo colorido universal crianças desktop jogando brinquedos de madeira blocos russos brinquedos educativos iniciais – os melhores produtos na loja online Joom Geek22 janeiro 2025 -
999K Anime Stickers WASticker - Apps on Google Play22 janeiro 2025
-
 Mini Phoenix - Guild Wars 2 Wiki (GW2W)22 janeiro 2025
Mini Phoenix - Guild Wars 2 Wiki (GW2W)22 janeiro 2025 -
 Design life thumbnail with impressive quotes.22 janeiro 2025
Design life thumbnail with impressive quotes.22 janeiro 2025 -
donation-website · GitHub Topics · GitHub22 janeiro 2025
-
 Diferença entre utsukushii e subarashii!22 janeiro 2025
Diferença entre utsukushii e subarashii!22 janeiro 2025 -
 ZERO by PUFF BAR, Watermelon Slush Flavor22 janeiro 2025
ZERO by PUFF BAR, Watermelon Slush Flavor22 janeiro 2025
