Using Web Application Firewall at container-level for network-based threats
Por um escritor misterioso
Last updated 15 julho 2024
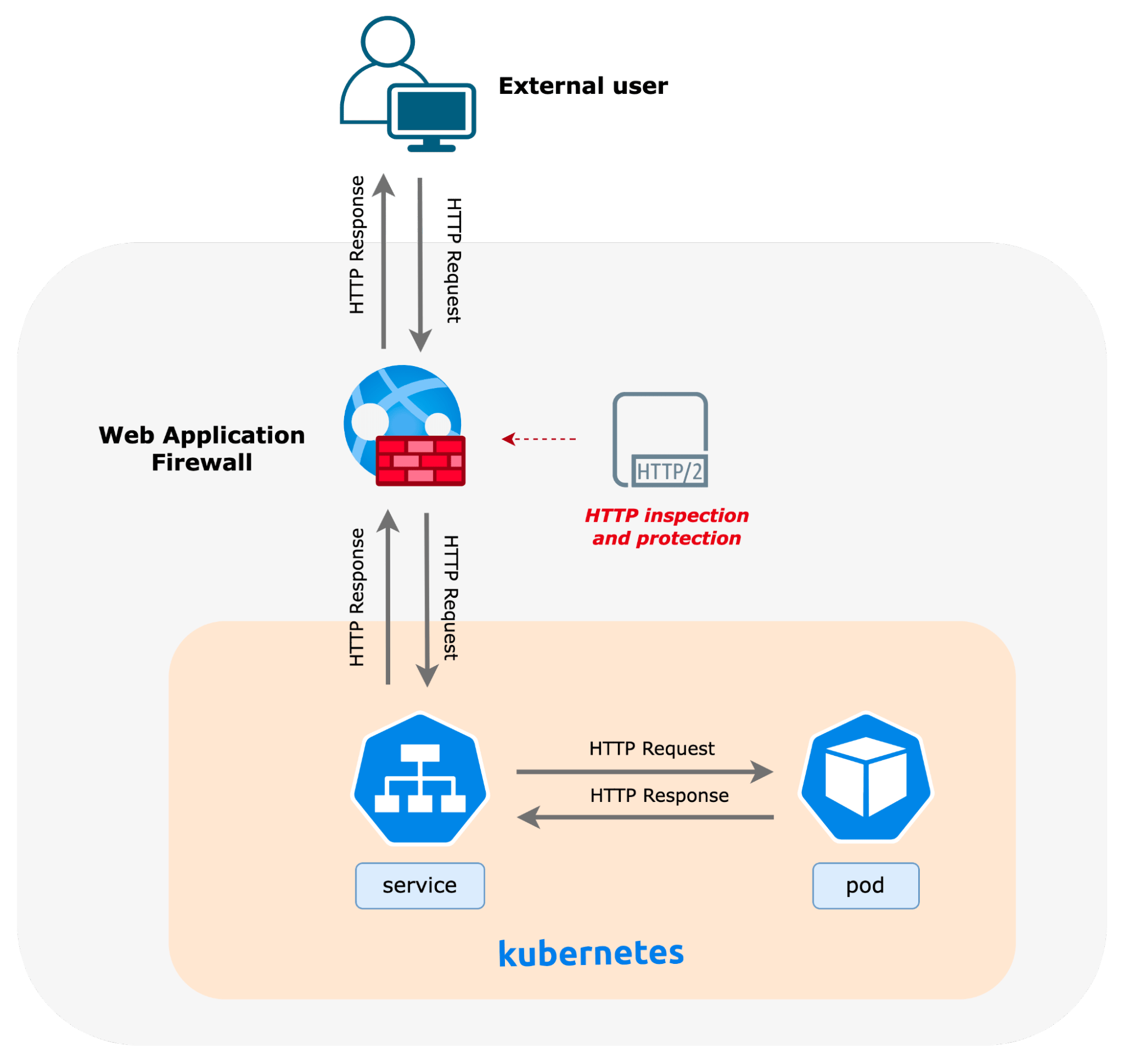
The microservices architecture provides developers and DevOps engineers significant agility that helps them move at the pace of the business. Breaking monolithic applications into smaller components accelerates development, streamlines scaling, and improves fault isolation. However
Imperva Web Application Firewall (WAF)
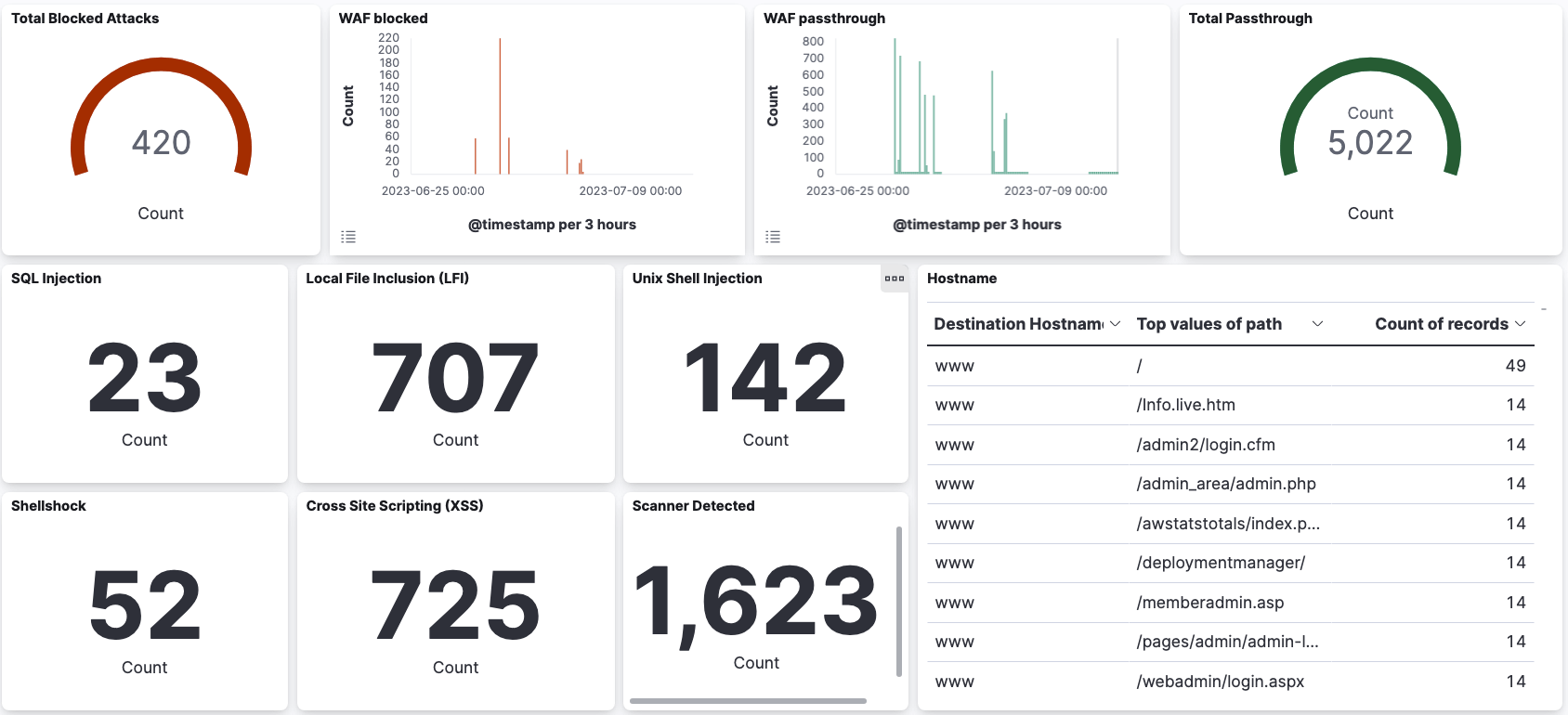
Using Web Application Firewall at container-level for network-based threats
BIG-IP Advanced WAF
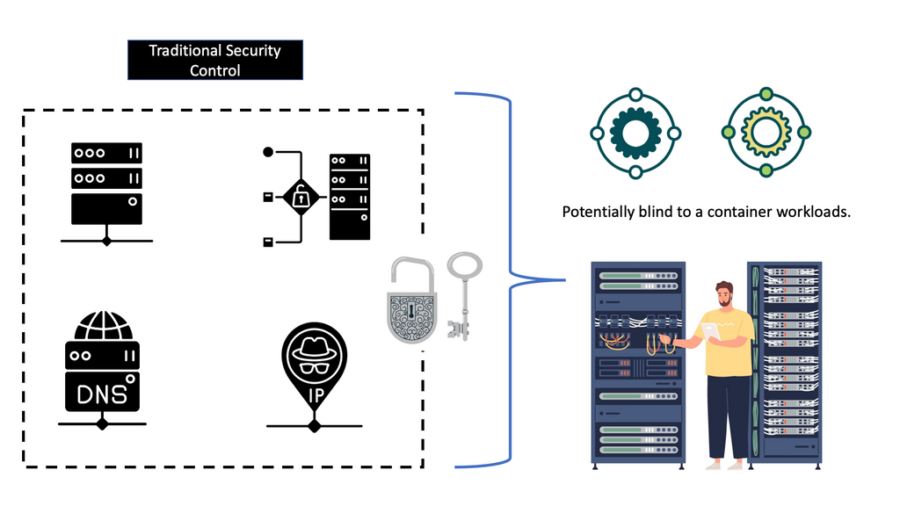
Docker Security Options
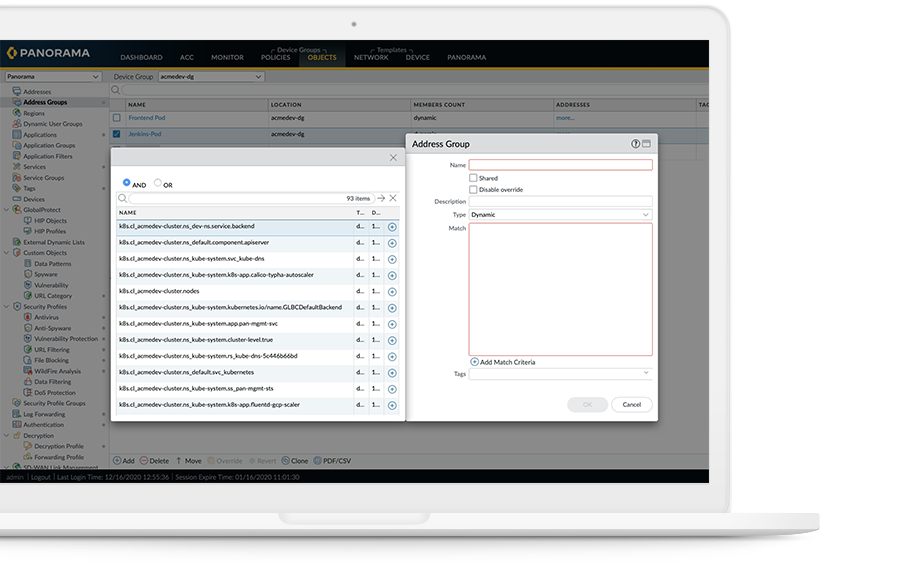
CN-Series Container Firewalls for Kubernetes - Palo Alto Networks
Imperva Web Application Firewall (WAF)
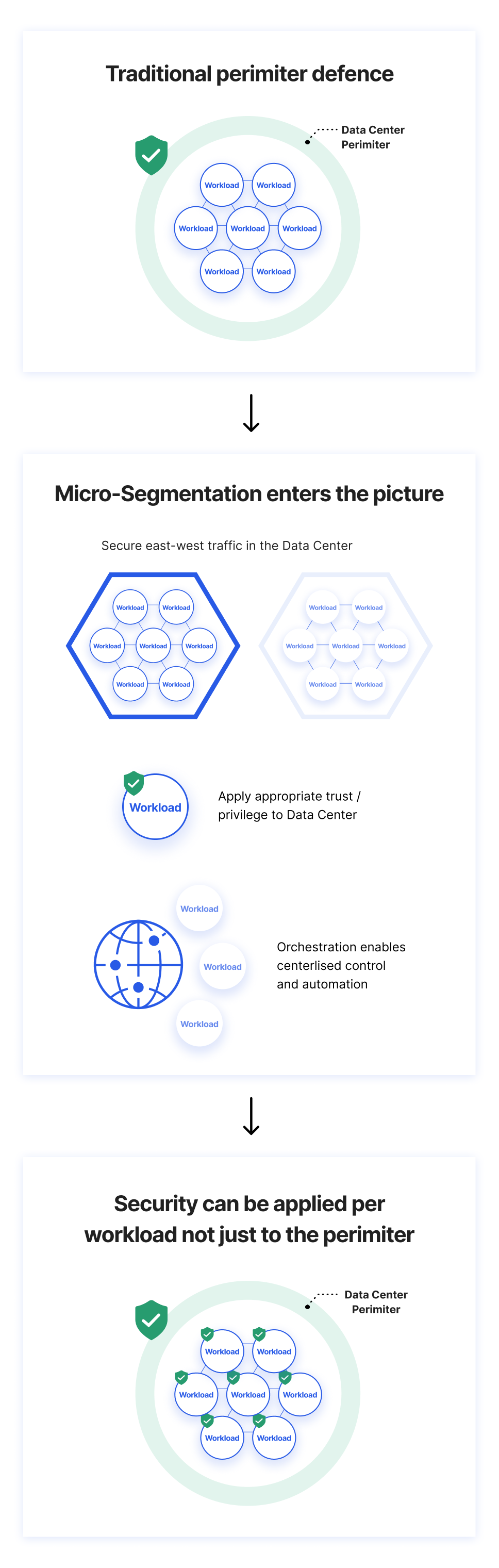
What is Micro-Segmentation?, Security Best Practices

CYBER SECURITY True Digital Group

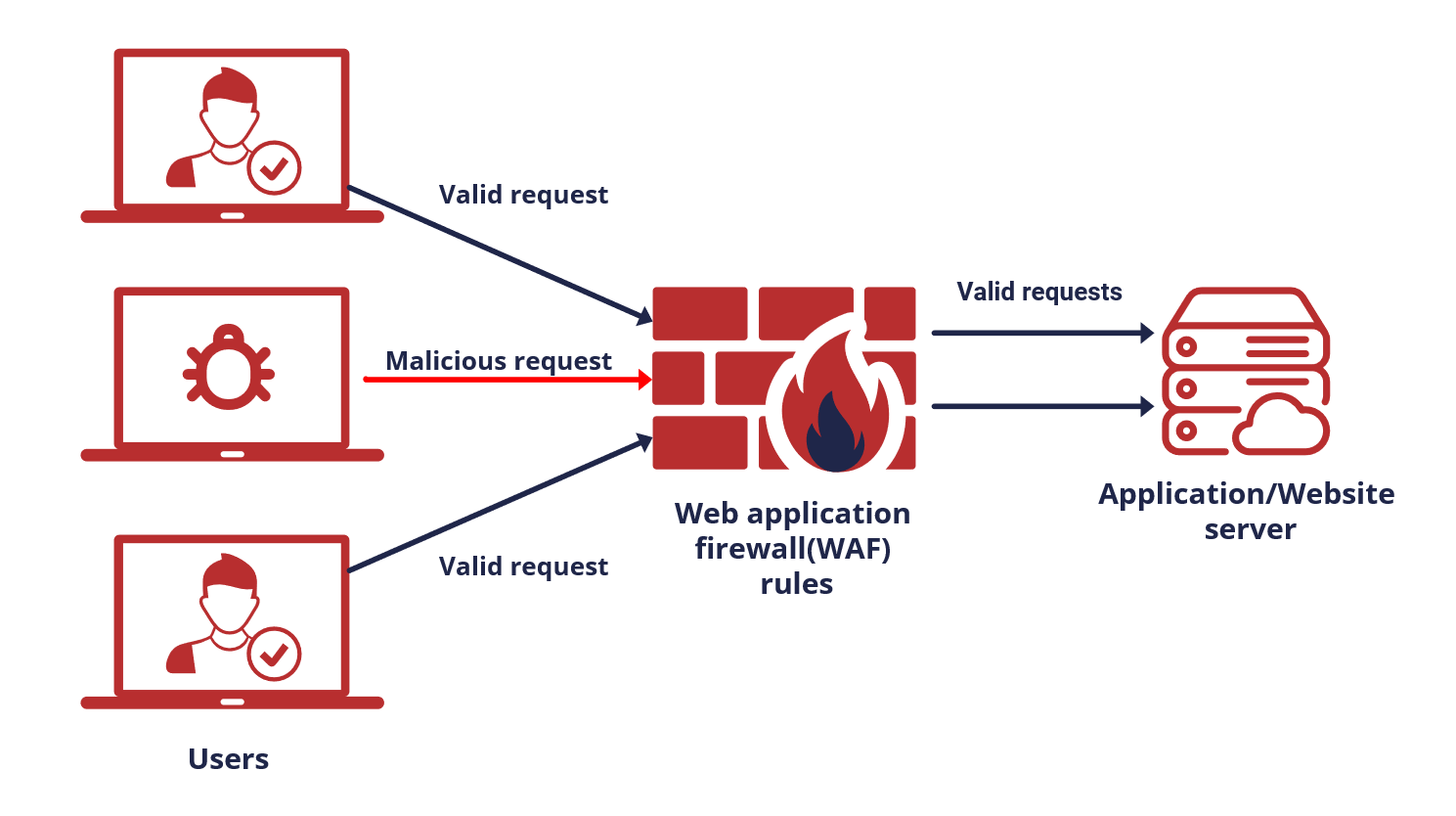
Web Application Firewall (WAF) vs Network Firewall : Know the difference - IP With Ease
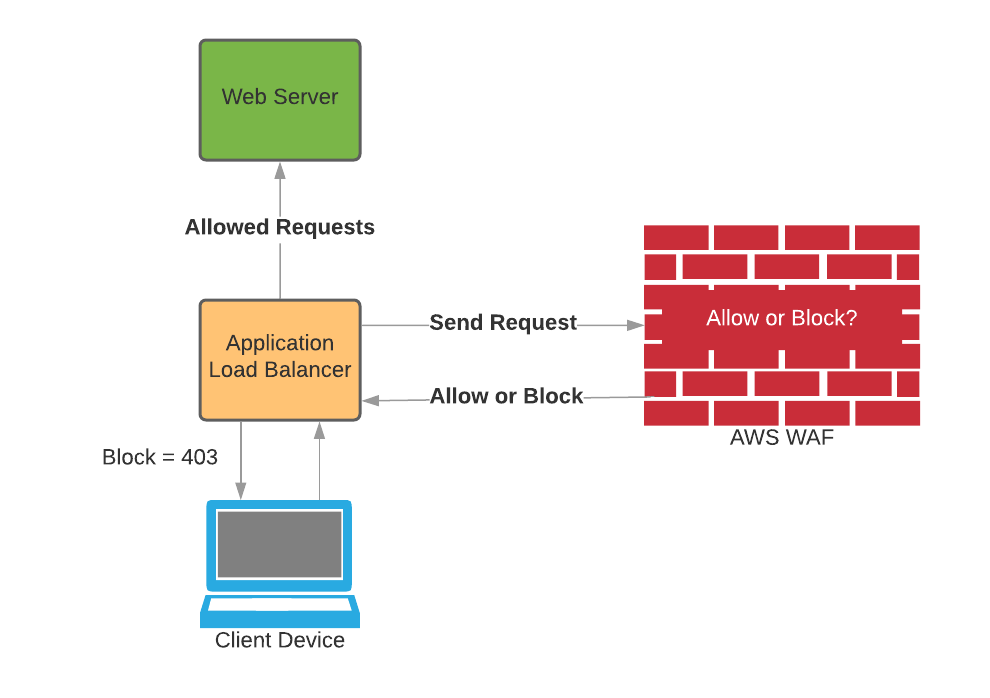
Deep Dive Into The AWS Web Application Firewall (WAF), by Daniel Glucksman
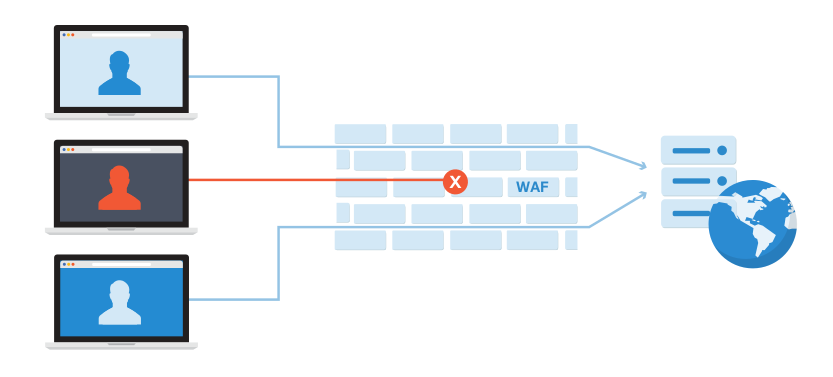
WAF configuration with NLB, EKS, Digital ocean, GKE, Nginx ingress, by vishal acharya
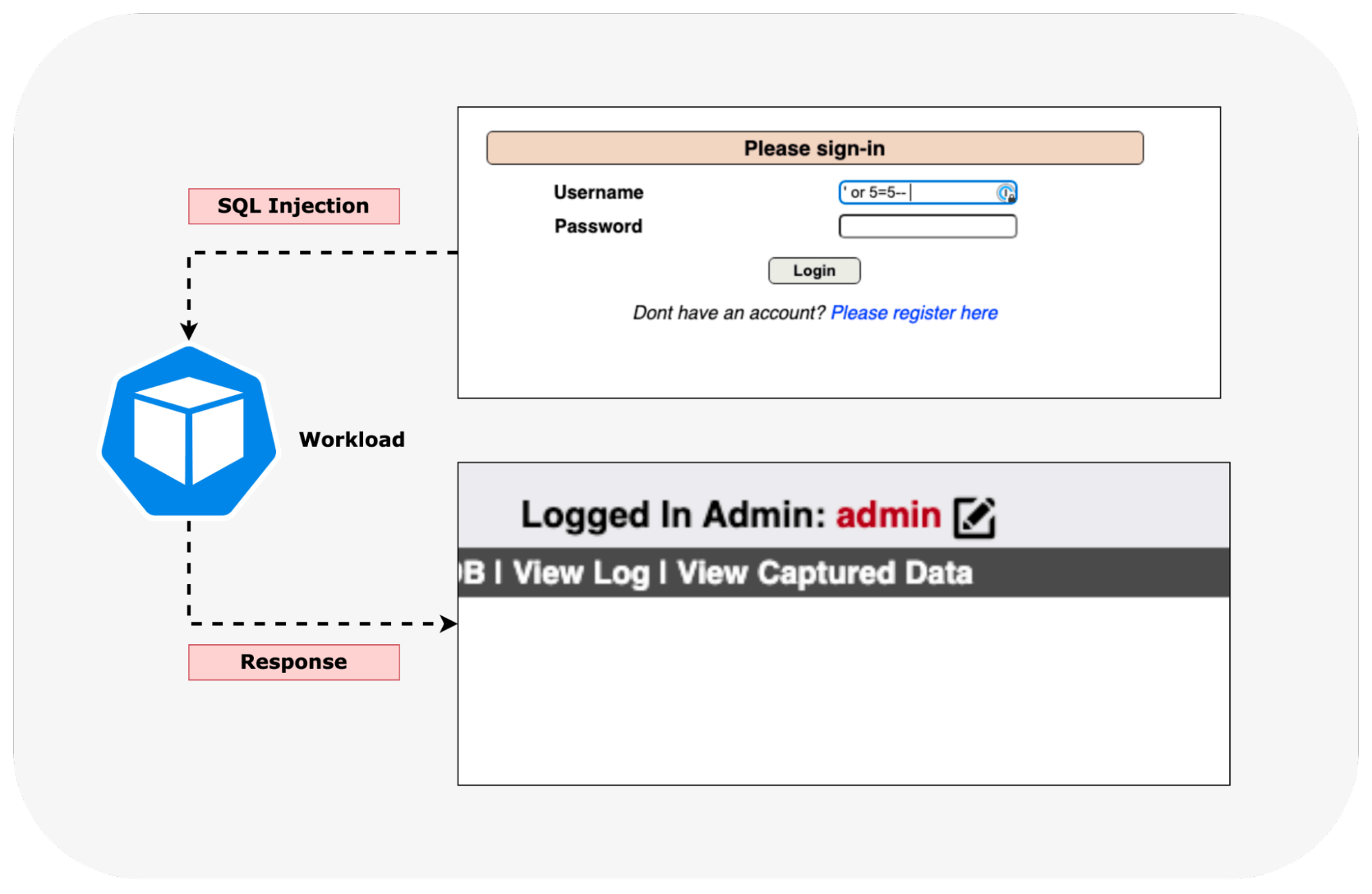
Using Web Application Firewall at container-level for network-based threats
Recomendado para você
-
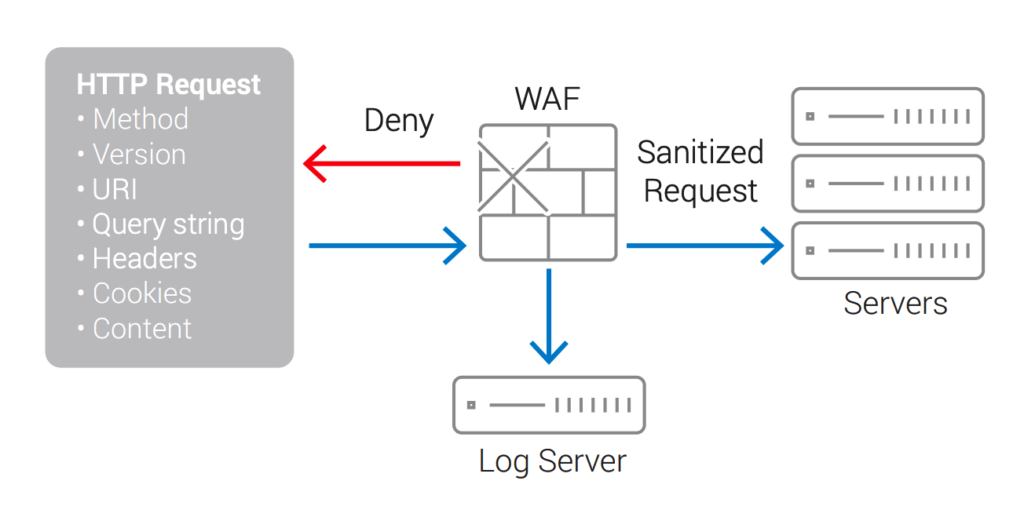 What is a Web Application Firewall (WAF)?, Glossary15 julho 2024
What is a Web Application Firewall (WAF)?, Glossary15 julho 2024 -
 What is a Web Application Firewall (WAF)15 julho 2024
What is a Web Application Firewall (WAF)15 julho 2024 -
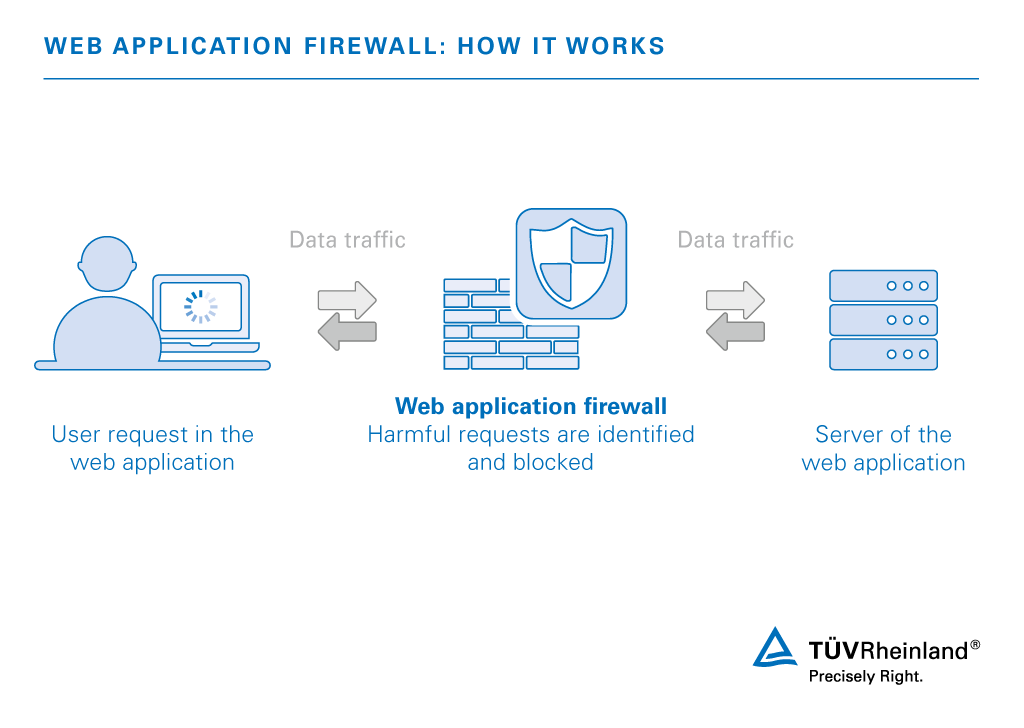 Web Application Firewall (WAF) Service, IQ15 julho 2024
Web Application Firewall (WAF) Service, IQ15 julho 2024 -
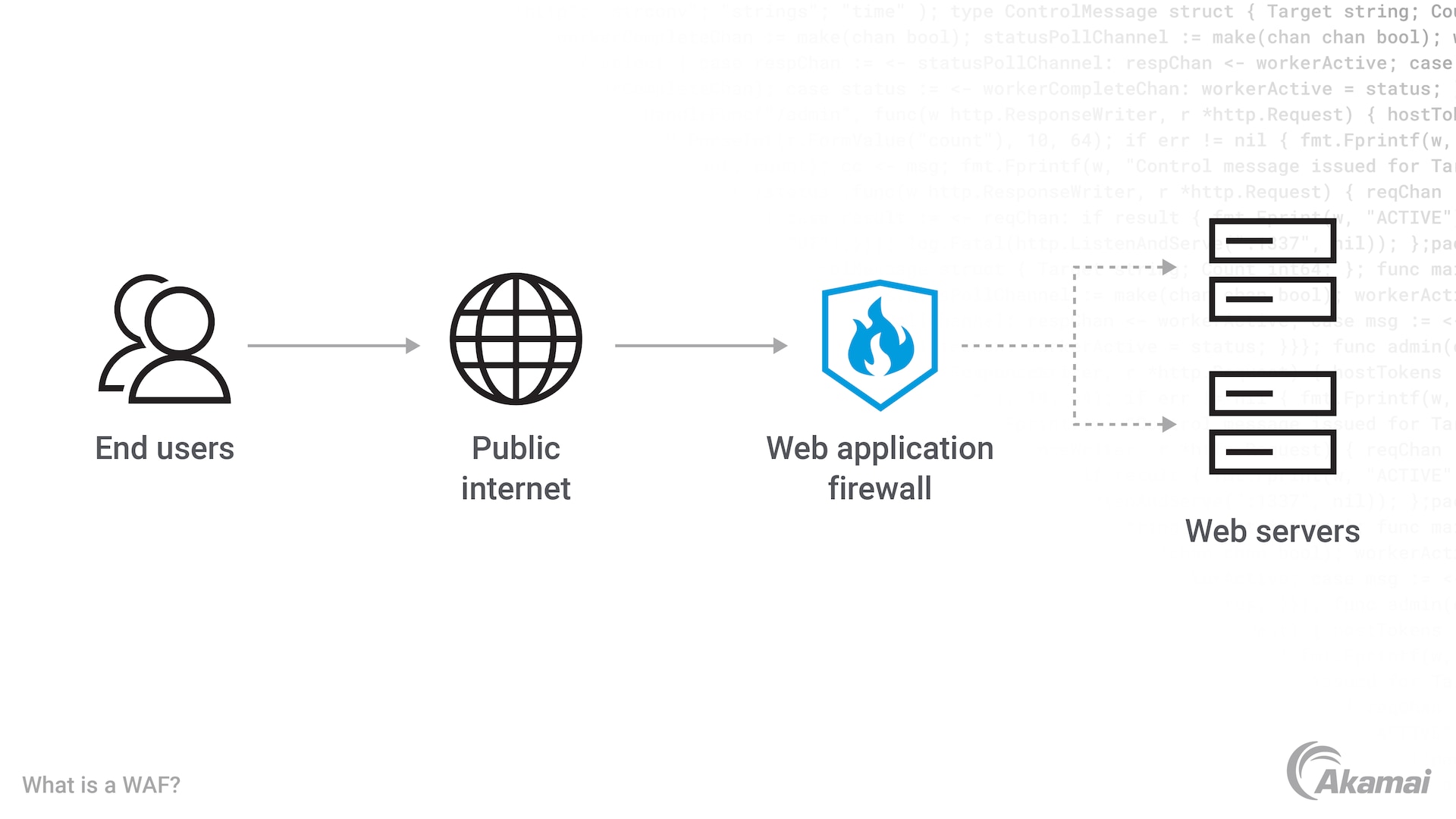 What Is a Web Application Firewall (WAF)?15 julho 2024
What Is a Web Application Firewall (WAF)?15 julho 2024 -
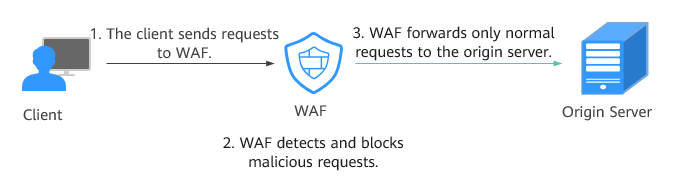 What Is Web Application Firewall?_Web Application Firewall_Service Overview_Huawei Cloud15 julho 2024
What Is Web Application Firewall?_Web Application Firewall_Service Overview_Huawei Cloud15 julho 2024 -
 Imperva Web Application Firewall (WAF)15 julho 2024
Imperva Web Application Firewall (WAF)15 julho 2024 -
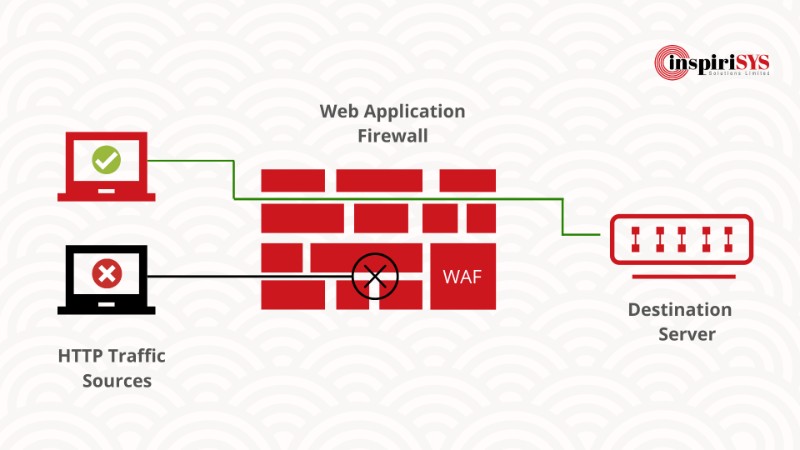 Benefits of using Web Application Firewall (WAF)15 julho 2024
Benefits of using Web Application Firewall (WAF)15 julho 2024 -
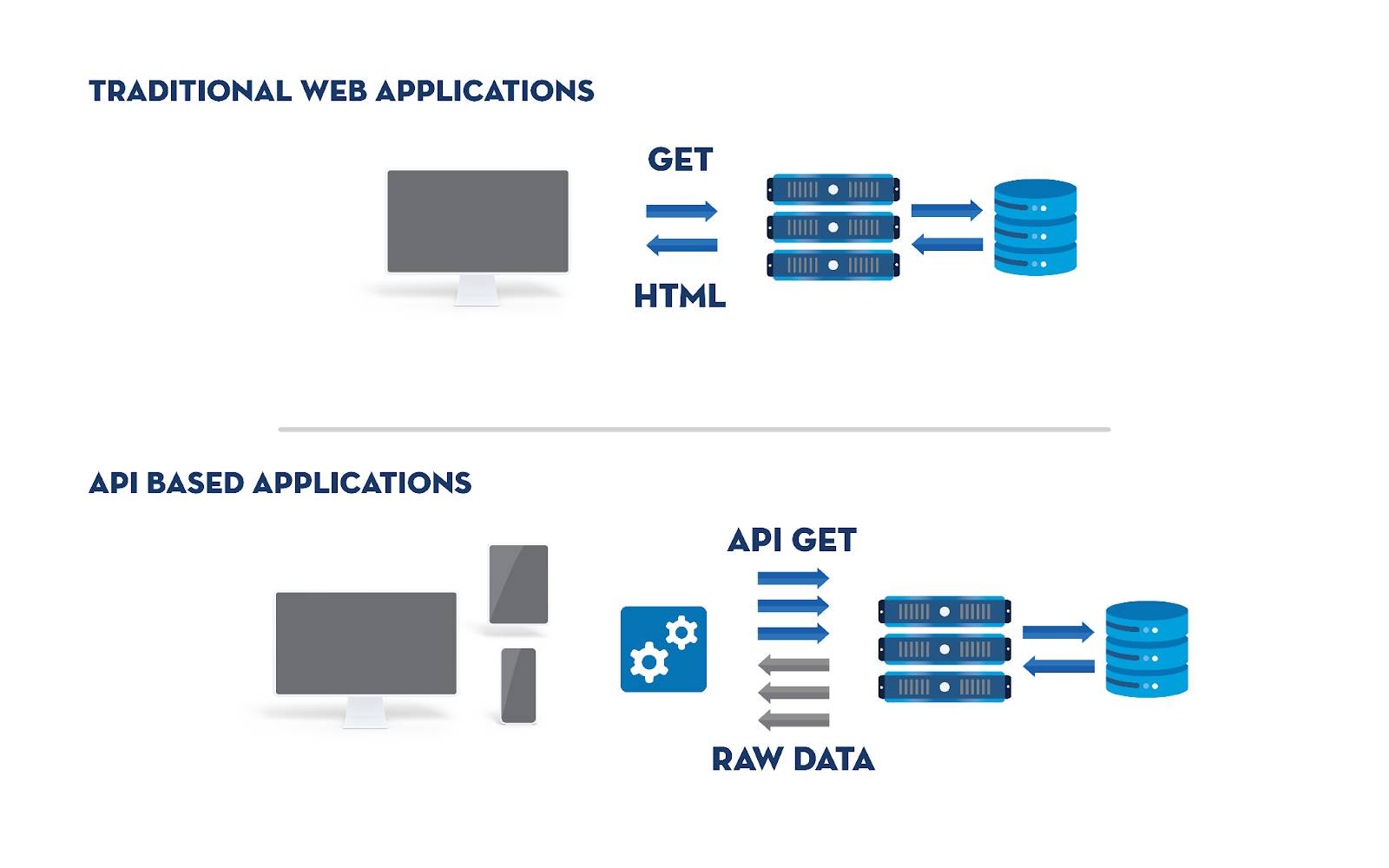 Learn How Web Application Firewalls Protect APIs Unit15 julho 2024
Learn How Web Application Firewalls Protect APIs Unit15 julho 2024 -
![What is a Web Application Firewall (WAF) ? Types & Benefits of Web Application Firewalls [2021 Update]](https://www.datalinknetworks.net/hs-fs/hubfs/Types%20of%20WAFs-png.png?width=1459&name=Types%20of%20WAFs-png.png) What is a Web Application Firewall (WAF) ? Types & Benefits of Web Application Firewalls [2021 Update]15 julho 2024
What is a Web Application Firewall (WAF) ? Types & Benefits of Web Application Firewalls [2021 Update]15 julho 2024 -
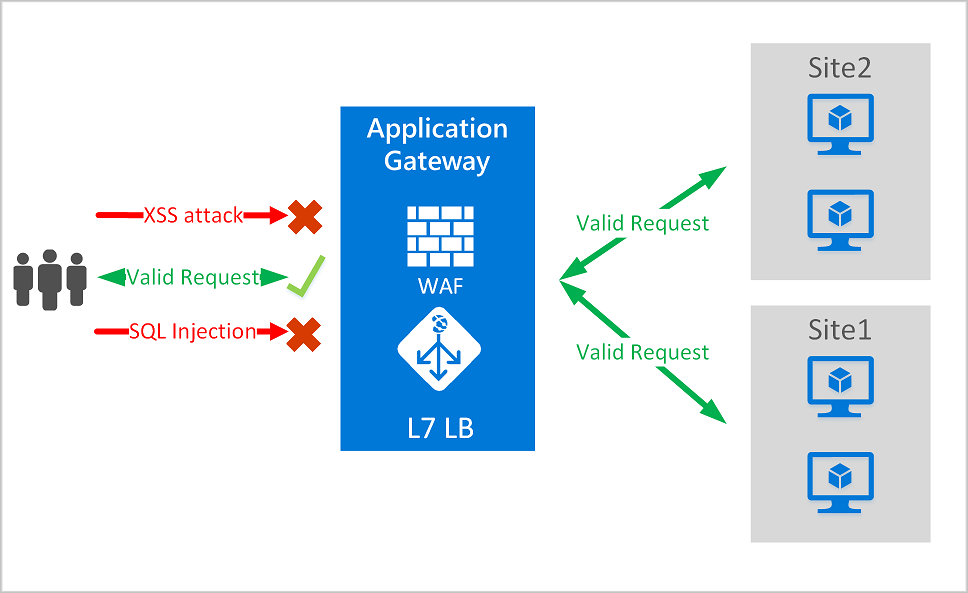 What is Azure Web Application Firewall on Azure Application15 julho 2024
What is Azure Web Application Firewall on Azure Application15 julho 2024
você pode gostar
-
fotos raras da luluca 2021|Pesquisa do TikTok15 julho 2024
-
 Valkyria Anime-Planet15 julho 2024
Valkyria Anime-Planet15 julho 2024 -
 Todos os estádios disponíveis no Fifa 22 – Tecnoblog15 julho 2024
Todos os estádios disponíveis no Fifa 22 – Tecnoblog15 julho 2024 -
Scream 6' Writers on Why Chad Survived Near-Fatal Attack by Ghostface15 julho 2024
-
 Runden on Planet Minecraft15 julho 2024
Runden on Planet Minecraft15 julho 2024 -
 O Metaverso - Um mundo para além daquele em que vivemos15 julho 2024
O Metaverso - Um mundo para além daquele em que vivemos15 julho 2024 -
 Batman: Arkham City - Trophies (Two Face), Another guide wi…15 julho 2024
Batman: Arkham City - Trophies (Two Face), Another guide wi…15 julho 2024 -
 Eu Amo Poços de Caldas / Xadrez Gigante15 julho 2024
Eu Amo Poços de Caldas / Xadrez Gigante15 julho 2024 -
 One Punch Man Season 3 : Release Date and Other Information You Want To Know15 julho 2024
One Punch Man Season 3 : Release Date and Other Information You Want To Know15 julho 2024 -
 El press francés, Desarrolla tus triceps con este ejercicio, Eurofitness15 julho 2024
El press francés, Desarrolla tus triceps con este ejercicio, Eurofitness15 julho 2024
