The Windows Process Journey — cmd.exe (Windows Command Processor), by Shlomi Boutnaru, Ph.D.
Por um escritor misterioso
Last updated 06 janeiro 2025
“cmd.exe” is the “Windows Command Processor” which is the default CLI (command line interface/interpreter) of Windows (and also reactOS). By the way, it is also known as “Command Prompt”. It is the…

SRM: A Security Reference Monitor for Windows Security. Learn more about it here: Shlomi Boutnaru, Ph.D. posted on the topic

The Windows Process Journey: by Dr. Shlomi Boutnaru, PDF, Windows Registry
The Linux Security Journey — iptables: Chains, by Shlomi Boutnaru, Ph.D.

Use nim compiled language to evade Windows Defender reverse shell detection, by Nol White Hat
Privilege Escalation] Breaking out of Chroot Jail, by Nishant Sharma
Building a FreeIPA Lab. While researching FreeIPA one thing has…, by n0pe_sled

Shlomi Boutnaru, Ph.D. on LinkedIn: #windows #microsoft #security #infosec #learning #devops #devsecops…

Aviad Noama - Tel Aviv District, Israel, Professional Profile

Shlomi Boutnaru, Ph.D. on LinkedIn: #windows #microsoft #learning #devops #devsecops #thewindowsprocessjourney…

Use nim compiled language to evade Windows Defender reverse shell detection, by Nol White Hat

Process injection: How attackers run malicious code in other processes

Exploring Execute-Assembly: A Deep Dive into In-Memory Threat Execution, by Tho Le

Bypass “Mimikatz” using the Process Injection Technique, by Usman Sikander
Recomendado para você
-
 How to use CMD.exe (Command Prompt)06 janeiro 2025
How to use CMD.exe (Command Prompt)06 janeiro 2025 -
 Cmd Command06 janeiro 2025
Cmd Command06 janeiro 2025 -
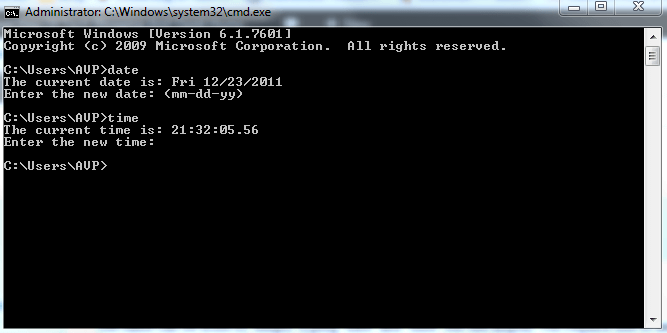 Beginner's Guide to Windows CMD - MiniTool06 janeiro 2025
Beginner's Guide to Windows CMD - MiniTool06 janeiro 2025 -
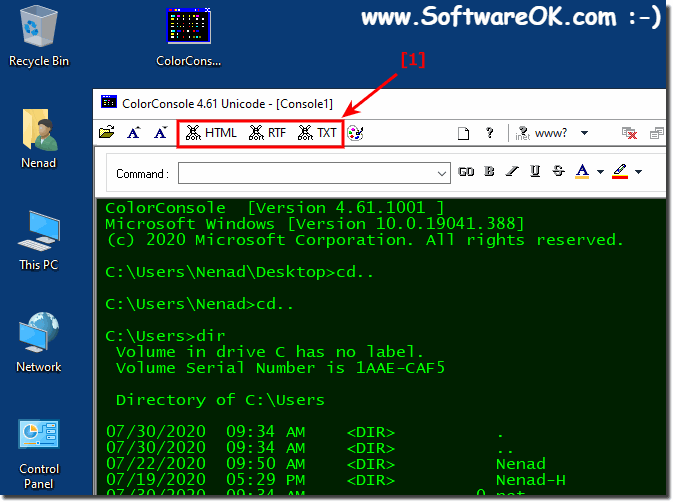 Export the output of the command prompt (cmd.exe) TXT, RTF, HTML06 janeiro 2025
Export the output of the command prompt (cmd.exe) TXT, RTF, HTML06 janeiro 2025 -
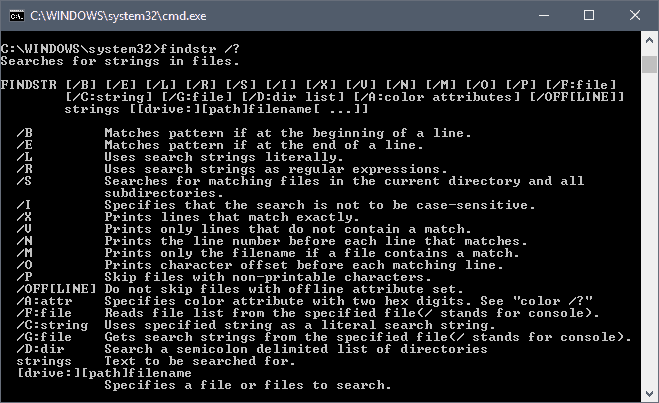 findstr review: Handy Windows tool for command searches for text strings - gHacks Tech News06 janeiro 2025
findstr review: Handy Windows tool for command searches for text strings - gHacks Tech News06 janeiro 2025 -
 Executing Command-Line Commands in TwinCAT06 janeiro 2025
Executing Command-Line Commands in TwinCAT06 janeiro 2025 -
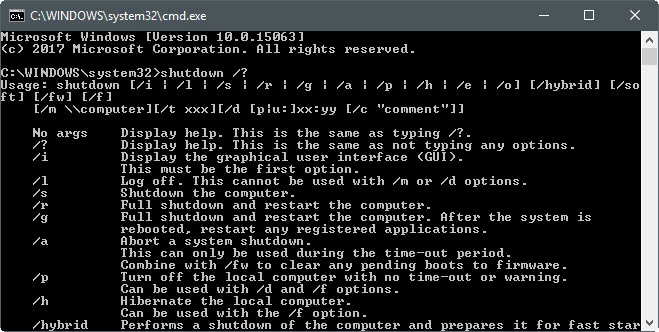 How to use the Windows shutdown command - gHacks Tech News06 janeiro 2025
How to use the Windows shutdown command - gHacks Tech News06 janeiro 2025 -
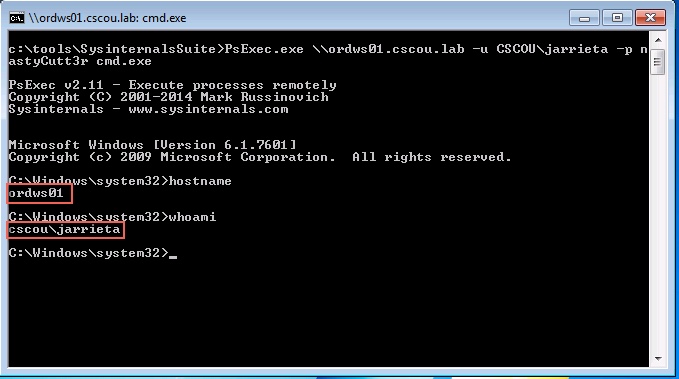 Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog06 janeiro 2025
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog06 janeiro 2025 -
 This window titled “C:/WINDOWS/system32/cmd.exe” randomly appears on my computer sometimes. Does anyone know what this could be? : r/computers06 janeiro 2025
This window titled “C:/WINDOWS/system32/cmd.exe” randomly appears on my computer sometimes. Does anyone know what this could be? : r/computers06 janeiro 2025 -
Solved: Run Command Tool - cmd.exe runs perfectly until I - Alteryx Community06 janeiro 2025
você pode gostar
-
 Spongebob Squarepants Movie Faces Collage Meme Wood Print by Joe Taylor - Pixels06 janeiro 2025
Spongebob Squarepants Movie Faces Collage Meme Wood Print by Joe Taylor - Pixels06 janeiro 2025 -
 A Bruxa' impediu Anya Taylor-Joy de ser uma estrela do Disney06 janeiro 2025
A Bruxa' impediu Anya Taylor-Joy de ser uma estrela do Disney06 janeiro 2025 -
 Jogos – Cris e as Tecnologias Educacionais06 janeiro 2025
Jogos – Cris e as Tecnologias Educacionais06 janeiro 2025 -
 Problems with uploading shirts to roblox - Art Design Support - Developer Forum06 janeiro 2025
Problems with uploading shirts to roblox - Art Design Support - Developer Forum06 janeiro 2025 -
/pic5825973.jpg) The World of Vampire Hunter D, RPG Item06 janeiro 2025
The World of Vampire Hunter D, RPG Item06 janeiro 2025 -
 Oakley Camiseta feminina Ultra Frog B1b Rc, New Granite Heather06 janeiro 2025
Oakley Camiseta feminina Ultra Frog B1b Rc, New Granite Heather06 janeiro 2025 -
 Suzume' Opens a Door to the Spiritual Discipline of Deli06 janeiro 2025
Suzume' Opens a Door to the Spiritual Discipline of Deli06 janeiro 2025 -
 COMO JOGAR PACIÊNCIA - REGRAS EXPLICADAS COM MUITA PACIÊNCIA06 janeiro 2025
COMO JOGAR PACIÊNCIA - REGRAS EXPLICADAS COM MUITA PACIÊNCIA06 janeiro 2025 -
 Weird Internet Issue - Scripting Support - Developer Forum06 janeiro 2025
Weird Internet Issue - Scripting Support - Developer Forum06 janeiro 2025 -
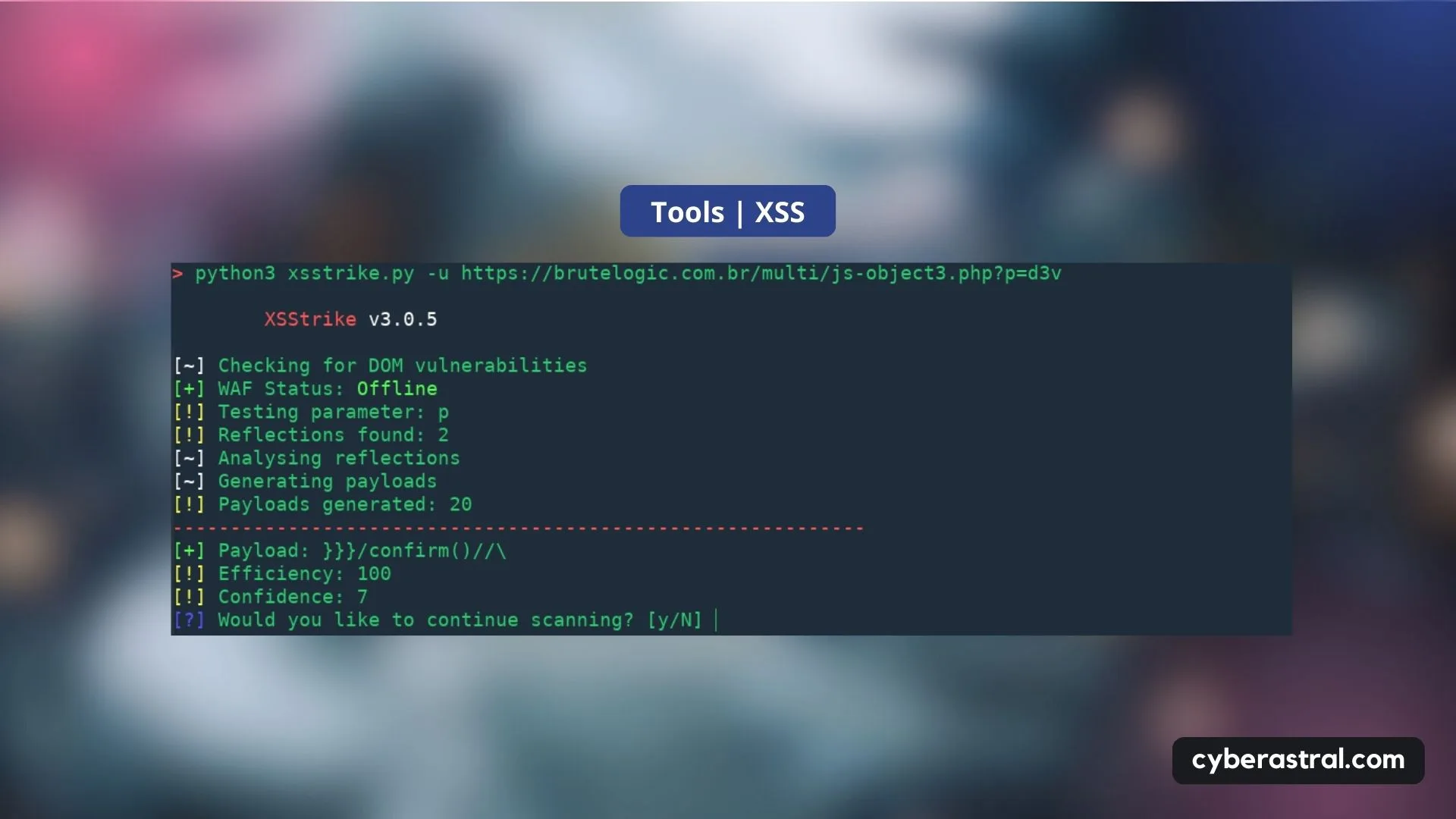 XSStrike XSS • CyberAstral • Your Trusted Cybersecurity Partner06 janeiro 2025
XSStrike XSS • CyberAstral • Your Trusted Cybersecurity Partner06 janeiro 2025