JUST EXPLOIT - Home
Por um escritor misterioso
Last updated 16 março 2025

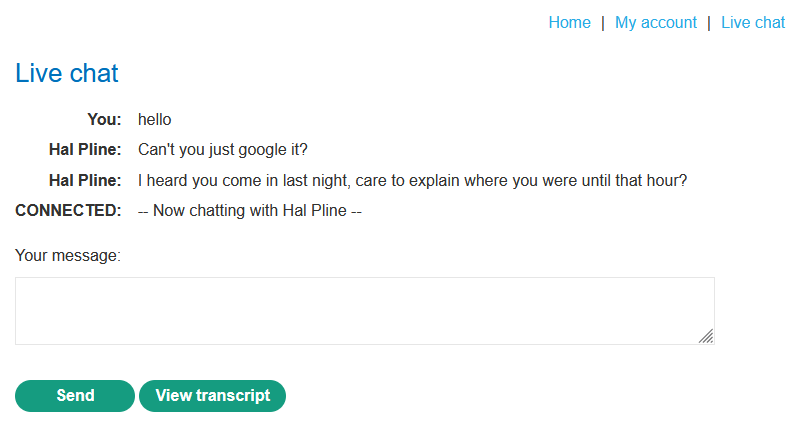
A Guide to IDOR. In this article you'll find the answers…, by Eduardo Cardoso, stolabs

Corelan Consulting & Training

Vintage Shazam⚡️Video Disc CED

How US brands can exploit shift to at-home consumption - Just Food
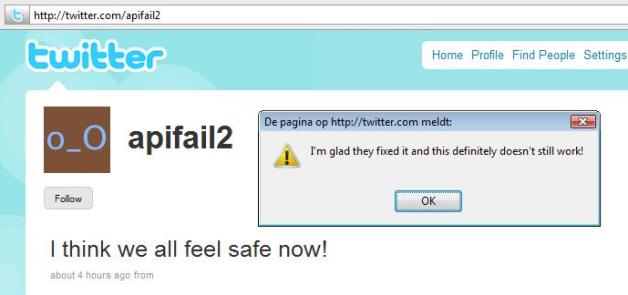
Massive Twitter Security Problem Not Resolved Just Yet
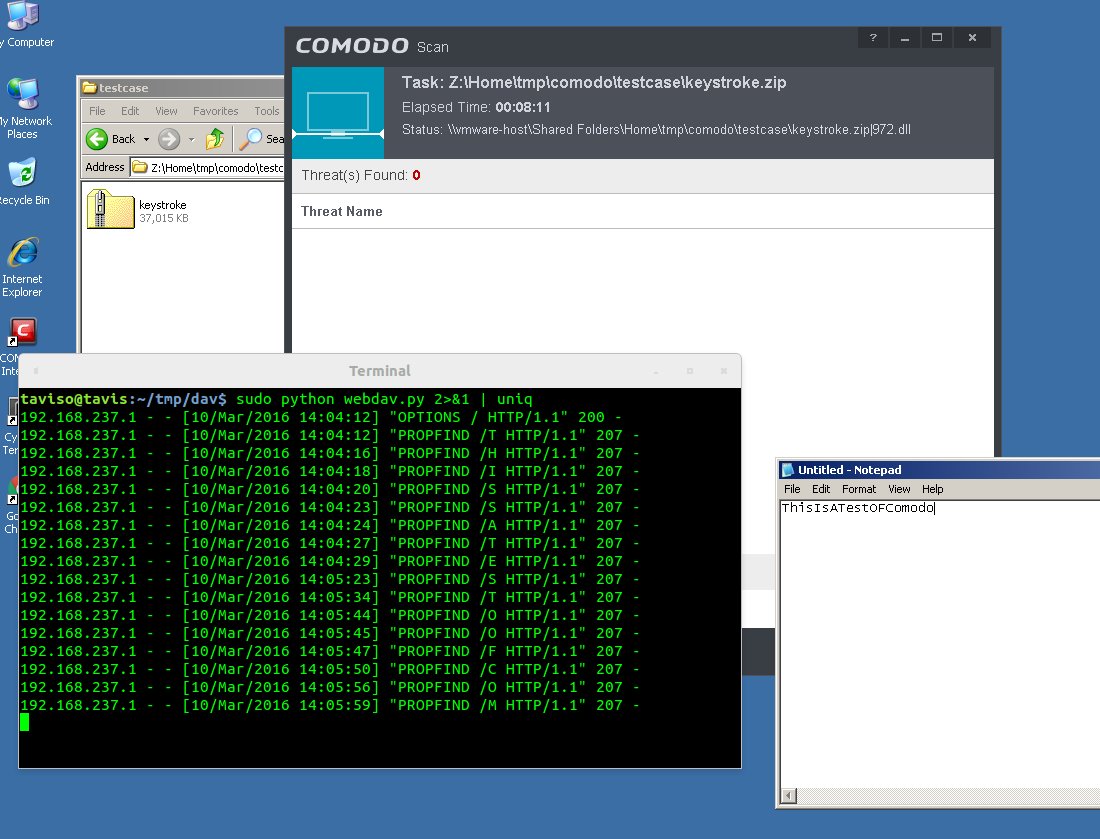
Tavis Ormandy on X: Working on an unusual exploit for Comodo Antivirus, just *scanning* a file can exfiltrate keystrokes. #wtf / X

What is the dark web and how do you access it? - Norton

Meeting Today's Biggest Cyber Threats Head-On - Business and Tech

Penetration testing toolkit, ready to use
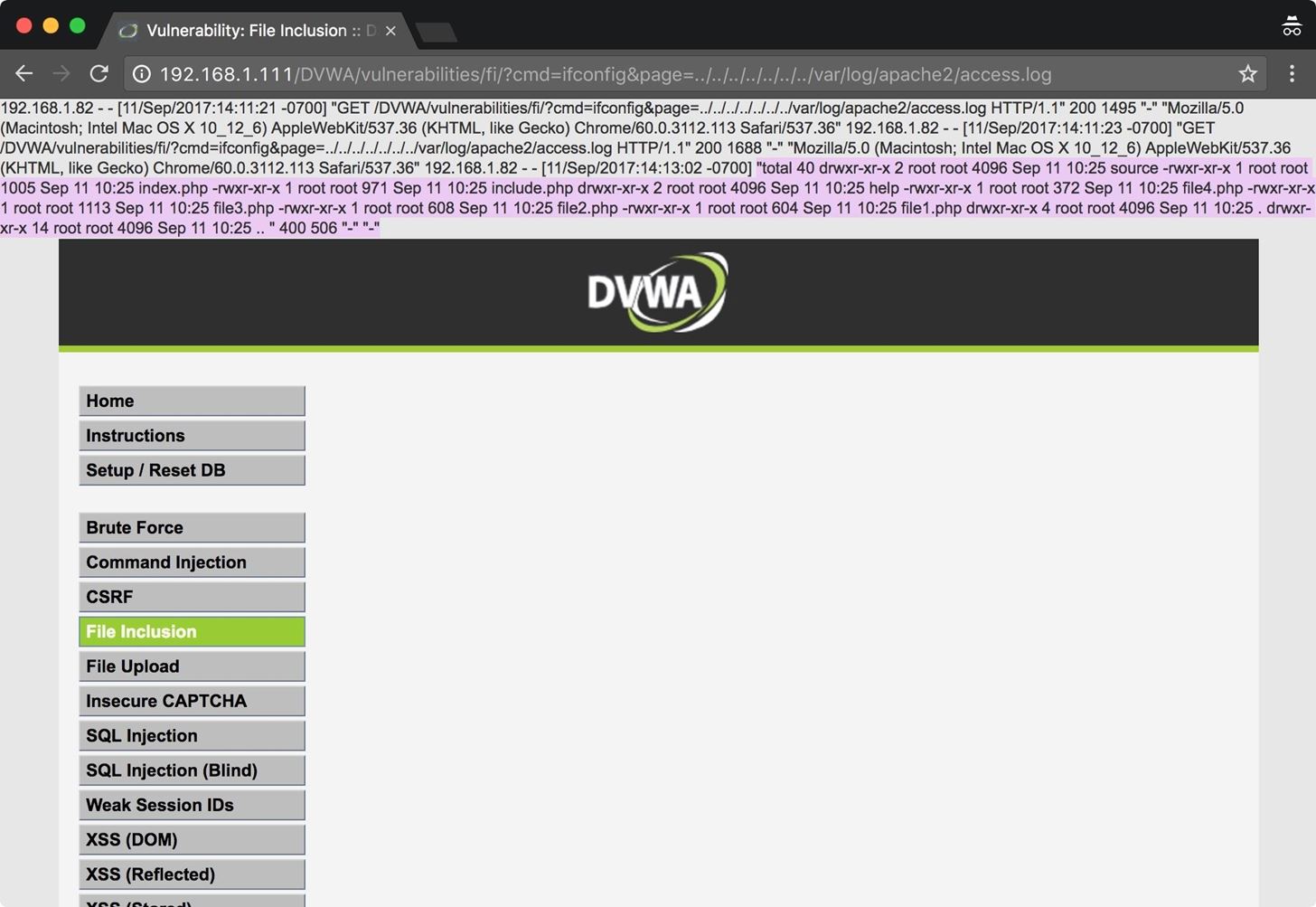
How to Exploit PHP File Inclusion in Web Apps « Null Byte :: WonderHowTo

Home Dune: Awakening

The Bruin media group internship is just a way to exploit free story shout outs from students, only with the **POSSIBILITY** OF winning $300 : r/ucla

I wanted to live in Chipping Norton – but we could only afford a shoebox
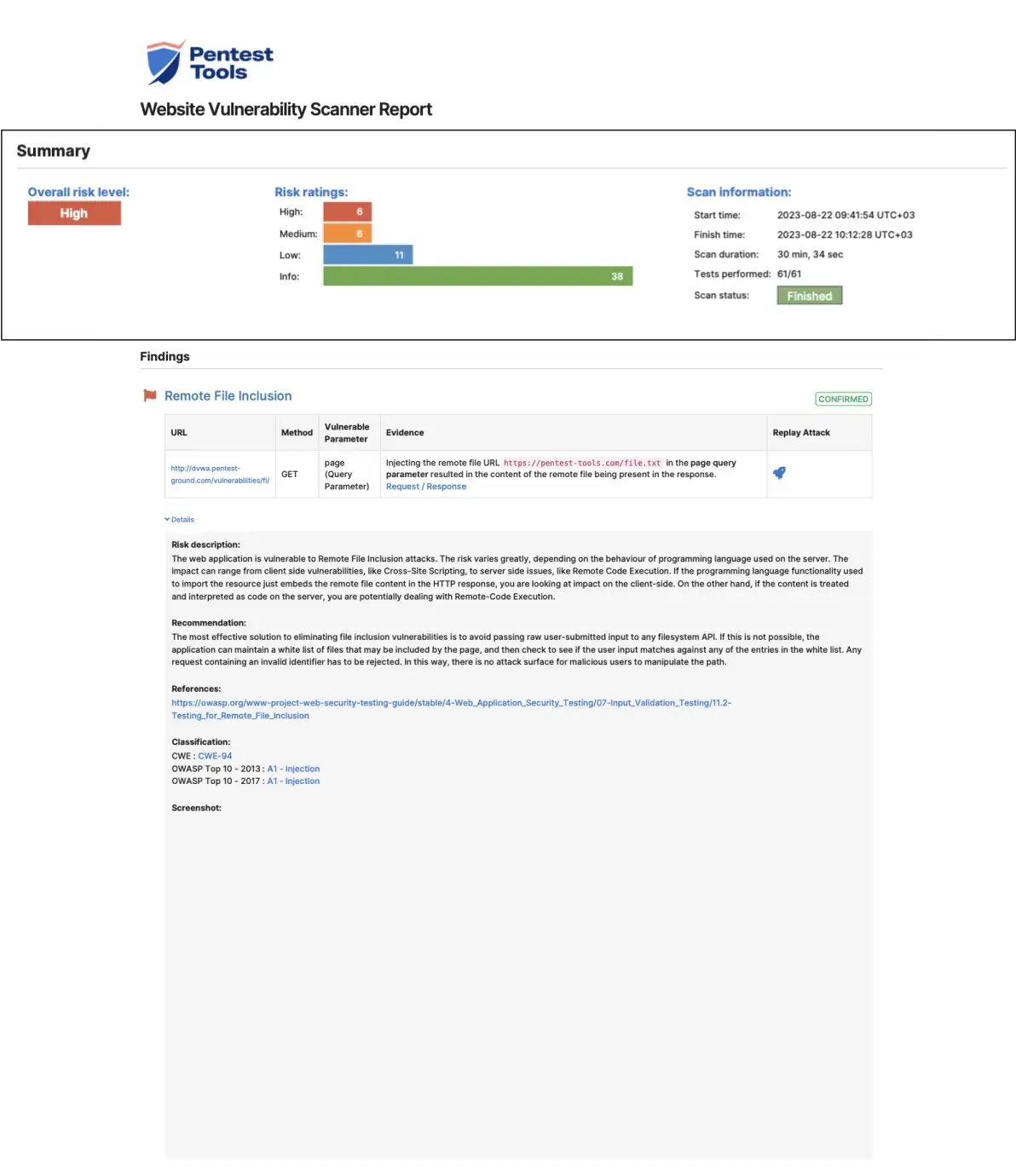
Comprehensive Web Vulnerability Scanner

Home tour Linda Olsrud Tallerud — Simply Scandi
Recomendado para você
-
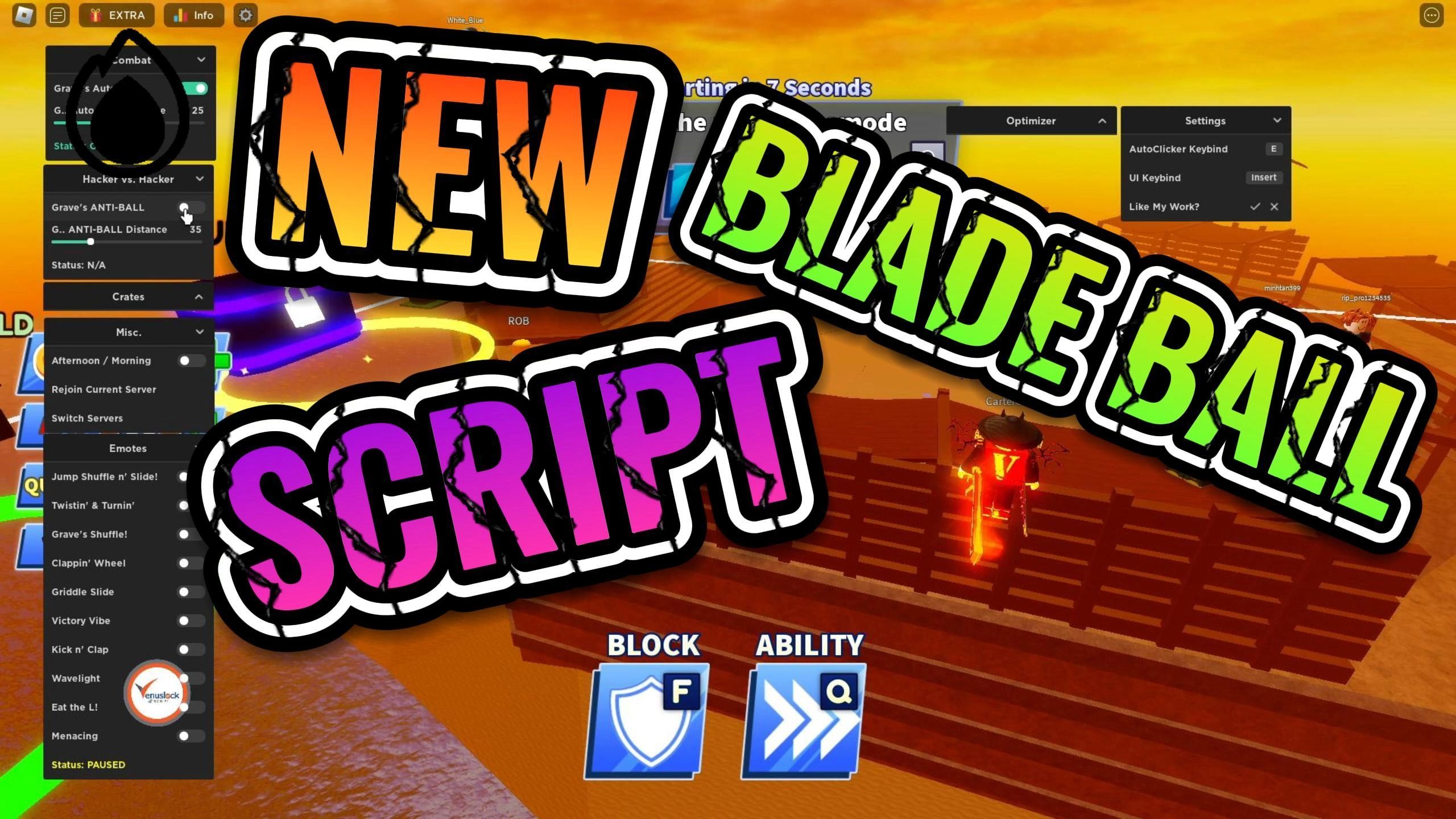 Roblox Blade Ball Script Auto Parry Hack - BiliBili16 março 2025
Roblox Blade Ball Script Auto Parry Hack - BiliBili16 março 2025 -
roblox-script · GitHub Topics · GitHub16 março 2025
-
 Pin on Jailbreak Hack Download16 março 2025
Pin on Jailbreak Hack Download16 março 2025 -
ROBLOX JAILBREAK SCRIPT OP by ItzVirii - Free download on ToneDen16 março 2025
-
 Jailbreak SCRIPT V616 março 2025
Jailbreak SCRIPT V616 março 2025 -
One Click Auto Rob Script16 março 2025
-
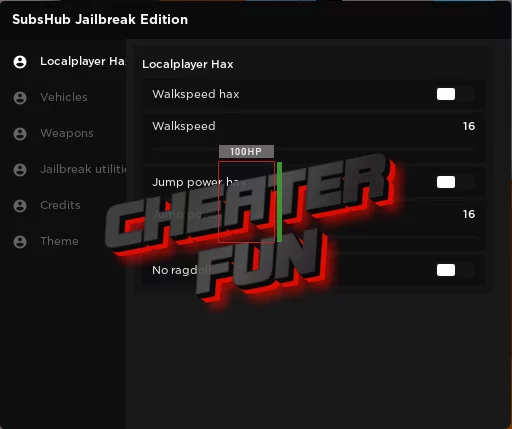 Roblox Jailbreak GUI – Weapons, Vehicles, Teleports & More – Caked16 março 2025
Roblox Jailbreak GUI – Weapons, Vehicles, Teleports & More – Caked16 março 2025 -
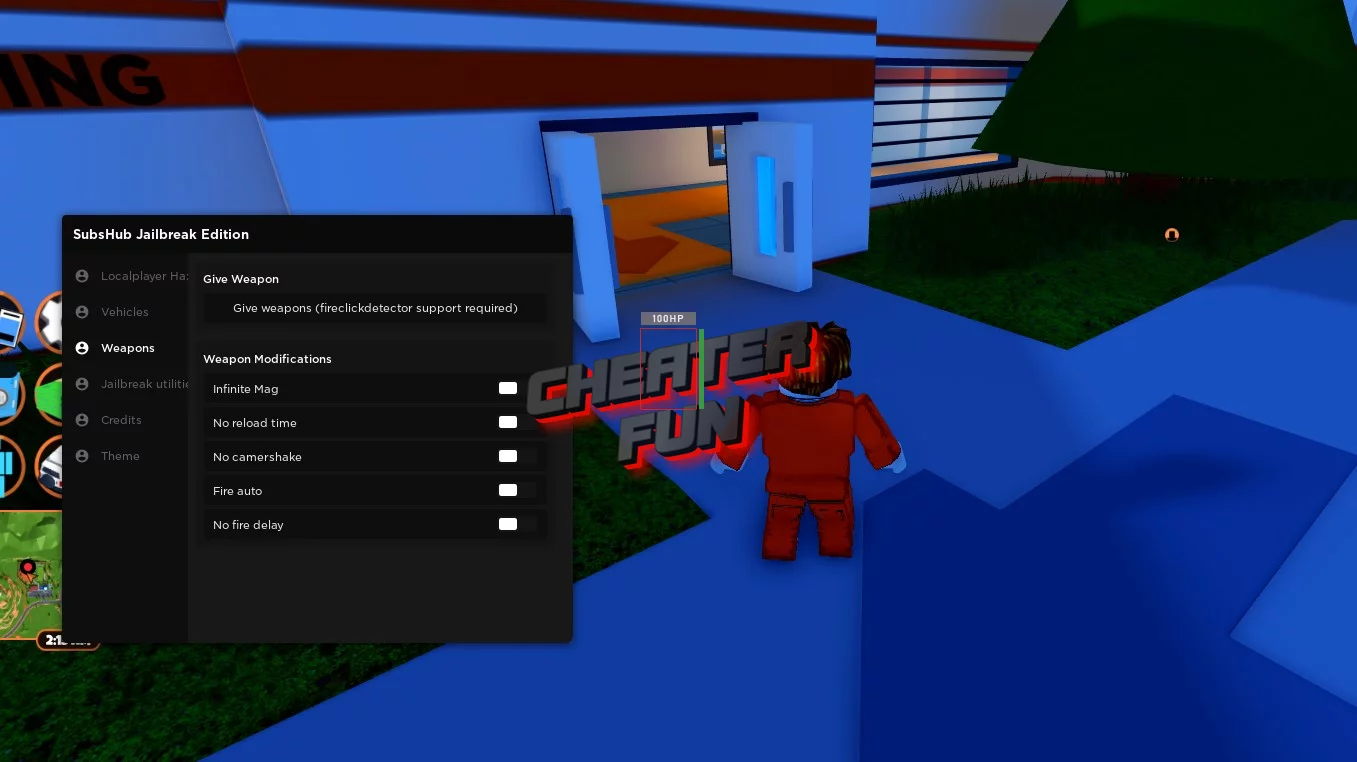 Roblox Jailbreak GUI - Weapons, Vehicles, Teleports & More16 março 2025
Roblox Jailbreak GUI - Weapons, Vehicles, Teleports & More16 março 2025 -
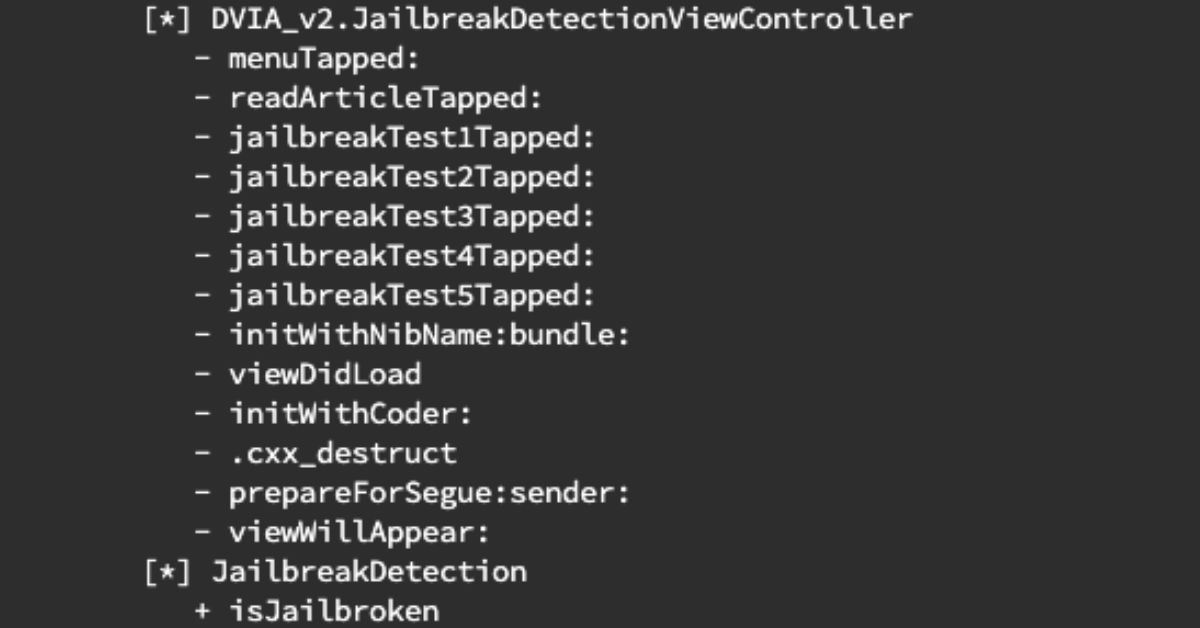 Boolean-Based iOS Jailbreak Detection Bypass with Frida16 março 2025
Boolean-Based iOS Jailbreak Detection Bypass with Frida16 março 2025 -
 Jailbreak!/transcript, Encyclopedia SpongeBobia16 março 2025
Jailbreak!/transcript, Encyclopedia SpongeBobia16 março 2025
você pode gostar
-
Sumo - Works - Tried shading on one of my gacha Ocs16 março 2025
-
outlast trials crossplay|TikTok Search16 março 2025
-
 If bendy was in the cuphead show by MerioTheCartoony on DeviantArt16 março 2025
If bendy was in the cuphead show by MerioTheCartoony on DeviantArt16 março 2025 -
 Xbox Game Pass' tem novos jogos16 março 2025
Xbox Game Pass' tem novos jogos16 março 2025 -
 TOKYO REVENGERS 2 TEMPORADA EP 11 LEGENDADO PT-BR - DATA E HORA16 março 2025
TOKYO REVENGERS 2 TEMPORADA EP 11 LEGENDADO PT-BR - DATA E HORA16 março 2025 -
 Broly's Return In Dragon Ball Super Is Every Fan's Dream Come True16 março 2025
Broly's Return In Dragon Ball Super Is Every Fan's Dream Come True16 março 2025 -
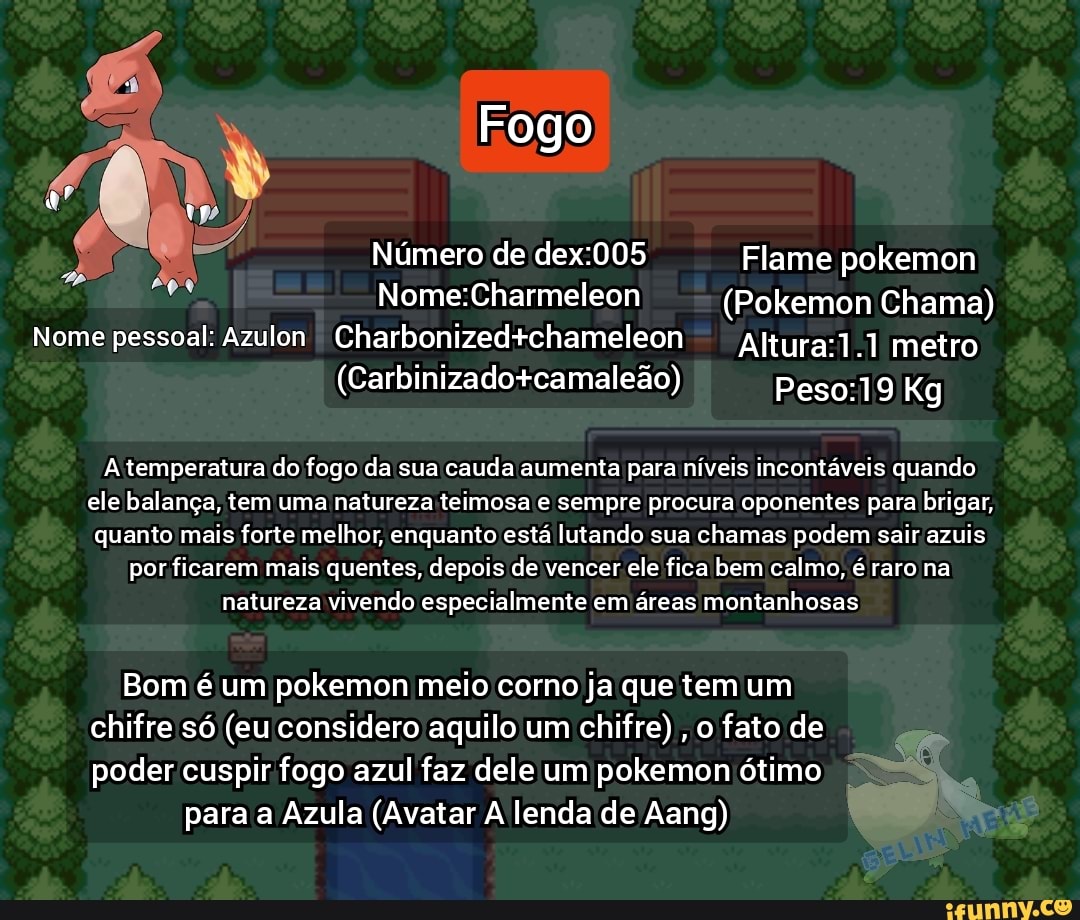 Fogo Número de Flame pokemon (Pokemon Chama) Nome pessoal: Azulon Charbonizedtchameleon metro (Carbinizadoscamaleao) Kg temperatura do16 março 2025
Fogo Número de Flame pokemon (Pokemon Chama) Nome pessoal: Azulon Charbonizedtchameleon metro (Carbinizadoscamaleao) Kg temperatura do16 março 2025 -
 Classificação dos reis Arte de anime Mozambique16 março 2025
Classificação dos reis Arte de anime Mozambique16 março 2025 -
Good Place of Animes and Games16 março 2025
-
/filters:quality(70)/n49shopv2_zanline/images/produtos/jogo-infantil-puxe-a-batatinha-frita-brinquedo-divertido-pula-batata-colorido-dican-939888694-1.jpg) Jogo Infantil Puxe a Batatinha Frita Brinquedo Divertido Pula Batata Colorido Dican16 março 2025
Jogo Infantil Puxe a Batatinha Frita Brinquedo Divertido Pula Batata Colorido Dican16 março 2025


