Detecting Linux Anti-Forensics: Timestomping
Por um escritor misterioso
Last updated 24 março 2025
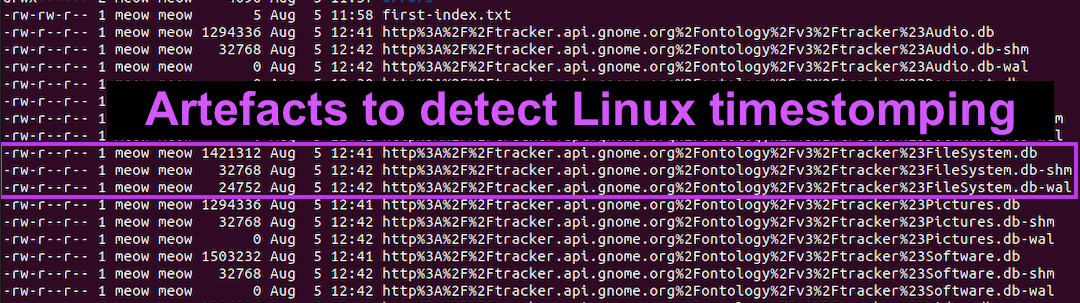
#160; Threat actors can modify the timestamps on malicious files to evade detection. This technique has been used time and time again across va
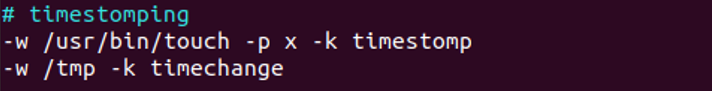
Detecting Linux Anti-Forensics: Timestomping
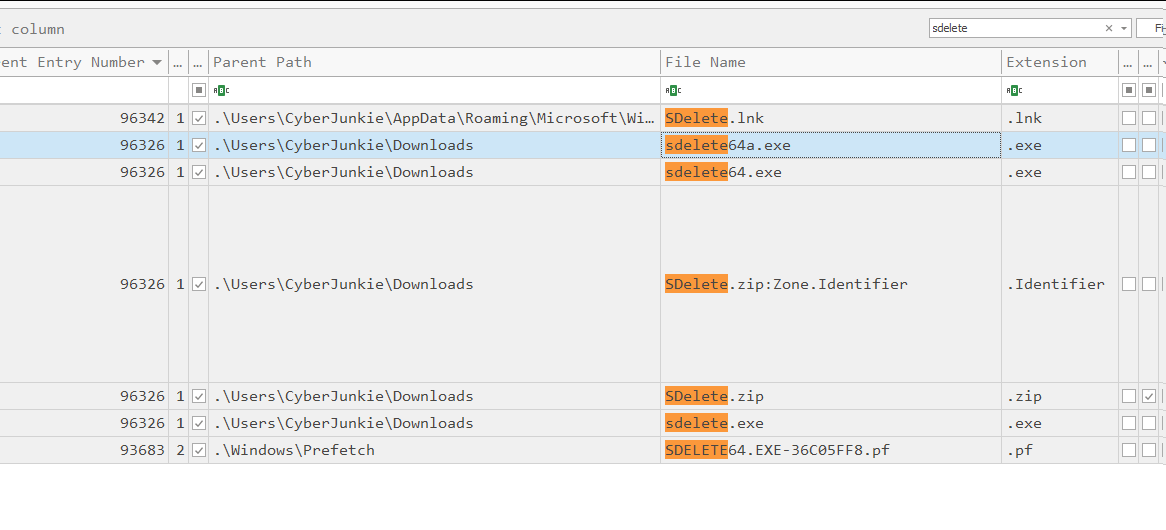
5 anti-forensics techniques to trick investigators (+ examples

Anti-forensics: Furthering digital forensic science through a new

Anti-forensics in ext4: On secrecy and usability of timestamp

Anti-forensic - wstęp i timestomping
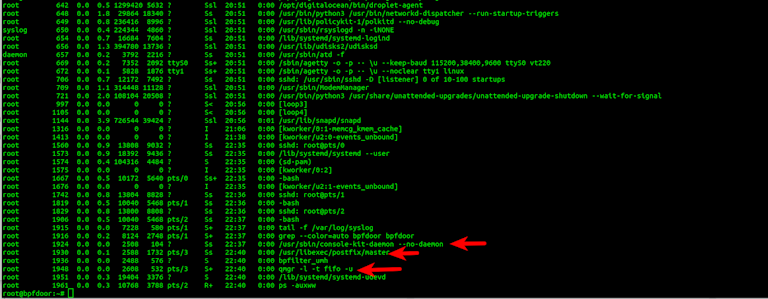
BPFDoor - An Evasive Linux Backdoor Technical Analysis

Wiping Techniques and Anti-Forensics Methods

Wiping Techniques and Anti-Forensics Methods
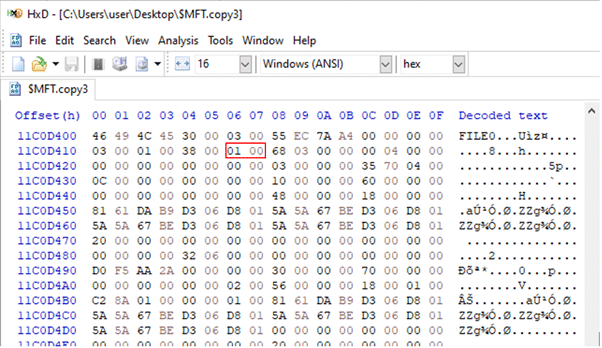
Anti-Forensics Techniques - Cynet
Recomendado para você
-
I love evade.#fyp#viral#evade#mobilegameplay #iloveevade, a+w+d evade24 março 2025
-
 Tumors exploit FTO-mediated regulation of glycolytic metabolism to evade immune surveillance - ScienceDirect24 março 2025
Tumors exploit FTO-mediated regulation of glycolytic metabolism to evade immune surveillance - ScienceDirect24 março 2025 -
 Hackers Using New Obfuscation Mechanisms to Evade Detection24 março 2025
Hackers Using New Obfuscation Mechanisms to Evade Detection24 março 2025 -
 Warning to Parents: Obscure Acronyms Like I.H.Y.D.M.A.W.S. Can Evade Apple's Anti-Sexting Technology24 março 2025
Warning to Parents: Obscure Acronyms Like I.H.Y.D.M.A.W.S. Can Evade Apple's Anti-Sexting Technology24 março 2025 -
Roblox Script - Evade, Roflux24 março 2025
-
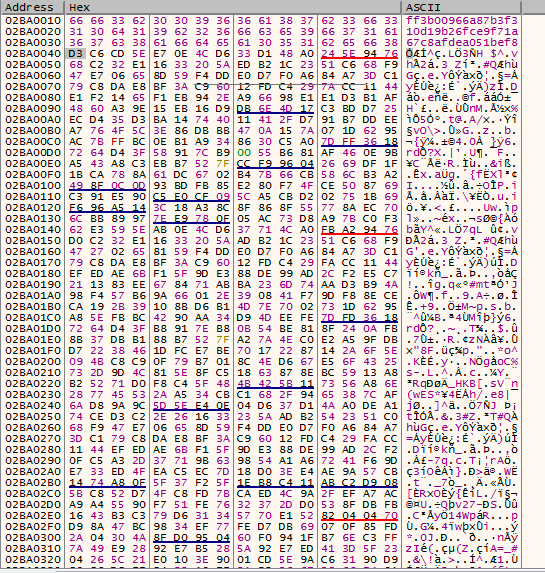 GuLoader – a highly effective and versatile malware that can evade detection24 março 2025
GuLoader – a highly effective and versatile malware that can evade detection24 março 2025 -
 New Python NodeStealer Goes Beyond Facebook Credentials, Now Stealing All Browser Cookies and Login Credentials - Netskope24 março 2025
New Python NodeStealer Goes Beyond Facebook Credentials, Now Stealing All Browser Cookies and Login Credentials - Netskope24 março 2025 -
 Cybercriminals are shapeshifting to evade security controls24 março 2025
Cybercriminals are shapeshifting to evade security controls24 março 2025 -
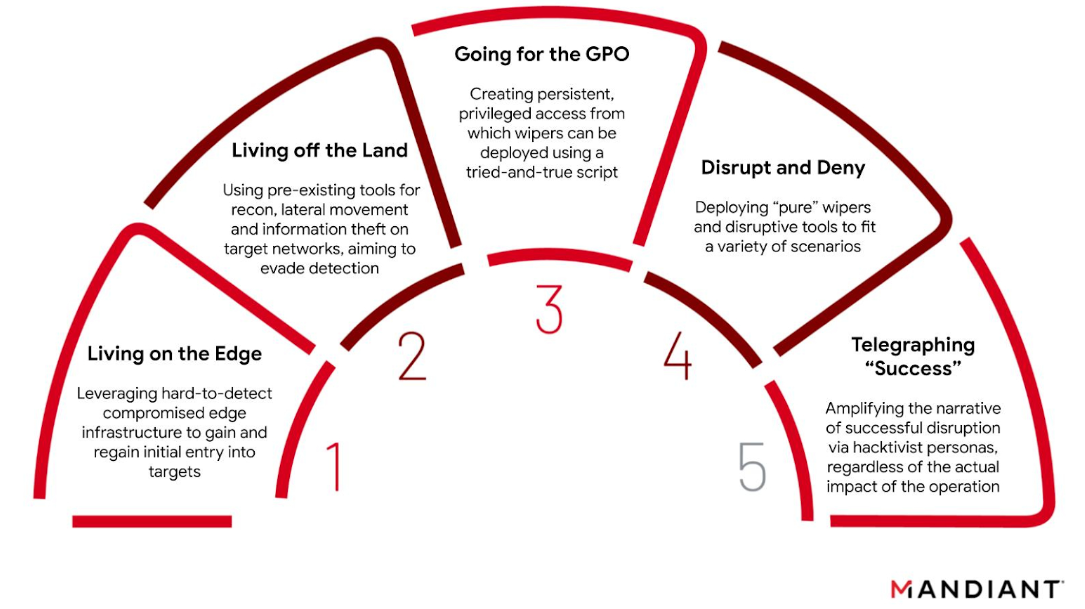 The GRU's Disruptive Playbook24 março 2025
The GRU's Disruptive Playbook24 março 2025 -
 ToddyCat: Keep calm and check logs24 março 2025
ToddyCat: Keep calm and check logs24 março 2025
você pode gostar
-
 Download do APK de Football 2024 League Clue para Android24 março 2025
Download do APK de Football 2024 League Clue para Android24 março 2025 -
Download Gorilla Tag Mod For Roblox on PC (Emulator) - LDPlayer24 março 2025
-
 Fundo de imagem Desenho Animado, Naruto, Desenhos Animados24 março 2025
Fundo de imagem Desenho Animado, Naruto, Desenhos Animados24 março 2025 -
 Crash Bandicoot - Smash Box Blind Box (Single Box) - Collectibles24 março 2025
Crash Bandicoot - Smash Box Blind Box (Single Box) - Collectibles24 março 2025 -
 Chess Board. Vector Drawing Stock Vector - Illustration of chessboard, business: 14118252324 março 2025
Chess Board. Vector Drawing Stock Vector - Illustration of chessboard, business: 14118252324 março 2025 -
 Ubisoft All Star Blast!_Free Online Games for PC & Mobile - hoopgame.net24 março 2025
Ubisoft All Star Blast!_Free Online Games for PC & Mobile - hoopgame.net24 março 2025 -
 Silent Hill 2 Mini Pyramid Head Plush (MADE TO ORDER!) - Silent-Neutral's Ko-fi Shop - Ko-fi ❤️ Where creators get support from fans through donations, memberships, shop sales and more! The original24 março 2025
Silent Hill 2 Mini Pyramid Head Plush (MADE TO ORDER!) - Silent-Neutral's Ko-fi Shop - Ko-fi ❤️ Where creators get support from fans through donations, memberships, shop sales and more! The original24 março 2025 -
 Restaurant to Another World Isekai Shokudou 2 Vol.1 Blu-ray Soundtrack CD Japan24 março 2025
Restaurant to Another World Isekai Shokudou 2 Vol.1 Blu-ray Soundtrack CD Japan24 março 2025 -
 Sneak Peek - Part 8 — RocketSnail24 março 2025
Sneak Peek - Part 8 — RocketSnail24 março 2025 -
Download Zombie Battle Simulator Free for Android - Zombie Battle24 março 2025

