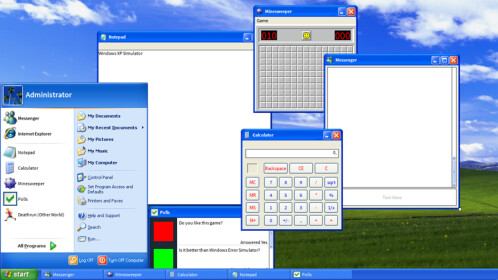
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 16 julho 2024
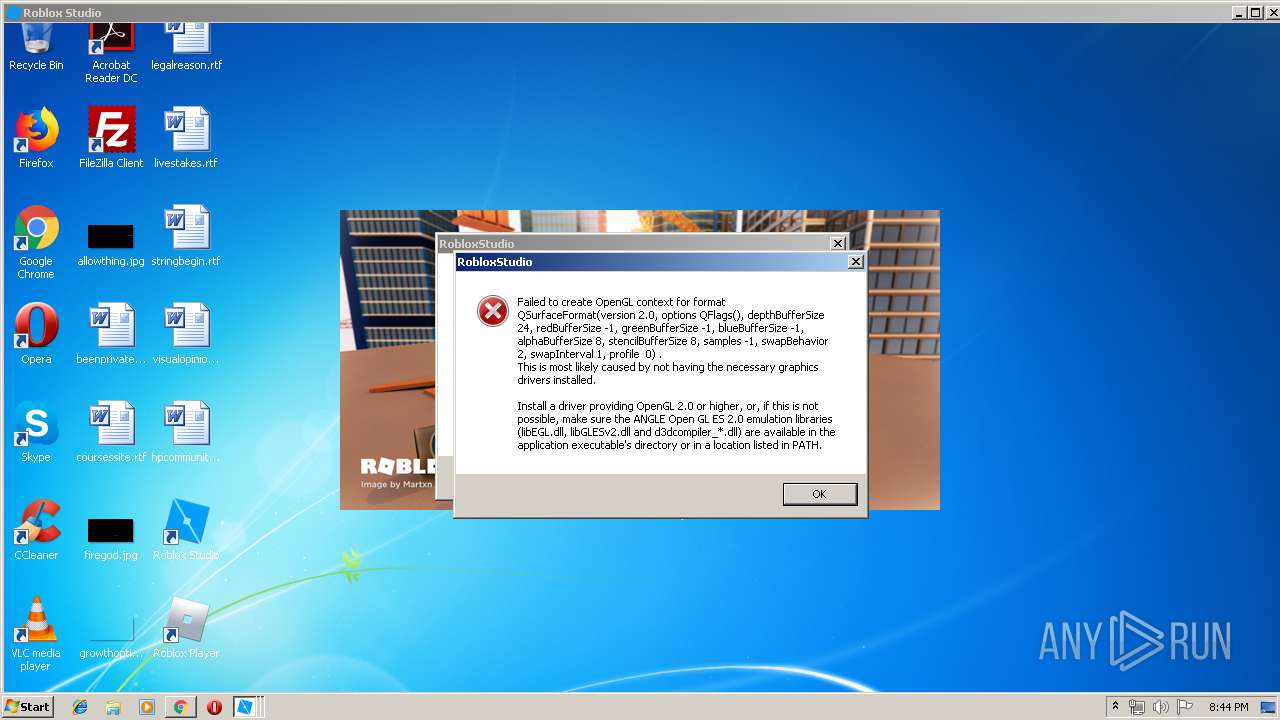

TryHackMe Hacktivities

Malware Analysis - What is, Benefits & Types (Easily Explained)

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging

Malware analysis Program_Install_and_Uninstall Malicious activity

Malware Analysis: Protecting Your Network from Cyber Attacks

Mastering Malware Analysis

Dynamic malware analysis [34]

A detailed analysis of the Menorah malware used by APT34
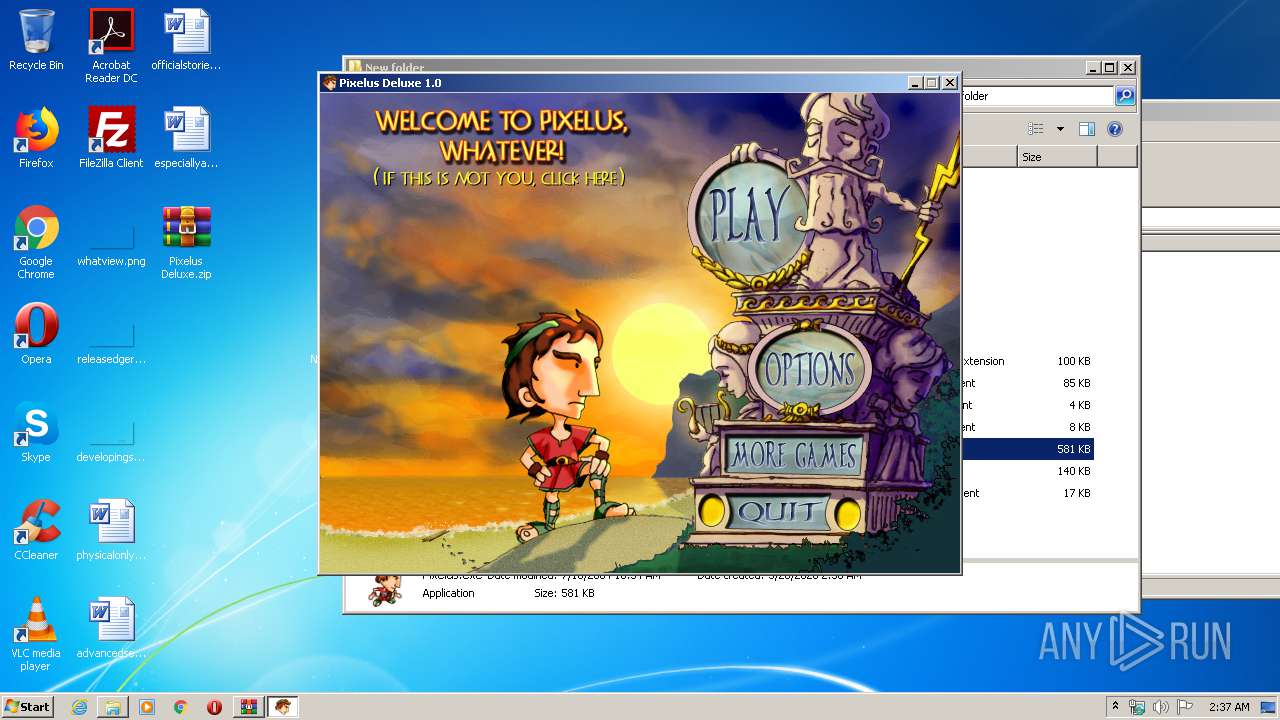
Malware analysis Pixelus Deluxe.zip Malicious activity

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug
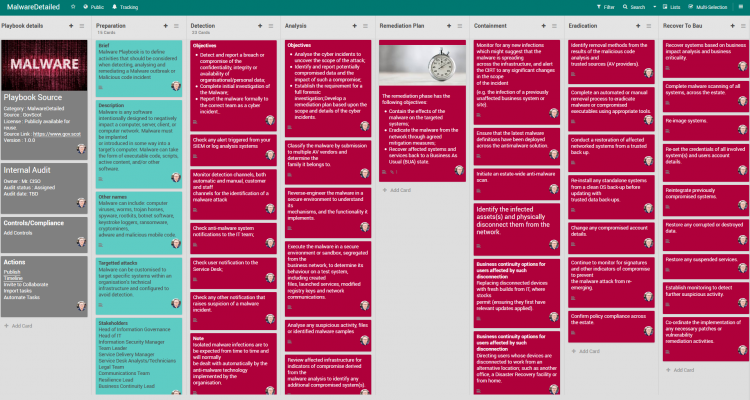
Playbook for Malware outbreak

Malware Analysis: Steps & Examples - CrowdStrike

Intro to Malware Analysis: What It Is & How It Works - InfoSec

PROUD-MAL: static analysis-based progressive framework for deep

Antivirus software - Wikipedia
Recomendado para você
-
 How to Download & Play Roblox for Free on Any Platform16 julho 2024
How to Download & Play Roblox for Free on Any Platform16 julho 2024 -
 Playing games in ROBLOX Studio - Studio Bugs - Developer Forum16 julho 2024
Playing games in ROBLOX Studio - Studio Bugs - Developer Forum16 julho 2024 -
 How to Play Roblox on Your PC16 julho 2024
How to Play Roblox on Your PC16 julho 2024 -
Windows XP Simulator - Roblox16 julho 2024
-
 How to install/download roblox on Windows XP SP2 and SP316 julho 2024
How to install/download roblox on Windows XP SP2 and SP316 julho 2024 -
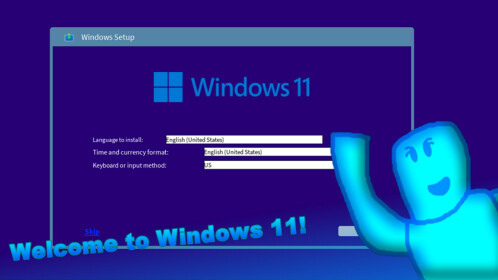
1M Visits Badge 💿 Windows 11 - Roblox16 julho 2024
-
 Roblox Icon16 julho 2024
Roblox Icon16 julho 2024 -
Roblox Won't Start/Download16 julho 2024
-
 Windows XP Home Edition SP3 x86 : Microsoft : Free Download, Borrow, and Streaming : Internet Archive16 julho 2024
Windows XP Home Edition SP3 x86 : Microsoft : Free Download, Borrow, and Streaming : Internet Archive16 julho 2024 -
 Roblox Studio - Download16 julho 2024
Roblox Studio - Download16 julho 2024
você pode gostar
-
 Ghosted' Review: Chris Evans and Ana de Armas in Action Romance – Deadline16 julho 2024
Ghosted' Review: Chris Evans and Ana de Armas in Action Romance – Deadline16 julho 2024 -
 Mr Robot season 3 review - Why Mr Robot deserves a second chance16 julho 2024
Mr Robot season 3 review - Why Mr Robot deserves a second chance16 julho 2024 -
 Mark Hamill, John Boyega Support Campaign to Let Terminally Ill16 julho 2024
Mark Hamill, John Boyega Support Campaign to Let Terminally Ill16 julho 2024 -
 Ways to Make Hide and Seek More Enjoyable for Your Child16 julho 2024
Ways to Make Hide and Seek More Enjoyable for Your Child16 julho 2024 -
Woman power16 julho 2024
-
 roblox doors eyes full audio by Onee Sound Effect - Meme Button - Tuna16 julho 2024
roblox doors eyes full audio by Onee Sound Effect - Meme Button - Tuna16 julho 2024 -
 He Lived Alone on an Island for 40 Years, DUB16 julho 2024
He Lived Alone on an Island for 40 Years, DUB16 julho 2024 -
 Happy Wheels Unblocked Sticker Vinyl Waterproof Sticker Decal Car Laptop Wall Window Bumper Sticker 516 julho 2024
Happy Wheels Unblocked Sticker Vinyl Waterproof Sticker Decal Car Laptop Wall Window Bumper Sticker 516 julho 2024 -
![Super Power Evolution Simulator Codes [NEW] - Try Hard Guides](https://tryhardguides.com/wp-content/uploads/2023/03/featured-super-power-evolution-simulator-codes.jpg) Super Power Evolution Simulator Codes [NEW] - Try Hard Guides16 julho 2024
Super Power Evolution Simulator Codes [NEW] - Try Hard Guides16 julho 2024 -
Don Woods16 julho 2024