Hackers Target Gamers With Microsoft-Signed Rootkit
Por um escritor misterioso
Last updated 25 março 2025

Kernel mode driver can download second-stage payload directly to memory, allowing threat actors to evade endpoint detection and response tools.

Microsoft Signed Rootkit Malware That Spreads Through Gaming

Driving Through Defenses Targeted Attacks Leverage Signed
Chinese Hackers Utilize Microsoft Signed Rootkit To Target The

Hackers Target Reddit Alternative Lemmy via Zero-Day Vulnerability

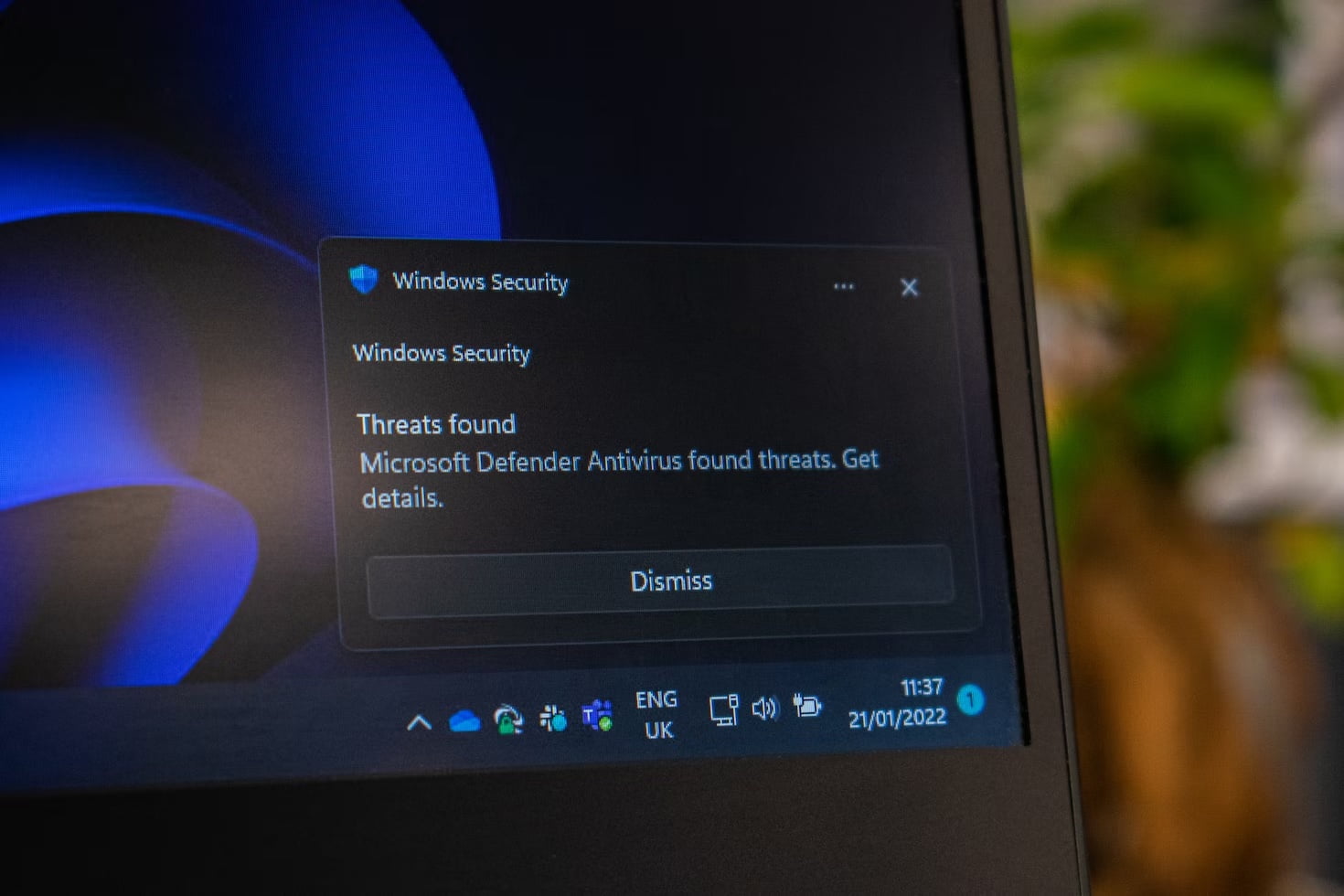
Microsoft admits signing a software driver loaded with rootkit malware

Microsoft accidentally signed a gaming driver containing rootkit
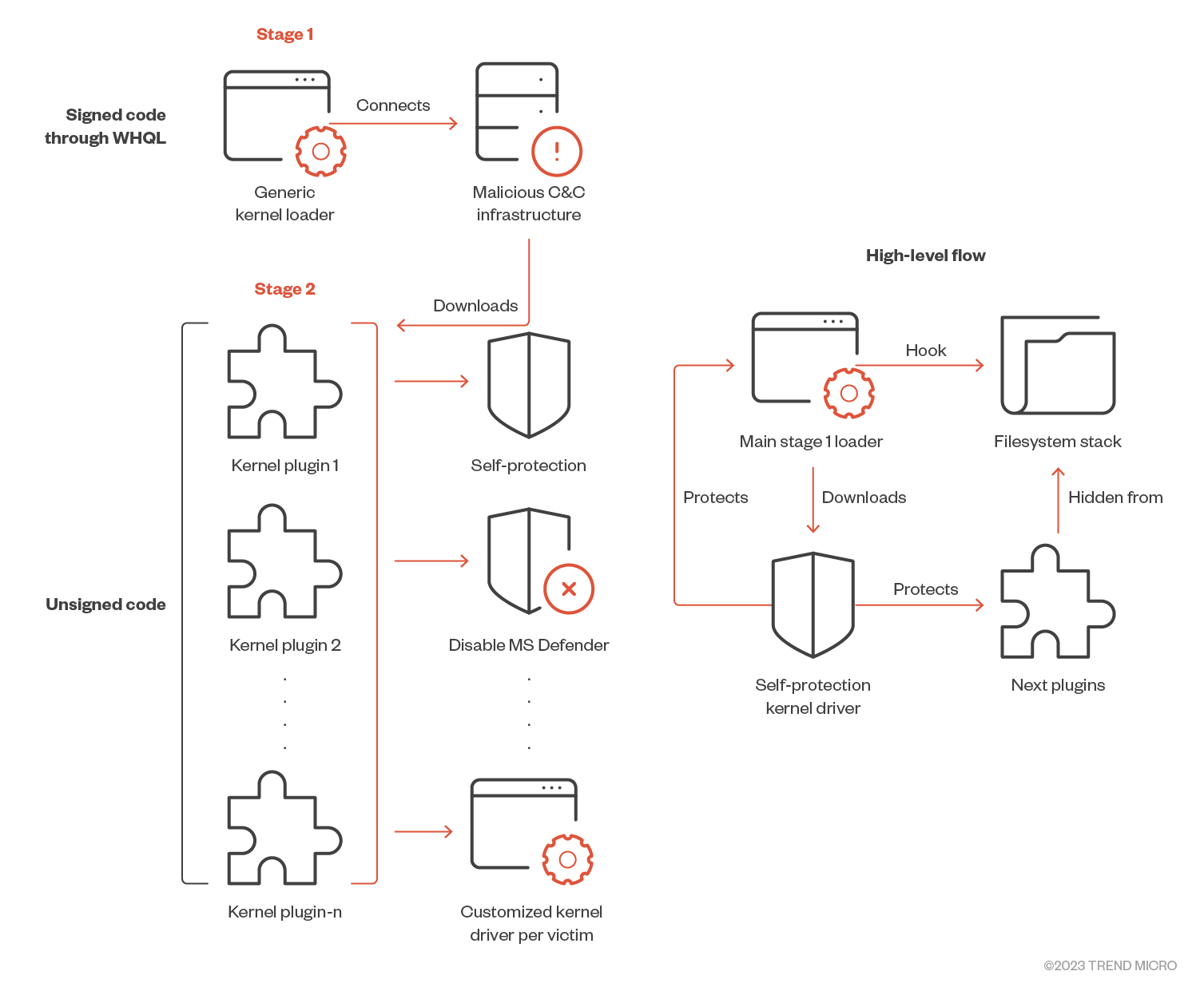
Hunting for A New Stealthy Universal Rootkit Loader

Netfilter Rootkit Malware Targets the Gaming Community: Microsoft

Breach Alert: Gaming Host & Shadow PC Malware Attack
Investigating Fivesys And Microsoft's Digital Seal— Auslogics Blog

Netfilter Rootkit Malware Targets the Gaming Community: Microsoft

Chinese Hackers Are Abusing Log4Shell to Deploy Rootkits

How to detect & prevent rootkits
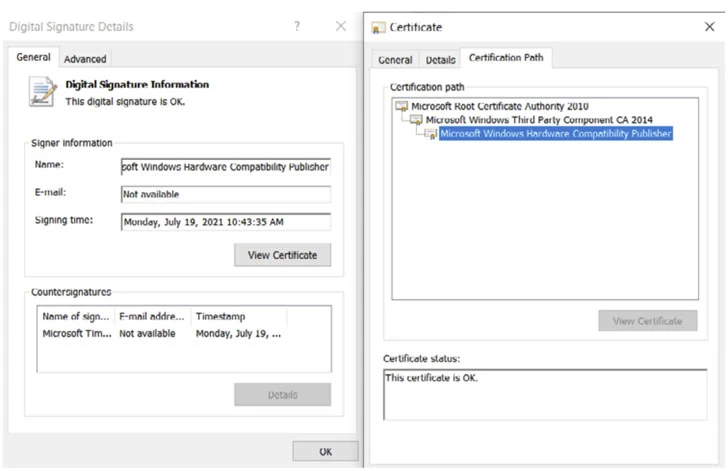
Researchers Discover Microsoft-Signed FiveSys Rootkit in the Wild
Recomendado para você
-
 Roblox (@Roblox) / X25 março 2025
Roblox (@Roblox) / X25 março 2025 -
 Hack The Box (@hackthebox_eu) / X25 março 2025
Hack The Box (@hackthebox_eu) / X25 março 2025 -
 The *NEWEST* Roblox HACKER in 2023?! 😲25 março 2025
The *NEWEST* Roblox HACKER in 2023?! 😲25 março 2025 -
 Roblox data breach exposes developer data25 março 2025
Roblox data breach exposes developer data25 março 2025 -
 Roblox hack: User data leaked online after failed extortion attack25 março 2025
Roblox hack: User data leaked online after failed extortion attack25 março 2025 -
 Every day hacking, Roblox Creepypasta Wiki25 março 2025
Every day hacking, Roblox Creepypasta Wiki25 março 2025 -
 Here's How Hackers Steal Your Password and How You Can Create a Safer One25 março 2025
Here's How Hackers Steal Your Password and How You Can Create a Safer One25 março 2025 -
Is label in Roblox a hacker|TikTok Search25 março 2025
-
Minecraft: Kaspersky reports growth in gamer cyberattacks in 202325 março 2025
-
 Hacktivism in the Israel-Hamas Conflict25 março 2025
Hacktivism in the Israel-Hamas Conflict25 março 2025
você pode gostar
-
 How to download GTAV in PPSSPP Emulator 2020!! Working 100%25 março 2025
How to download GTAV in PPSSPP Emulator 2020!! Working 100%25 março 2025 -
/cdn.vox-cdn.com/uploads/chorus_asset/file/23174426/TheCupheadShow__Season1_Episode2_00_00_34_0920220105_5654_7th525.jpg) The Cuphead Show! gets wild trailer and timely Netflix release date - Polygon25 março 2025
The Cuphead Show! gets wild trailer and timely Netflix release date - Polygon25 março 2025 -
 FC Alania Vladikavkaz - Wikiwand25 março 2025
FC Alania Vladikavkaz - Wikiwand25 março 2025 -
 Technology News, Online Marketplace OLX Group To Slash Over 1,500 Jobs Globally25 março 2025
Technology News, Online Marketplace OLX Group To Slash Over 1,500 Jobs Globally25 março 2025 -
 Wall Art Print, 1966 Set of Chess Pieces Patent25 março 2025
Wall Art Print, 1966 Set of Chess Pieces Patent25 março 2025 -
 All Rebirth Champions X Balloon Locations (2023) - Complete Guide25 março 2025
All Rebirth Champions X Balloon Locations (2023) - Complete Guide25 março 2025 -
 How to Download Garten of Banban on Android25 março 2025
How to Download Garten of Banban on Android25 março 2025 -
 Puer faca de chá curiosos aço inoxidável cortador de chá inserção artesanal sândalo kung fu chá faca cerimônia te verde chino teaware - AliExpress25 março 2025
Puer faca de chá curiosos aço inoxidável cortador de chá inserção artesanal sândalo kung fu chá faca cerimônia te verde chino teaware - AliExpress25 março 2025 -
 ArtStation - Everywhere at the End of Time fanart25 março 2025
ArtStation - Everywhere at the End of Time fanart25 março 2025 -
Jenny Wakeman - XJ-9 (VRchat Avatar)25 março 2025

