Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 31 março 2025
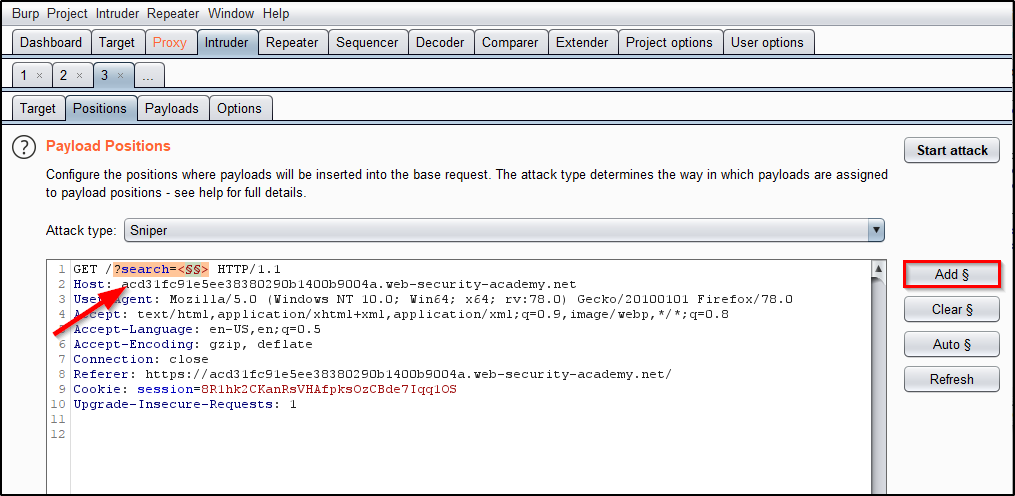
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

What is a Cross-site scripting attack? How to prevent XSS attack

Example code and XSS attacks

XSS‐immune: a Google chrome extension‐based XSS defensive framework for contemporary platforms of web applications - Gupta - 2016 - Security and Communication Networks - Wiley Online Library
Bypassing modern XSS mitigations with code-reuse attacks - Truesec
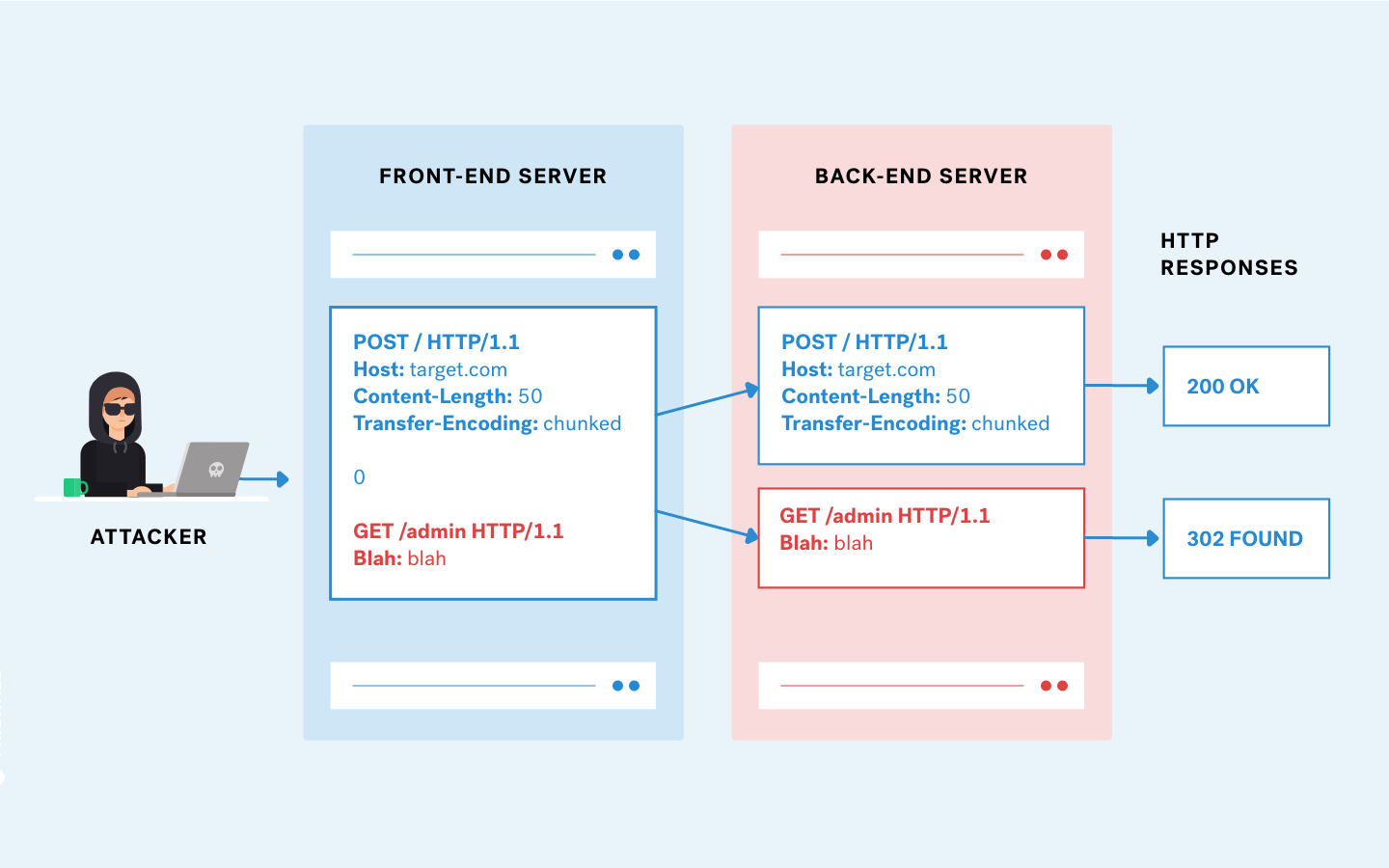
A Pentester's Guide to Cross-Site Scripting (XSS)

Bypassing Signature-Based XSS Filters: Modifying HTML - PortSwigger

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Understanding XSS Attacks
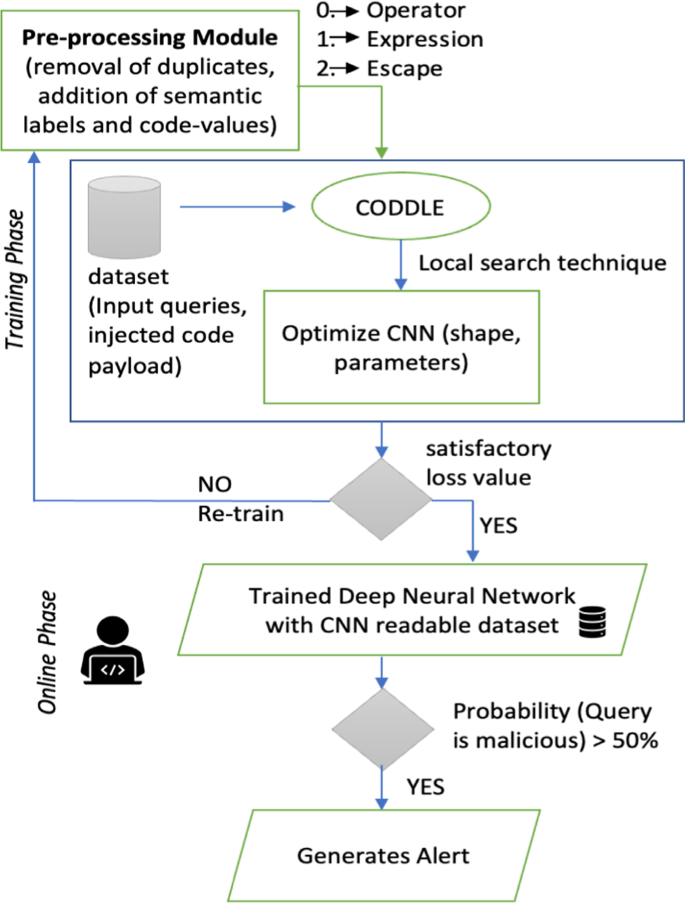
Detection of cross-site scripting (XSS) attacks using machine learning techniques: a review

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Recomendado para você
-
 What is a Cross-Site Scripting (XSS) attack: Definition & Examples31 março 2025
What is a Cross-Site Scripting (XSS) attack: Definition & Examples31 março 2025 -
XSS Cheat Sheet by Rodolfo Assis [Leanpub PDF/iPad/Kindle]31 março 2025
-
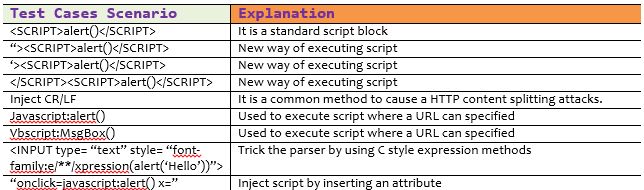 Net Penetration Testing: Cheat Sheet31 março 2025
Net Penetration Testing: Cheat Sheet31 março 2025 -
 XSS Prevention Cheat Sheet for Penetration Testers31 março 2025
XSS Prevention Cheat Sheet for Penetration Testers31 março 2025 -
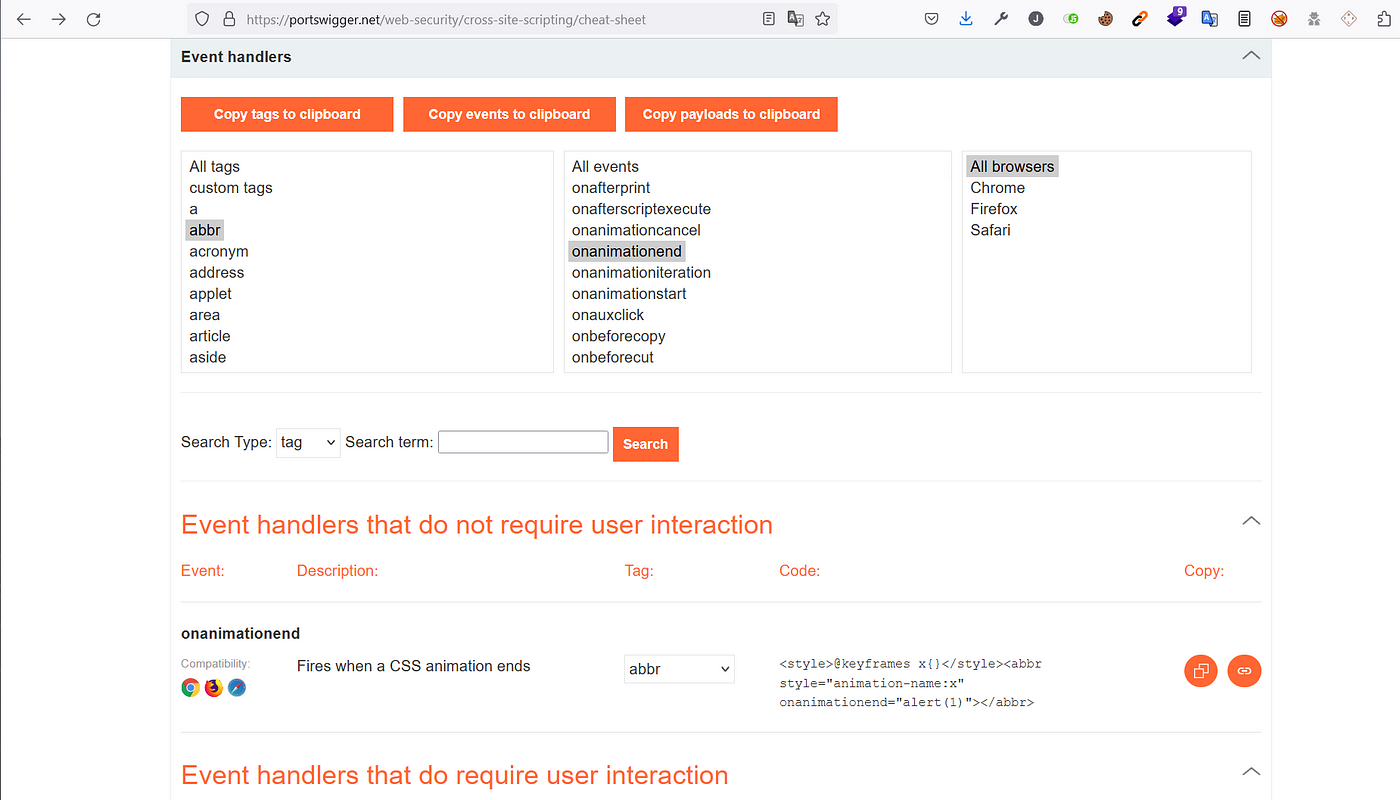 Reflected XSS on Target with tough WAF ( WAF Bypass ), by jowin92231 março 2025
Reflected XSS on Target with tough WAF ( WAF Bypass ), by jowin92231 março 2025 -
 Your Guide to Cross-Site Scripting (xss) Cheat Sheet - GuardRails31 março 2025
Your Guide to Cross-Site Scripting (xss) Cheat Sheet - GuardRails31 março 2025 -
 XSS Cheat Sheet31 março 2025
XSS Cheat Sheet31 março 2025 -
The XSS Rat - Uncle Rat ❤️ on X: #BugBountyTips i created this XSS cheat sheet for you guys <3 / X31 março 2025
-
 Bypassing Modern WAF's XSS Filters - Cheat Sheet - Miscellaneous Ramblings of a Cyber Security Researcher31 março 2025
Bypassing Modern WAF's XSS Filters - Cheat Sheet - Miscellaneous Ramblings of a Cyber Security Researcher31 março 2025 -
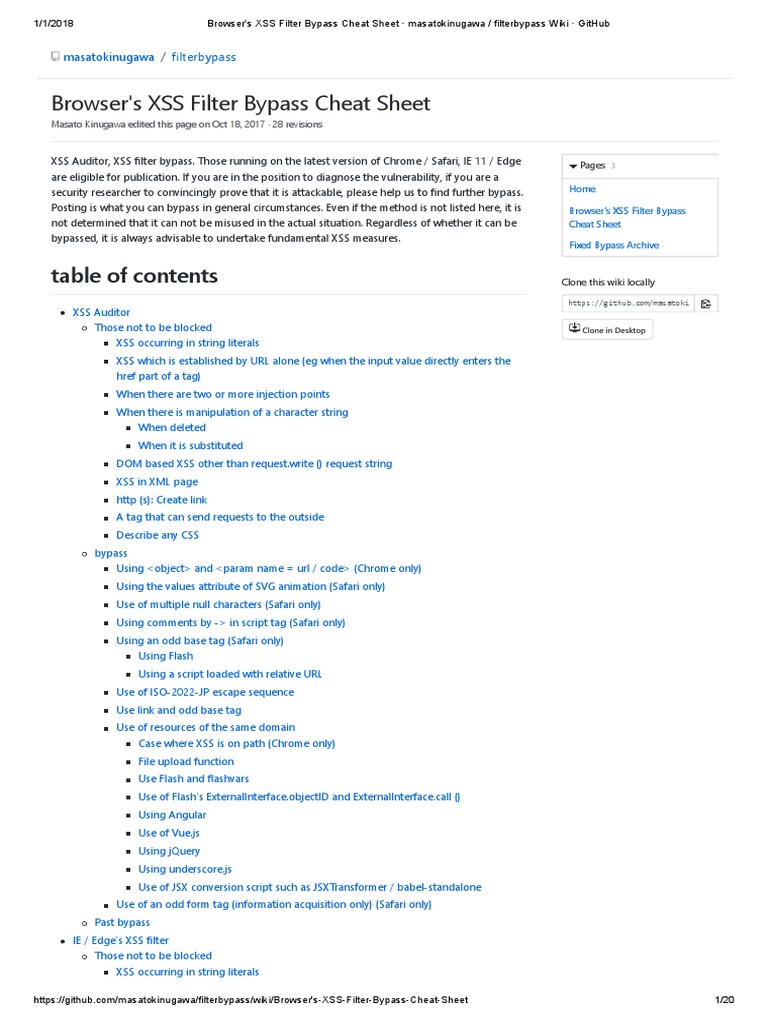
Browser's XSS Filter Bypass Cheat Sheet Masatokinugawa - Filterbypass Wiki GitHub, PDF, Html Element31 março 2025
você pode gostar
-
 Ex- Santos, Palmeiras e São Paulo, Wesley anuncia aposentadoria : r/futebol31 março 2025
Ex- Santos, Palmeiras e São Paulo, Wesley anuncia aposentadoria : r/futebol31 março 2025 -
 HD desktop wallpaper: Music, 5Xl Beats download free picture #56399331 março 2025
HD desktop wallpaper: Music, 5Xl Beats download free picture #56399331 março 2025 -
 Aí vem filler: My Hero Academia terá 3 personagens novos exclusivos do anime - NerdBunker31 março 2025
Aí vem filler: My Hero Academia terá 3 personagens novos exclusivos do anime - NerdBunker31 março 2025 -
 Used 2002 Suzuki Intruder 800 For Sale in Canyonville, OR - 5028009356 - Cycle Trader31 março 2025
Used 2002 Suzuki Intruder 800 For Sale in Canyonville, OR - 5028009356 - Cycle Trader31 março 2025 -
 Introducing Our New Studio Logo! - #50 by I_I - News & Alerts - Developer Forum31 março 2025
Introducing Our New Studio Logo! - #50 by I_I - News & Alerts - Developer Forum31 março 2025 -
Youjo Senki Episode 2 ENG Sub on Vimeo31 março 2025
-
 Movida e Rei do Mate estão entre as marcas com promoções31 março 2025
Movida e Rei do Mate estão entre as marcas com promoções31 março 2025 -
 XboxBR on X: Como já dizia Lara Croft: Nós criamos o nosso31 março 2025
XboxBR on X: Como já dizia Lara Croft: Nós criamos o nosso31 março 2025 -
/cdn.vox-cdn.com/uploads/chorus_asset/file/24373977/01_______IJM__09_CAP_0009_copy.jpg) Junji Ito Maniac review: a brief taste of horror in this Netflix anime31 março 2025
Junji Ito Maniac review: a brief taste of horror in this Netflix anime31 março 2025 -
![AmiAmi [Character & Hobby Shop] Bungo Stray Dogs Mini Acrylic](https://img.amiami.com/images/product/main/224/GOODS-04309994.jpg) AmiAmi [Character & Hobby Shop] Bungo Stray Dogs Mini Acrylic31 março 2025
AmiAmi [Character & Hobby Shop] Bungo Stray Dogs Mini Acrylic31 março 2025
![XSS Cheat Sheet by Rodolfo Assis [Leanpub PDF/iPad/Kindle]](https://d2sofvawe08yqg.cloudfront.net/xss/s_hero?1620563369)