Blog - Page 2 of 4 - Infosec
Por um escritor misterioso
Last updated 02 dezembro 2024
No blog da Infosec Security você encontra matérias relacionadas a vulnerabilidades em redes, aplicações Web, aplicativos mobile, ransomware, dentre outros.

10 Information Security Policies Organizations Should Implement

Cybersecurity vs. Information Security: Is There A Difference? (Yeah)

Enhance your Security and Privacy: Deploy your own WireGuard Servers, by Truvis Thornton, Sep, 2023

Top 5 Internal Data Security Threats and How to Deal with Them

Cyber Security Blog

Guide on creating enterprise security policy – Tresorit
Information Security Management System (Pre-configured ISMS) Solution
What is SOC 2 Compliance? Definition, Benefits & More, LogicGate

Blog - Page 2 of 107 - ProjectManager

Beth Barach

Unlock the world of Information Security Analyst: Salary, Must-Have Skills, and Beyond
0xor0ne on X: List of links to blog posts, write-ups and papers related to cybersecurity, reverse engineering and exploitation (constantly updated) #cybersecurity #infosec / X

Measure Your Organization's Cyber Secure Culture

The Top Cyber Security Blogs and Websites of 2023

Importance of Information Security Programs for Businesses
Recomendado para você
-
OLX - ogłoszenia lokalne - Apps on Google Play02 dezembro 2024
-
 Google smart lock issue in OLX app02 dezembro 2024
Google smart lock issue in OLX app02 dezembro 2024 -
 How to easily upload products from your store to OLX?02 dezembro 2024
How to easily upload products from your store to OLX?02 dezembro 2024 -
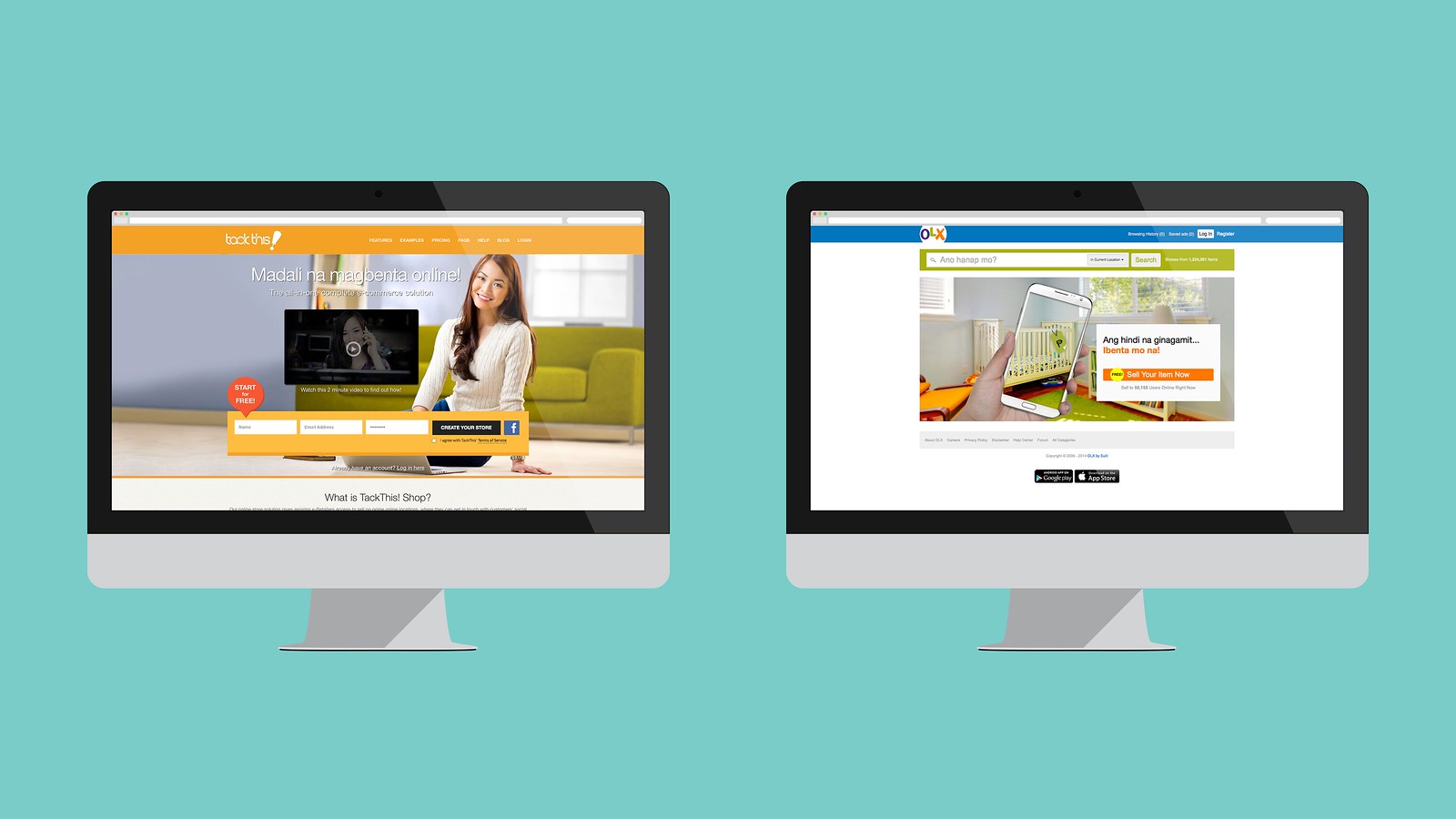 Garage Selling: OLX and Tackthis, designdrive.co/lab/though…02 dezembro 2024
Garage Selling: OLX and Tackthis, designdrive.co/lab/though…02 dezembro 2024 -
 OLX Autos (Dealers Only) on the App Store02 dezembro 2024
OLX Autos (Dealers Only) on the App Store02 dezembro 2024 -
 Brave browser not proceeding OLX.in after successful login via Google Account - Web Compatibility - Brave Community02 dezembro 2024
Brave browser not proceeding OLX.in after successful login via Google Account - Web Compatibility - Brave Community02 dezembro 2024 -
 Determining the Market Price of Old Vehicles Using Python02 dezembro 2024
Determining the Market Price of Old Vehicles Using Python02 dezembro 2024 -
About: OLX Champs NG (Google Play version)02 dezembro 2024
-
 Classified For Multipurpose App Buysell Classified like Olx, Mercari, Offerup, Carousell (1.3.1) by Panacea-Soft02 dezembro 2024
Classified For Multipurpose App Buysell Classified like Olx, Mercari, Offerup, Carousell (1.3.1) by Panacea-Soft02 dezembro 2024 -
 Olx and its working algorithm02 dezembro 2024
Olx and its working algorithm02 dezembro 2024
você pode gostar
-
 University of Birmingham & IIT-Madras launch joint Masters programmes02 dezembro 2024
University of Birmingham & IIT-Madras launch joint Masters programmes02 dezembro 2024 -
 Download Free Doll House Coloring Pages For Your Kids02 dezembro 2024
Download Free Doll House Coloring Pages For Your Kids02 dezembro 2024 -
Shadow form my version 🤗💞 - Claudia Pasquini02 dezembro 2024
-
 Palpite: Udinese x Juventus – Serie A– 20/8/2023 - Lance!02 dezembro 2024
Palpite: Udinese x Juventus – Serie A– 20/8/2023 - Lance!02 dezembro 2024 -
 Undertale Sans (fanart I made.) : r/Undertale02 dezembro 2024
Undertale Sans (fanart I made.) : r/Undertale02 dezembro 2024 -
 Top 5 Roblox Tycoons - (2022)02 dezembro 2024
Top 5 Roblox Tycoons - (2022)02 dezembro 2024 -
![Bully Anniversary Edition Steelbook | FantasyBox [N-Released]](http://ifantasybox.com/cdn/shop/products/Bully-Steelbook-FantasyBox.jpg?v=1651486812) Bully Anniversary Edition Steelbook | FantasyBox [N-Released]02 dezembro 2024
Bully Anniversary Edition Steelbook | FantasyBox [N-Released]02 dezembro 2024 -
 GTA sa Grand Theft Auto: San Andreas Apk for android Mod Money and Data for free Download on phone02 dezembro 2024
GTA sa Grand Theft Auto: San Andreas Apk for android Mod Money and Data for free Download on phone02 dezembro 2024 -
 Animes In Japan 🎃 on X: INFO Ilustração especial do mangá de Yahari Ore no Seishun Love Comedy wa Machigatteiru.: Monologue, de Rechi Kazuki, promovendo o volume 21 da série. /02 dezembro 2024
Animes In Japan 🎃 on X: INFO Ilustração especial do mangá de Yahari Ore no Seishun Love Comedy wa Machigatteiru.: Monologue, de Rechi Kazuki, promovendo o volume 21 da série. /02 dezembro 2024 -
 Dinossauros baby: 32 bichinhos super fofinhos para usar em suas decorações como faço, trabalhos manuais passo a passo, técnicas de criatividade, coisas legais …02 dezembro 2024
Dinossauros baby: 32 bichinhos super fofinhos para usar em suas decorações como faço, trabalhos manuais passo a passo, técnicas de criatividade, coisas legais …02 dezembro 2024

